This section explains how to invoke the Business Service Administration subsystem and illustrates the menu structure. The following topics are covered:
Note:
For information on navigating menus, operating panels, and using
online help, direct commands, and PF-keys, see
What
is Natural Construct? in Natural Construct
Administration and Modeling.
The Business Service Administration subsystem resides in the SYSBIZ library.
 To invoke the Business Service Administration subsystem
To invoke the Business Service Administration subsystem
Log onto the SYSBIZ library at the More prompt.
Enter "Menu" at the Command prompt.
The Business Service Administration Subsystem main menu is displayed. For example:
BS__MAIN ***** Business Service Administration Subsystem ***** CDLAYMN1
Feb 14 - Main Menu - 08:47 PM
Functions
-------------------------------------------------
SA System Administration
AA Application Administration
? Help
. Terminate
-------------------------------------------------
Function .......... __
Command ........... _________________________________________________________
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
help retrn quit flip main |
The Business Service Administration subsystem is divided into System Administration and Application Administration functions. Each function has its own main menu, which leads to maintenance, query, and special functions. The following diagrams illustrate these menu structures.
Note:
If Natural Security is enabled, different
options are displayed on the System Administration menus. For information, see
Use Natural Security with
Natural Business Services.
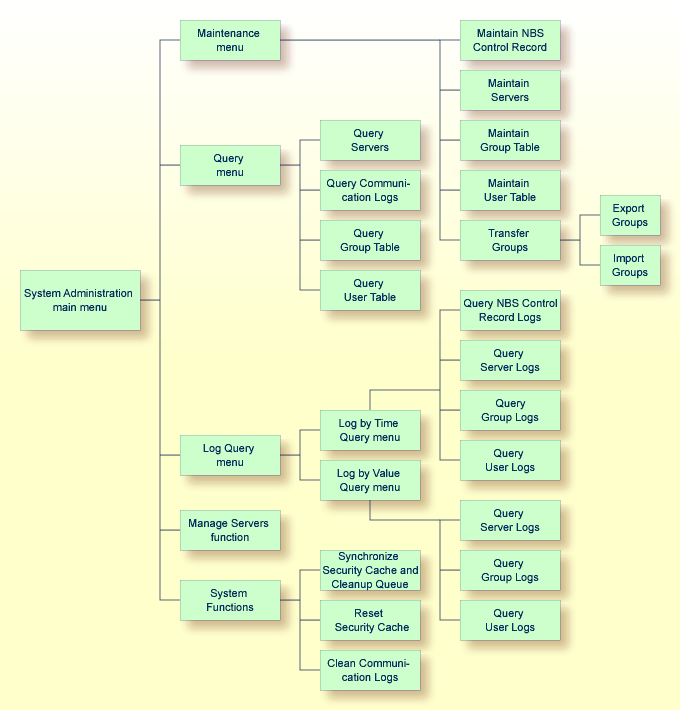
The following diagram shows the menu structure of the System Administration main menu:
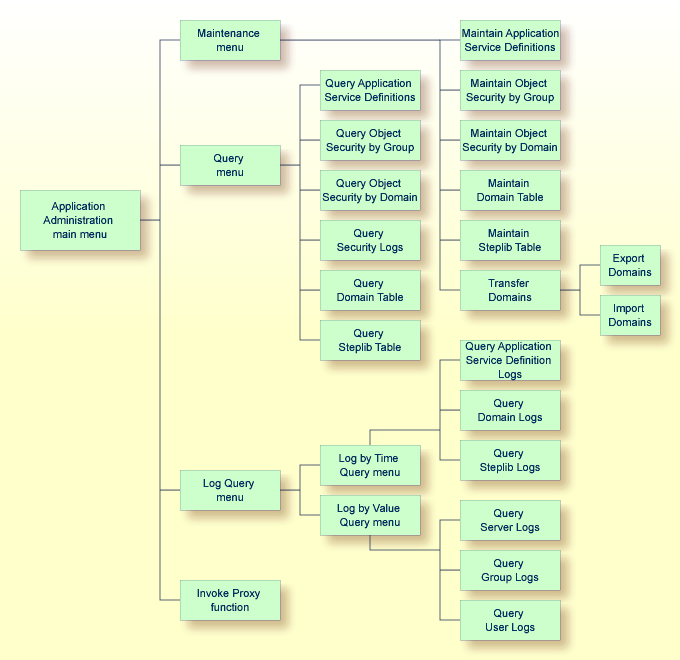
The following diagram shows the menu structure of the Application Administration main menu:
The Business Service Administration subsystem is fully integrated with Natural Security. If Natural Security is being used, all updates to group and user information are applied directly to Natural Security data. It is also possible to define user-library links. If Natural Security is not being used, the Business Service Administration subsystem manages users and their groups with its own set of security tables. The security data is always synchronized with any updates made to table data, whether the updates are made to data in the Business Service Administration subsystem or the Natural Security server.
