The Business Service Administration subsystem consists of a table-driven server environment based in Natural. Typically, the Business Service Administration subsystem is used for three types of activities:
| Activity | Tasks |
|---|---|
| System administration |
|
| Security |
|
| Business service administration |
|
This section covers the following topics:
The Business Service Administration subsystem provides dynamic, online management of tables used by servers. All data required by the servers to start, stop, and perform requested functions is maintained here. The subsystem also provides mechanisms to enhance the functionality of EntireX, such as a security mechanism, service start-up and shutdown mechanisms, and messaging mechanisms. It is also used to expose some of the EntireX parameters through table-driven maintenance functions, including defining Broker service settings.
System administration involves the following tasks:
Defining servers
Servers, which include attach, dispatch, and security servers, interact with EntireX and the network to automate the communication between business service components on the client and on the server. The server definitions enable the servers to make themselves known to EntireX and to configure themselves for the environments in which they are expected to run.
Managing business service servers
Using the Business Service Administration subsystem, administrators can start, stop, and ping business service servers.
Viewing information logs
Logs maintained by the Business Service Administration subsystem contain updates to all system tables, information generated by running the business service servers, errors related to communication with the business service dispatch server, and security violations.
Another way of looking at the architecture of a business service is to view the Business Service Administration subsystem components that participate in directing requests from the client to the appropriate method on the server. The following diagram illustrates the relationships between these components:
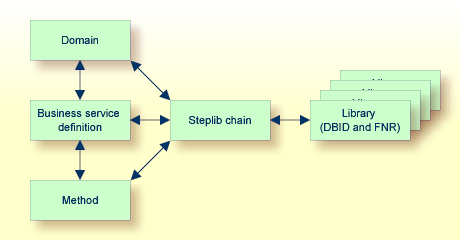
These components are:
| Component | Description |
|---|---|
| Steplib chain containing step libraries | Defines a set of
Natural libraries that a business service dispatch
server must access to call a subprogram proxy. The dispatch server accesses the
libraries in the order they are listed in the steplib definition.
Note: |
| Domain | Identifier used to group business services or define the boundaries of a business service. For example, all services in an Order Entry business service (such as Customer, Order, and Product) can share a single domain. |
| Business service definition and method | Groups a domain, business service, and version information under one identifier that describes the business service. This definition specifies all the methods of a business service, which subprogram proxies enable access to specific methods, and where the subprograms are located (steplibs). |
Application administrators and developers use the Business Service Administration subsystem to define steplibs and domains. Business service definitions are also stored in the subsystem, where they can be modified as needed.
The Business Service Administration subsystem is also used to define security settings that control user access to domains, business services, and methods.
First define the user IDs, then assign each user ID to one or more groups. Groups provide a mechanism for identifying users who need to access the same combination of domains, business services, and methods. Groups usually associate people who perform similar tasks. For example, an organization might have groups for Quality Assurance, Sales, and Management.
Note:
Users and groups can also be defined in Natural
Security, rather than Natural Business
Services security.
Once users and groups are defined in the Business Service Administration subsystem, security settings can be defined at multiple levels, as shown in the following table:
| Level | Description |
|---|---|
| Domain | When a group is granted access to a domain, its members can use all services and methods in the domain. |
| Service | Within domains, individual services can have security settings defined so users can only access selected services. |
| Method | Access privileges can also be explicitly granted or revoked for individual methods of a service. |
Because security data is located in the Business Service Administration subsystem, it can be maintained centrally. In addition, the subsystem includes a dynamically updated cache mechanism that improves throughput. When a business service dispatch server receives a request from the client, the Natural Business Services security server assigned to it verifies security privileges for the user. The security server builds a security cache when it first verifies the security for a given request. Thereafter, only one table lookup is required to verify the access privileges of a user to requested data, thereby improving response time after the initial request.
The contents of the security cache are always dynamic. If changes occur in the Business Service Administration subsystem data that affect security, the security cache is automatically updated. The security cache is maintained as a separate encrypted table in an external data source.