This document covers the following topics:
The Terminal Emulation Key Scheme dialog box lets you define the keys to be used for a specific key scheme. This dialog box appears when you manage a key scheme in the Configuration Manager, set up a key scheme in the session properties, or when you add, modify or duplicate a key scheme in the terminal application.
Using the button, you can hide the keyboard in the lower part of the dialog box. The name of the command button then changes to .
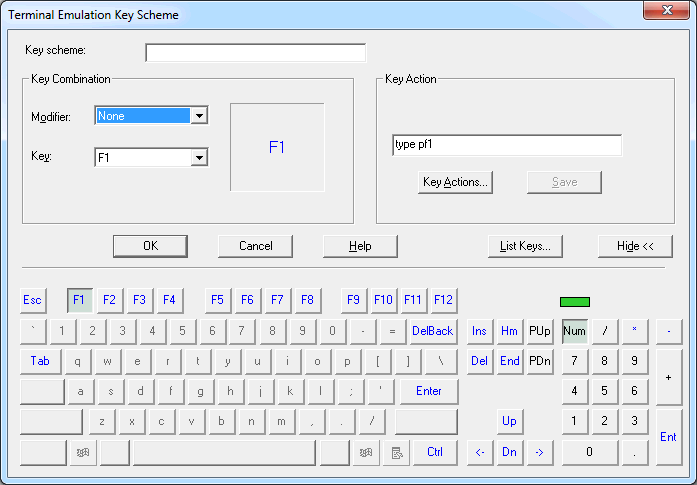
The layout of the keyboard in the lower part of the dialog box depends on the language that is currently defined in your user properties. This can be English or German.
Different colors are used for the key names that are shown in the lower part of the dialog box:
| Color | Meaning |
|---|---|
| Black | A key action has not yet been assigned. |
| Blue | A key action has already been assigned. To view the action, select the key and then use the different options in the Modifier drop-down list box. When an action has been assigned for a specific modifier, the corresponding values are shown in the Key Action group box. When you move the mouse over a blue key name and when a key action has been defined for the currently selected modifier, the defined key action is shown in a tooltip. |
| Gray (dimmed) | The key is disabled. Therefore, a key action cannot be assigned. Whether a key is disabled or not depends on the currently selected option button in the Modifier drop-down list box. |
Notes:
 To modify the key scheme
To modify the key scheme
When you add a new key scheme, specify its name in the Key scheme text box. The key scheme name can be up to 32 characters long and may contain blanks.
Select one of the following options from the Modifier drop-down list box:
None
The selected key is not used in combination with any other
key.
Shift
The selected key is to be used in combination with the
SHIFT key.
Ctrl
The selected key is to be used in combination with the
CTRL key.
Alt
The selected key is to be used in combination with the
ALT key.
Depending on the currently selected key, it may be possible that not all options are shown in the Modifier drop-down list box. When you deselect the key, all options are available again.
In the lower part of the dialog box, select the key that is to be defined. Disabled keys cannot be selected.
If an action has already been defined for the selected key or key combination, this action is shown in the Key Action group box. An action represents, for example, a key or string to be sent to the host. You can define several actions for each key combination. Thus you can define, for example, a logon sequence consisting of several steps that are executed by pressing a single key.
When a German keyboard is shown and you select a special character which is not available on the English keyboard or which has a different position on the English keyboard, the corresponding character from the English keyboard, at that position, is used. For example, when a German keyboard is shown and you select "ü", the Key drop-down list box shows you that "[" has been selected.
Or:
Select the desired key from the Key
drop-down list box. Using this drop-down list box, it is possible to select
non-standard PC keys which are only available on special keyboards (for
example, F13 through F24).
The name of the selected key is now shown in the Key Combination group box. For example:

In the Key Action group box, enter the command that is to be performed. For example:
| Command | Description |
|---|---|
EXECTASK
DSYSTRANS |
Executes the task
DSYSTRANS.
|
EXECUTE LOGOFF |
Executes the procedure file Logoff.ncp. |
TYPE 'SAAAA'
CR |
Sends the characters
SAAAA and CR (ENTER) to the host.
|
Or:
Choose the button to
specify the action using a dialog box. For further information, see
Selecting a Key
Action.