Using Natural Security instead of Natural Business Services built-in security allows you to use security definitions that are already in place. There is no need to duplicate this information in the Business Service Administration subsystem files. This functionality is provided as an alternative for users without access to a Natural Security server.
Notes:
This section covers the following topics:
You can use Natural Security to maintain users and groups by configuring your Natural Security environment so that it informs Natural Business Services whenever changes are made to user or group tables. This ensures the integrity of data in Natural Business Services security cache. If a user is unlinked from a Natural Security group, all records associated with that user in the security cache are also deleted.
 To configure the Natural Security environment
To configure the Natural Security environment
Copy the NSCUSEX1 module from the SYSBIZ library into the SYSSEC library.
If you are already using the NSCUSEX1 exit in Natural Security, copy the sections of code identified in the NSCUSEX1 module supplied with Natural Business Services into your existing version of NSCUSEX1.
Use Natural Security to add SYSBIZ as a steplib to the SYSSEC library.
Catalog NSCUSEX1 in the SYSSEC library.
Modify your NATPARM to start Natural Security sessions to include the LFILE definitions required by Natural Business Services (LFILE 135 and 136).
When you are starting Natural Business
Services servers as a batch job under Natural
Security, refer to the guidelines supplied in the
Natural Security documentation. For example, use
STACK=(LOGON[library] [user-id] [pswd]) in the NATPARM settings
used to start the Natural session in the batch
job.
The user ID used to perform the Natural Security logon for batch jobs starting Natural Business Services must be linked to the SYSBIZ library. No other special privileges need be granted to the user.
 To allow Natural Business Services to communicate with Natural
Security
To allow Natural Business Services to communicate with Natural
Security
Invoke the Natural Security main menu.
Invoke the Administration Services main menu.
Invoke the General Options menu.
Set the Free access to functions via interface subprograms property to "True".
Natural Business Services uses the published Natural Security interface, NSC---L, to determine whether a user may use a library. The interface does not provide a means to specify a DBID and FNR with the library name. If a user is linked to a library through Natural Security on a given DBID or FNR, Natural Business Services cannot verify that the library it is accessing on behalf of the user is on the same DBID or FNR specified under Natural Security.
When you define steplib chains in the Business Service Administration subsystem, be sure to only specify libraries that are protected by Natural Security. When you specify a steplib with a DBID or FNR in Natural Business Services, define the library in Natural Security with the same DBID or FNR.
Note:
You cannot use the same name for libraries with different DBIDs or
FNRs.
