Adabas uses the concept of Role-Based Access Control (RBAC) to implement Authorization for Adabas Utilities.
You can restrict the scope of your security definitions to a database (mode ADABAS) or to the machine with all installed databases (mode INI).
For more detailed information, please refer to Authorization for Adabas Utilities (Mode ADABAS) or Authorization for Adabas Utilities (Mode INI).
This document covers the following:
Authorization provides a means of restricting the usage of Adabas utilities on databases by assigning users a role which represents selective access privileges
The user is identified by the credentials, which were used to access the local machine.
The Adabas utilities check the provided credentials against the security definitions in the security repository. The security repository depends on the mode that is chosen during configuration. For further details, please refer to Configuration.
If the credentials have been assigned a role, the access privileges for the requested operation on the database are determined. If the access privileges are sufficient the user is allowed to execute the utility on the database. If the access privileges are insufficient or lacking, authorization fails and the utility usage is denied.
The security repository stores granted privileges, denial of specific operations is not supported.
The audit trail logs both successful and failed attempts to use an Adabas utility.
In the current version:
Adabas utilities do not perform authentication checks.
Supported credentials are the local system credentials.
Authorization implies "usage or no usage" of the utility and the database on which the operation was to be performed.
The audit trail is written to the log file, which can be configured.
The authorization feature is only available in the following Adabas utilities: ADABCK, ADADBM, ADAELA,ADAFDU, ADAFRM,ADAOPR, ADAORD, ADARBA,ADAREC, ADAREP, ADASCR and ADAULD.
Adabas Role-Based Access Control restricts database access to users based on their roles
Permissions to perform specific Adabas utilities are granted to roles, and users are authorized to execute Adabas utilities through their assigned roles.
Adabas RBAC knows the object types Users, Roles, Actions and Resources. Assignments and Privileges describe the relations between these entities.
- User
The user name.
- Role
The role name groups access rights.
- Action
The Adabas utility.
- Resource
The database ID. The current database is denoted as DBID.CURRENT.
- Assignment
A user can have multiple roles.
A role can be assigned to multiple users.
- Privilege
A role can have multiple permissions.
A specific permission can be assigned to multiple roles.
The security library validates an Adabas utility’s access request against the access privileges defined in the security repository.
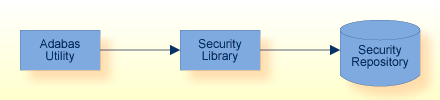
Authentication for Adabas Utilities uses the login credentials to authenticate a user:
Unix: User ID
Windows: Domain and user ID
Authorization for Adabas Utilities uses RBAC security definitions to authorize a requested operation on a specified database.
The security library validates the access request against the access privileges defined in the security repository.
If a matching access privilege is found, the Adabas Utility is authorized to perform the requested operation, otherwise the request is rejected.
The installation of the required components and configuration files is mandatory.
The security infrastructure is required by the Adabas utilities.
An initial security configuration is created during the installation; e.g.
The Audit Trail is pre-configured.
A minimal set of not restrictive role-based security definitions is installed.
Authorization is not active.
This section describes how to configure the authorization feature.
The configuration of Authorization for Adabas Utilities is stored in the following files:
| Configuration File | Description |
|---|---|
adaauth.ini |
Configuration of Authorization for Adabas Utilities |
adaaudit.ini |
Configuration of Audit Trail |
adarbac.ini |
Role-Based Access Control Definitions (MODE=INI) |
These files configure the local machine and apply to all databases, to all product installations and product versions that are greater than or equal to Adabas Version 6.5 on the machine.
The configuration files are ASCII files and can be edited with a standard text editor. Access to these file should be restricted. Please refer to the section Security Considerations, which describes how to secure (“harden”) the database.
The location of the configuration files is platform-dependent and is described in the section Configuration of Authorization for Adabas Utilities of the Extended Operation documentation.
The adaauth.ini configuration file contains information, which applies to the machine and to all databases, to all product installations and product versions that are greater than or equal to Version 6.5 on the machine.
| Section | Item | Description |
|---|---|---|
AUTHZ |
AUDIT_FILE |
Location of Audit Trail configuration file |
RBAC_FILE |
Location of security definitions (MODE=INI) | |
ACTION |
Enable the Authorization for Adabas Utilities feature | |
MODE |
Define the source of the security definitions |
Note:
Currently, this file enables or disables the Authorization for
Adabas Utilities feature. The default setting is
"disabled" (ACTION = NO). This setting
may be removed or changed in later product versions.
For further information on the syntax of this file, see the descriptions of adaauth.ini in the Extended Operation documentation.
The adaaudit.ini configuration file defines the layout and location of the Audit Trail.
| Section | Item | Description |
|---|---|---|
AUDIT |
LOG_FILE |
Location of Audit Trail log file |
FORMAT |
Determines the layout of the log file Entry
|
|
SEPARATOR |
The separator used in CSV layout |
Requirements on the Audit Trail log file:
The Audit Entries are appended to the log file.
Thus, users of Adabas utilities require WRITE access to the log file.
The size of the log file should be monitored and backed-up or moved as need be.
Note:
It is mandatory that all users, who are authorized to execute an
Adabas utility, have READ/WRITE access permissions to both the LOG_FILE and the
directory in which it is located.
For further information on the syntax of this file, see the descriptions of adaaudit.ini in the Extended Operation documentation.
This feature has minimal impact on the overall system performance.
If MODE=ADABAS is defined in the adaauth.ini configuration file, the accessed Adabas database is the source of the security definitions.
The Adabas database contains a specific system file, the RBAC system file that stores the security definitions. When it is created, a basic set of initial definitions is loaded. These security definitions can be adapted and extended to the application’s needs.
The advantage of this mode is that each authorization request is decided locally, hence performance impact is minimalized.
This approach supports authorization for utilities that access offline and online databases.
In mode ADABAS, the initial security definitions implement unrestricted access to all Adabas utilities.
Initially, the RBAC system file defines user PUBLIC and role PUBLIC with role PUBLIC assigned to user PUBLIC. The role PUBLIC has the privilege to execute all Adabas utilities.
Any user who is not yet known to the security repository is treated as user PUBLIC to ensure unrestricted access as in previous Adabas versions.
The utilities required to configure and administer the Authorization feature are:
ADADBM - Create the RBAC system file
ADAREP - Query the RBAC system file
ADARBA - Administer the RBAC system file
Use the RBAC_FILE function of ADADBM to create the RBAC system file.
Note:
The RBAC_FILE function requires that the database is offline.
Use the SUMMARY function of ADAREP to display the database system files.
Note:
The RBAC system file is only displayed if the RBAC file is defined.
It is not displayed if the file is not loaded.
Use the functions of ADARBA to create, read, update and delete security definitions.
Note:
ADARBA requires that the database is online.
In Authorization mode INI, the security definitions apply to the machine and to all databases, and to all product installations and product versions that are greater than or equal to Version 6.5 on the machine.
The adarbac.ini configuration file defines roles and assigns permissions to execute sets of operations on one or more objects. Below is an overview of the relationships between the entries in the file:
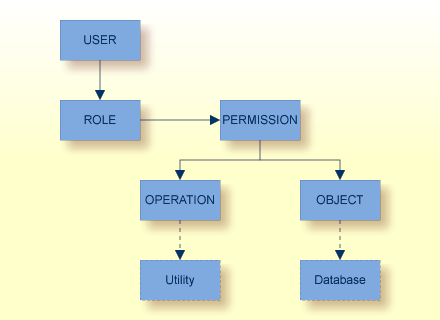
| Section | Item | Description |
|---|---|---|
USER_ROLE |
user_name |
User/Role assignment |
ROLE_PERMISSION |
role_name |
Role/Permission assignment |
PERMISSIONS |
permission_name |
Operation/Object assignment |
OBJECTS |
object_name |
Assignment of database ID |
OPERATIONS |
operation_name |
Assignment of utility |
For further information on the syntax of this file, see the descriptions of adarbac.ini in the Extended Operation documentation.