To save the key action which is currently shown in the Key Action group box, choose the button.
Notes:
When you have defined all required keys, choose the button.
The dialog box is closed.
The following dialog box appears when you choose the button in the Terminal Emulation Key Scheme dialog box which is described above.
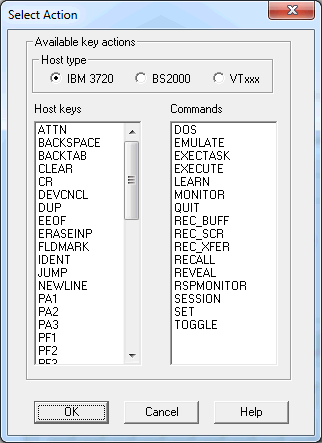
 To select a key action
To select a key action
Select the appropriate host type.
The host keys which are shown when the IBM 3720 option button is selected also apply for BS2000 and VTxxx hosts. When you select the BS2000 or VTxxx option button, additional host keys are shown which only apply to this host type.
Select either a host key or a command.
Choose the button.
When you have selected a host key, the TYPE
command is written to the Key Action group box, together
with the selected host key. See also
Terminal Function
Keys.
When you have selected a command, this command is written to the Key Action group box. You then have to specify all required parameters manually.
Invoke the dialog box repeatedly until the Key Action group box contains all required actions.
The following dialog box appears when you choose the button in the Terminal Emulation Key Scheme dialog box which is described above or in the Key Scheme Selection dialog box which is available in the terminal application. It lists the defined keys for the currently selected key scheme.
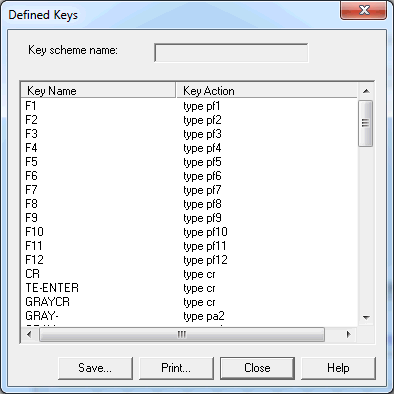
You can write the key actions for the currently shown key scheme to a file or you can directly print them.
 To write the key actions to a file
To write the key actions to a file
In the Defined Keys dialog box, choose the button.
The Save As dialog box appears.
Select the desired location and specify a file name.
The default extension is txt.
Choose the button.
 To print the key actions
To print the key actions
In the Defined Keys dialog box, choose the button.
The Print dialog box appears. You can print the key actions on a printer defined under Windows.
Choose the button.
A distinction is made between terminal function keys and physical function keys:
This terms refers to all keys that start a terminal function. Different host systems have different terminal functions and associated keys. Examples for IBM 3270 hosts: PF1, PF2, ATTN, PA1. Examples for BS2000 hosts: F1, K1, FKT1, DUE1.
The code sequence eventually sent to the host for a given terminal function key is taken from the terminal function code table. The share file contains terminal function code tables for all communication methods. The administrator can modify the terminal function code tables.
This terms refers to all keys on the physical keyboard that can be used as function keys. Examples: F1, F2, CTRL+F3, CTRL+A, ALT+B. Entire Connection has a unique name for each function key.