When Natural Security is enabled, the options on the System Administration menus differ slightly. The following diagram shows the menu structure:
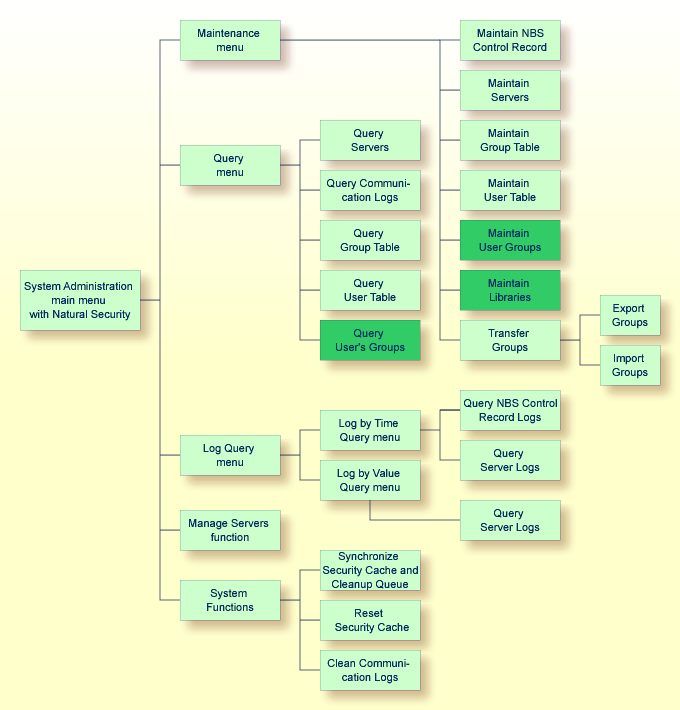
If you use Natural Security as your user and group management mechanism, the following changes are displayed in the System Administration menus:
System Administration Maintenance menu changes include:
Maintain User Table function invokes the Natural Security User Maintenance panel
Maintain Group Table function invokes the Natural Security Group Maintenance panel
Maintain User Groups function is available (see diagram)
This function allows you to associate users and groups.
Maintain Libraries function is available (see diagram)
This function allows you to define links between users and libraries.
System Administration Query menu changes include:
Query User Table function invokes a Natural Security User Information window
Query Group Table function invokes a Natural Security Group Information window
Query User Groups function is available (see diagram)
Queries for user and group log information (by time and value) are not available
Note:
This information only applies when using older applications and the
dispatch/security/attach servers. It does not apply to using the RPC
server.
If you use EntireX security to manage a security server (such as RACF, CA-TOP SECRET, or ACF2), you can use your established security system to authenticate users accessing business services. Natural Business Services supplies the SPSSAF module in the SYSBIZ library, which calls a Natural routine to perform authorization verifications based on service, domain, method, and user ID.
 To configure EntireX security for Natural Business Services
To configure EntireX security for Natural Business Services
Add a new resource class or type called "NBS".
Note:
If you call it something other than NBS, you must change the
reference to the class or type in SPSSAF.
Create resource profiles for each domain/service/method combination
used in the application using the format:
domain.service.method.
Ensure that the number of characters specified in resource profiles does not exceed 32. Do not use special characters in your resources.
Add the resource profiles to the resource class or type.
Set up your business service dispatch server to use the SAF security mode.
Notes:
Tip:
If you modify the resource profile after the business service is in
use, reset the business service security cache (to clear previous permissions
from memory). For information, see Reset the Security
Cache.
Note:
This information only applies when using older applications and the
dispatch/security/attach servers. It does not apply to using the RPC
server.
Natural Business Services also supports a hybrid security server. For example, you can use EntireX security for user authentication (mainframe access rights) and perform validations against FSEC (Natural library and domain/service/method authorization) or Natural Business Services security. The business service control record definition determines which security server is used.
 To use a hybrid security server with a dispatch server
To use a hybrid security server with a dispatch server
Display the second Maintain Servers panel for the dispatch server.
For information, see Access the Maintain Servers Panels.
Enter one of the following settings for SECURITY-MODE in the Server Start Parameters section:
| Setting | Description |
|---|---|
| SAF-NSC (for validations against FSEC) | The dispatch server verifies business service rights defined in the Natural Security file. |
| SAF-APPL (for Natural Business Services security) | The dispatch server verifies business service rights defined in the Natural Business Services security file. |
In both cases, the dispatch server uses SAF/EXX security for user ID and password authentication.
Notes: