The Integrated Authentication Framework (IAF) is a token-based infrastructure that enables Software AG's enterprise single sign-on. In addition, it allows usage of a configurable authentication system (user database) with Software AG products across platforms. IAF is part of the Software AG Security Infrastructure.
This document covers the following topics:
See also Integrated Authentication Framework (IAF) under Shared Components - Security Infrastructure on the Software AG Product Documentation website.
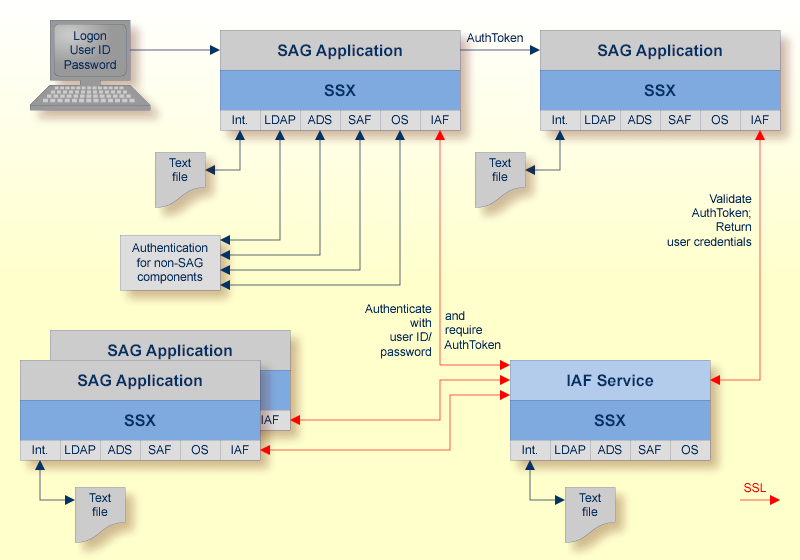
The architecture of IAF defines a central service (the IAF service) that is contacted by multiple clients in order to:
authenticate a user
create a unique and fraud resistant token
validate tokens
pass information about the token and the authenticated user to the owner of the token
More and more Software AG products will be equipped with the IAF client-side modules. These will be configured through the configuration process of the application itself. Mainly, the application must know the "address" of the IAF server. Under UNIX and Windows the IAF server can be started and stopped using a System Management Hub agent. Under z/OS it runs as a started task and can be started and stopped via operator commands.
The IAF server is configured using an attribute file, where you can define parameters that influence the scalability (multiple parallel threads) and internal cache sizes (max. buffers) of the server.
The main functionality of an IAF server is also configured using the attribute file. You have to select an existing user repository (such as a RACF database or a Windows Active Directory) that is triggered with authentication requests.
No license file is required, since IAF is a common infrastructure that can only be used by Software AG products.
The access module for the IAF server is called SSX [Software AG Security eXtension]. SSX is a shared library that offers authentication for a variety of different user repositories. The number of repositories depends on the platform.
All SSX implementations offer authentication type "IAF". The
serverHost parameter is then a Broker ID that points to
a running IAF server.
For EntireX, the notation of an IAF server is as follows:
iaf://<IAF-server-machine-IP-address>:<port>?<sslparms>
Calling IAF for authentication serves two purposes:
The authentication is performed by a remote server, i.e. can reach out to user repositories that may not be available on the local machine.
IAF creates a unique and secure token for each successful user authentication. The server returns this token to the client process, where it can be included in the message flow. The advantages are:
The user ID is not readable because the token is encrypted.
The token cannot be changed (e.g. the UserId cannot be altered) on transit because it is signed.
The token guarantees to the receiver that a user has successfully signed in to a user repository. Using an SSX library and the connection to the IAF server makes it possible to reveal the user name and some more statistical data about the authentication process.
IAF has been added as an authentication method to the Broker.
In the DEFAULTS=BROKER section of the broker attribute
file, specify
SECURITY = YES
In the DEFAULTS=SECURITY section, specify the address of
the IAF service:
AUTHENTICATION-TYPE="iaf://<server-name>:<server-port>?<ssl-parms>" SECURITY-LEVEL=AUTHENTICATION
At the moment, IAF on the mainframe is not capable of performing
authorization calls against RACF resource definitions. As the default
SECURITY-LEVEL on the mainframe sets both authentication and authorization, it
must be explicitly restricted to
SECURITY-LEVEL=AUTHENTICATION.
See Security-specific Attributes under Broker Attributes.