This Getting Started documentation covers the following topics:
Authorization for Adabas Utilities requires the security infrastructure. An initial security configuration is set up during installation, the Audit Trail is pre-configured, and Authorization is not active.
Adabas authorization uses your login credentials. This is the user ID on Unix platforms, and the domain and user ID on Windows platforms.
The Adabas utility ADARBA is used to maintain your RBAC security definitions, to create or drop user and role definitions, and to grant or revoke assignments and privileges.
This section describes how to configure Authorization for Adabas Utilities to use the RBAC security definitions that are stored in the Adabas RBAC system file.
 To configure Authorization for Adabas Utilities
To configure Authorization for Adabas Utilities
Set the following in the security configuration file adaauth.ini, section [AUTHZ]:
ACTION=YES - to enable Adabas Authorization
MODE=ADABAS - to use the authorization mode ADABAS
The setting RBAC_FILE is not used for this configuration.
The setting AUDIT_FILE can be left unchanged for the purpose of this Getting Started.
Create a demo database:
crdemodb 100
Query the database information:
adarep dbid=100 summary
At this point, you are authorized to execute the Adabas utility ADAREP, even though MODE=ADABAS is set, because an RBAC system file has not yet been defined.
Create the RBAC system file and load the initial security definitions:
adadbm db=100 rbac_file=<any_file_number>
At this point, you are authorized to execute the Adabas utility ADAREP because the RBAC system file has been defined and the initial definitions have been loaded.
Start the database, and then display the initial security definitions (the administration of RBAC definitions is only supported if the database is online):
adarba db=100 list users
shows the inital user PUBLIC.
adarba db=100 list roles
shows the inital role PUBLIC.
adarba db=100 list assignments
shows the inital assignment PUBLIC,PUBLIC.
By default, the user PUBLIC is granted the role PUBLIC, and therefore has all of the privileges that are granted to the role PUBLIC.
With the initial set of RBAC security data, your login user ID is authorized to execute the security-enabled Adabas utilities because, by default, a user who is not known to the RBAC system is authorized as the user PUBLIC with the role PUBLIC.
In the next steps, you will restrict the privileges for your current login ID
 To restrict the privileges for your current login ID
To restrict the privileges for your current login ID
Create a new user:
adarba db=100 create user=my-login-user
where my-login-user is your current user ID.
Create a new role:
adarba db=100 create role=newrole
Grant the new role to the new user:
adarba db=100 grant assignment role=newrole user= my-login-user
Check the assignments:
adarba db=100 list assignments
now shows
PUBLIC,PUBLIC (the initial assignment)
PUBLIC,my-login-user (default assignment for a new user)
newrole,my-login-user (the new assignment)
Grant a restricted privilege to the new role:
adarba db=100 grant privilege action=ada.uti.rba role=newrole
Check the privileges:
adarba db=100 list privileges
shows
all default privileges
ada.uti.rba,DBID.CURRENT,newrole
Because the user my-login-user has the roles PUBLIC and newrole, you are still authorized to do everything.
Restrict the access privilege of the user my-login-user to ADARBA:
adarba db=100 revoke assignment role=PUBLIC user= my-login-user
Now try to execute an Adabas utility other than ADARBA:
adarep db=200 sum
This will return ‘Security violation. Permission denied.’
If you want to adapt or restore your access privileges, you can still use ADARBA to define them according to your needs, e.g.
adarba db=100 grant privilege action=ada.uti.rep role=newrole
or
adarba db=100 grant assignment role=PUBLIC user= my-login-user