Some terminal function key names are found on all host systems, others are specific to a given host system. Entire Connection supports the following:
The following key names can be used with the
TYPE command to transmit the corresponding 3270 key
to the host:
| ATTN | DOWN | LEFT | RIGHT |
| BACKSPACE | EEOF | NEWLINE | SYSREQ |
| BACKTAB | ERASEINP | PA1 to PA3 | TAB |
| CLEAR | HOME | PF1 to PF24 | TEST |
| CR | IDENT | POR | UP |
| DELETE | INSERT | ||
| DEVCNCL | JUMP | RESET |
If any of the following key names is used with the
TYPE command, Entire Connection will automatically
wait for a response from the host before continuing:
ATTN
CLEAR
CR
POR
PA1 to PA3
PF1 to PF24
The following key names can be used with the
TYPE command to transmit the corresponding 9750 key
to the BS2000 host:
| AFG | FKT1 to FKT24 | P1 to P20 | SMU |
| AFZ | K1 to K14 | RU | SNZ |
| DUE1 | LSP | SBA | SZA |
| DUE2 | LVD | SDZ | TABL |
| EFG | LZE | SML | TABR |
| EFZ | LZF | SMO | |
| ENDM | MAR | SMR |
The following key names can be used with the
TYPE command to transmit the corresponding VT-type
key to the host:
| AKEY1 to AKEY15 |
^A to ^Z (where
^ stands for CTRL)
|
Physical function keys are all keys and key combinations that can be used as function keys by Entire Connection. In the Terminal Emulation Key Scheme dialog box, you can assign the following to a function key:
a command
a command string
an emulation key
a combination of the above possibilities.
When the function key is pressed, the assigned action is executed.
All physical function keys have symbolic names in
Entire Connection. These symbolic names are displayed in the
Key drop-down list box in the Terminal Emulation
Key Scheme dialog box and can be used with the commands
TYPE and SET TEKEY in a
procedure file.
Note that the Key drop-down list box in the Terminal Emulation Key Scheme dialog box contains more symbolic names than illustrated in the tables below (for example, "XF1"). These symbols can be used with keyboard types that have more keys. See the file Keyboard_us.kyb in the tables folder of Entire Connection for details.
The following table lists the Entire Connection physical function keys and indicates the combinations in which these keys can be used.
| Key | single key | SHIFT | CTRL | ALT |
|---|---|---|---|---|
| A through Z | X | X | ||
| BACKTAB | X | |||
| BKSPC | X | X | ||
| CENTER | X | X | ||
| CR | X | X | X | |
| DELBACK | X | |||
| DELETE | X | X | ||
| DOWN | X | X | ||
| END | X | X | ||
| ESC | X | X | ||
| F1 to F12 | X | X | X | X |
| HOME | X | X | ||
| INSERT | X | X | ||
| LEFT | X | X | ||
| PGDN | X | X | ||
| PGUP | X | X | ||
| PRTSC | X | |||
| RIGHT | X | X | ||
| TAB | X | X | ||
| UP | X | X | ||
| 0 to 9 | X | |||
| 2 and 6 | X | |||
| n-0 to n-. | X | |||
| GRAY * | X | X | X | |
| GRAY / | X | X | X | |
| \ | X | X | ||
| [ | X | X | ||
| ] | X | X | ||
| - | X | X | ||
| GRAY - | X | X | X | |
| = | X | |||
| GRAY + | X | X | ||
| ; | X | |||
| , | X | |||
| . | X | |||
| QUOTE | X |
Note:
The names n-0 to n-. represent the keys
on the numeric keypad. You can also transmit these keys by pressing
NUM.
Additional key support for IBM 101 enhanced keyboards:
| Key | single key | SHIFT | CTRL | ALT |
|---|---|---|---|---|
| DELETE (gray) | X | |||
| DOWN (gray) | X | |||
| END (gray) | X | |||
| HOME (gray) | X | |||
| INSERT (gray) | X | |||
| LEFT (gray) | X | |||
| PGDN (gray) | X | |||
| PGUP (gray) | X | |||
| RIGHT (gray) | X | |||
| UP (gray) | X |
When you press a function key, the following occurs:
Entire Connection takes the keyboard code received from the Windows operating system and scans the physical keyboard table for the name of the physical function key.
If the name of the physical function key is found, Entire Connection checks the keys that have been defined for terminal emulation. If the function key is not assigned, the key is passed to Windows for further processing. If the function key is assigned, the key action is passed to the communication modules.
The communication modules parse the key action. The key action may consist of several elements, including the name of a terminal function. For example:
TYPE 'username' CR
If the key action contains the name of a terminal function
(CR in the above example), Entire Connection scans the current
terminal
function code table for the code sequence of this terminal function,
and passes the code to the host.