Connecting Integration Server in Green Zone to API Gateway in DMZ
In this scenario, you can configure threat protection, authentication, authorization, and mediation rules in the API Gateway instance present in DMZ.
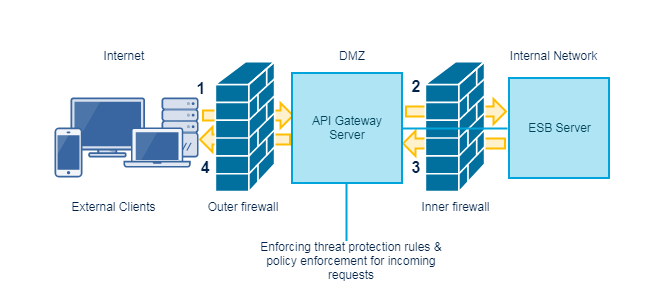
The following image describes the working method. The client requests are sent to the API Gateway in DMZ. These requests are present on the registration port. The Integration Server in green zone listens to the registration port through the internal port, processes the requests, and responds back to the API Gateway instance in DMZ. The API Gateway instance in DMZ responds to the external clients.
Important:
A connection between API Gateway Server in DMZ and the API Gateway Server in Green zone is available except when a request is being made to the API Gateway in green zone or a response is being returned from the API Gateway in green zone. In other words, DMZ API Gateway connection utilization is I/O bound. Therefore, if you expect large, simultaneous transactions, increase the number of registered connections accordingly.

To configure reverse invoke
1. Configure External and Registration ports on API Gateway in DMZ.
a. Log on to API Gateway as an Administrator user.
b. Expand the menu options icon, in the title bar, and select Administration.
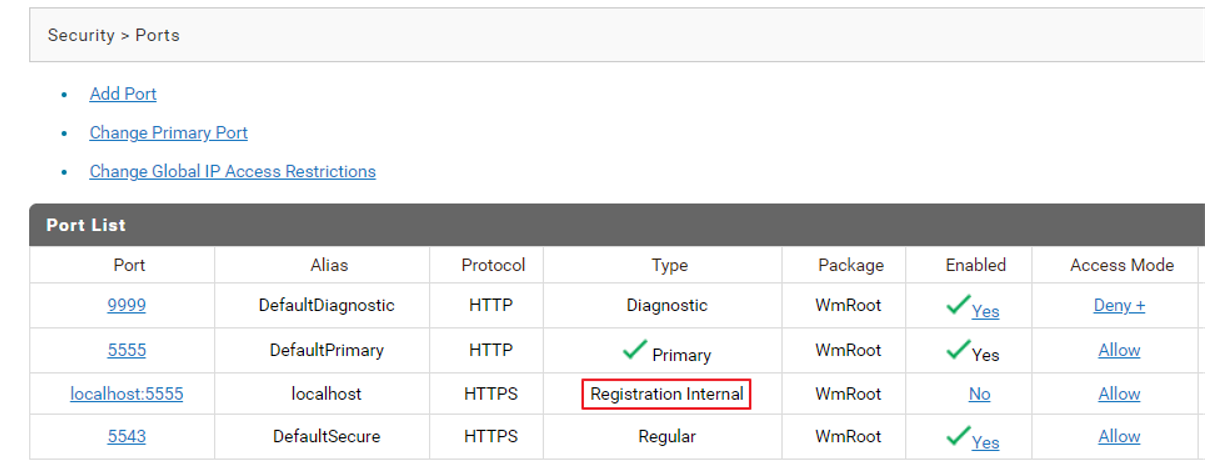
c. Navigate to Security > Ports.
d. Click Add ports.
e. Select API Gateway external option from the Type drop-down menu.
f. Click Add.
g. Provide the required information in the API Gateway external listener configuration to configure the External port.
The important fields to be configured are External port, Alias, Protocol, Backlog, and Keep alive timeout. For more information on ports, see webMethods API Gateway User's Guide.
h. To configure two-way SSL, select HTTPS in the Protocol field and select one of the following options in the Client authentication field in the in API Gateway external listener configuration section.
 Request client certificate
Request client certificate. This option requests for a certificate from the client. However, even if the client does not provide a valid certificate, the connection is established.
 Require client certificate
Require client certificate. This option requests for a certificate from the client. If the client does not provide a valid certificate, the connection is not established. If you select this option, you must also configure the
Truststore alias field.
i. Provide the required information to configure the Registration port, in the API Gateway registration listener configuration section.
The important fields to be configured are Registration port, Alias, and Protocol. For more information on ports, see webMethods API Gateway User's Guide.
j. If you execute step h, perform the following steps to configure two-way SSL.
a. Select HTTPS in the Protocol field and select Require client certificate in the Client authentication field.
b. Configure the Keystore alias and Truststore alias fields.
2. Configure Load Balancer URL in API Gateway.
a. Expand the menu options icon, in the title bar, and select Administration.
b. Navigate to General > Load Balancer.
Provide the configured external port or an external Load Balancer URL. The API endpoints have this port for external consumers. If you have a Load Balancer, then the requests from the Load Balancer must be directed to API Gateway's External port.
For more information on load balancers, see
Clusters and Load Balancers.
3. In the Green Zone Integration server, perform the following configurations to setup two-way SSL.
a. Navigate to Security > Ports.
b. Select the Registration Internal port of the API Gateway.
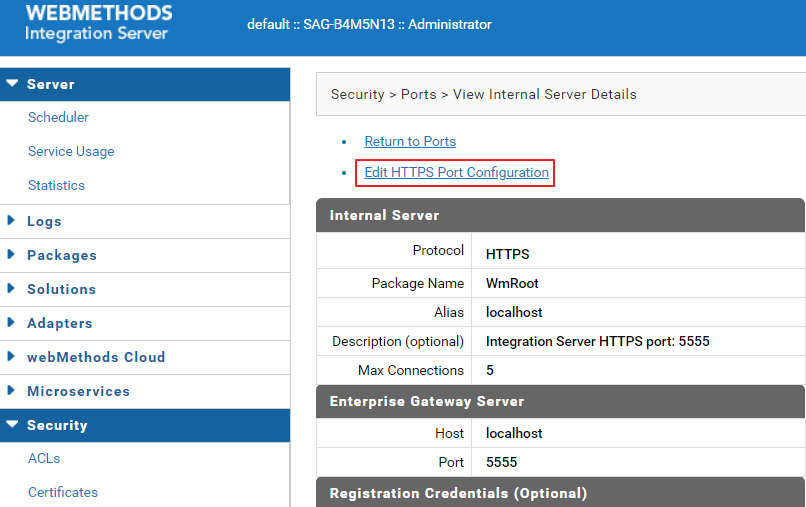
c. Click Edit HTTPS Port Configuration.
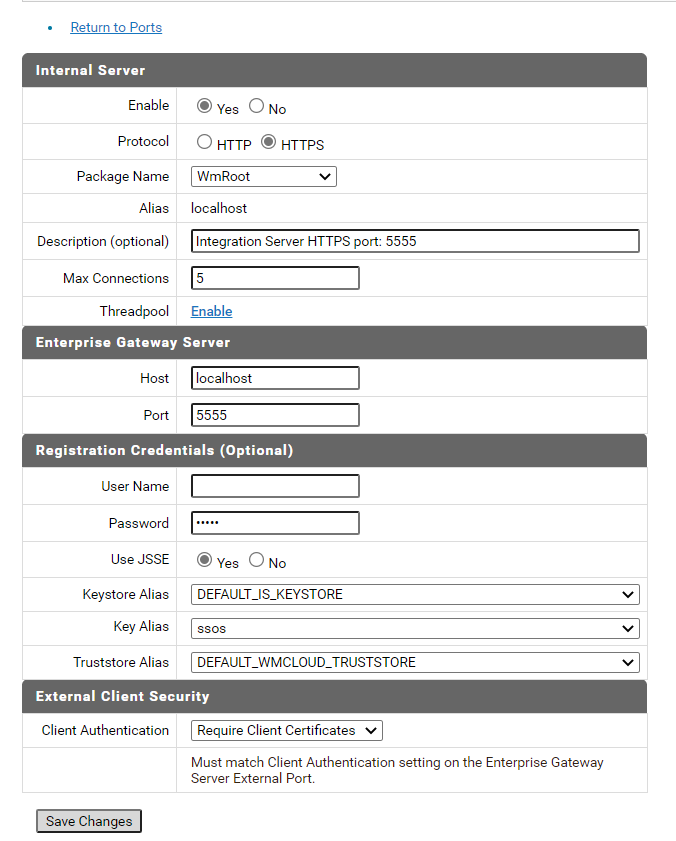
d. Select the Yes option in the Enable field.
e. Configure the fields, as required.
f. In the Registration credentials section, configure the Keystore Alias and Truststore Alias fields.
g. Select Require Client Certificates in the Client Authentication field.
h. Click Save Changes.
4. Configure API Routing Endpoints with Registration Port Alias.
a. Create an API in API Gateway.
For more information on how to create APIs, see
Creating an API.
Here, the internal server is an Integration Server and to use the reverse invoke functionality, you must modify the routing endpoint of the API created on the API Gateway instance in DMZ as shown in the below syntax.
apigateway://{REG_PORT_ALIAS}/rest/api/resource
If the internal server is not an Integration Server, you can specify the routing endpoint as regular endpoint, where the service is hosted.
Note:
If the routing points to an API that resides in API Gateway, the end point is as follows.
apigateway://{REG_PORT_ALIAS}/gateway/api/resource which in turn invokes the native service.
5. Configure Internal Server Port on the ESB Server (internal network).
a. Configure the Internal Server Port in the Integration Server where the native API resides.
b. Provide the details of API Gateway and Registration port.
6. You can now access the API by using the URL in the format http://externalserver:externalport/gateway/api-name/resource-path.
If the Internal Server runs out of registration connections, it issues the following error message:
number requests waiting for a registration connection.
Each connection consumes a thread, either from the Internal Server's common thread pool or from the internal listener's private thread pool, if one is defined. The consumed thread can only be used to process requests from API Gateway in DMZ.
If you have defined a private thread pool for the internal registration listener, the number of connections you can specify in the Max Connections box is limited to the maximum number of threads allowed in the private thread pool for this listener.
If you have multiple internal registration listeners, each with its own private thread pool, the same rule applies for each internal registration listener.
If you have not defined a private thread pool for an internal registration listener, a reasonable limit for the Max Connections box is 75% of the number of server threads specified in Server Thread Pool Max Threads box on the Settings > Resources page. If you have multiple internal registration listeners and none of them have private thread pools, the sum of all connections specified in the Max Connections boxes for these listeners should not exceed 75% of the number of server threads specified in Server Thread Pool Max Threads.
A thread remains open unless it is closed by a firewall, a network glitch, or an exception.
Note:
Since the Client Authentication in Integration server is set to Require client certificates, you must provide a certificate and map it to a user. To learn more about how to do this, see
Importing a Certificate and Mapping to User.