Reverse Invoke Configuration in API Gateway
Reverse invoke allows you to securely expose your API end points without exposing the backend APIs or services. You can configure reverse invoke by initiating a connection from the backend servers of the API Gateway present in the DMZ zone.
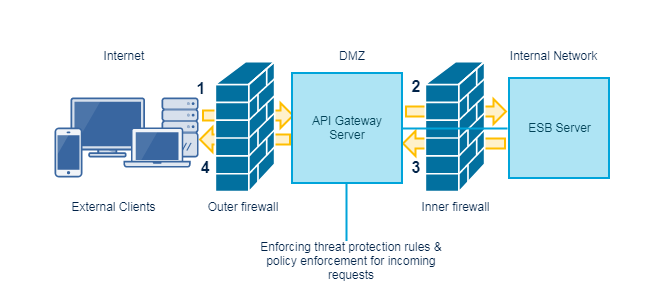
The following image shows how an internal server (API Gateway or webMethods Integration Server ) in the green zone connects to an API Gateway in the DMZ zone.
In a reverse invoke scenario, you must have paired ports in the external server (external port used for external clients and a registration port). The external client's requests are routed to external port which in turn routes the requests to its paired port that is the registration port. You must also create an internal port in the internal server, which responds to requests present in the registration port.
Note:

If a request is made to the external port and if the API is not available, the request is delegated to the registration port. The listener port configured on the green zone
API Gateway listens to the registration port and picks up this request (reverse invoke), processes it, and then sends back the response to the DMZ
API Gateway.

If a request is made to the external port and if the API exists locally, the DMZ
API Gateway processes the request.

The registration port and the external port operate independently. If you define the registration port with the HTTP protocol, you can still configure the external port with the HTTPS protocol.
For more information on ports, see
Ports.
In a paired gateway deployment scenario, if your API Gateway is behind an internal firewall and is not allowed to accept communications from external clients through the DMZ, then you can configure the API Gateway instance in DMZ with an external port to listen to the requests from external clients. You can then use reverse invoke to route the requests to the internal servers. The API Gateway internal listener port or the WebSocket listener port receives the requests from the registration port of the API Gateway present in DMZ, thus eliminating the need to open a port in the internal firewall to let the traffic through. External clients send requests to the API Gateway present in DMZ. The DMZ API Gateway's external port listens to these requests and evaluates each request against the API Gateway rules that have been defined. The DMZ API Gateway then passes the requests that have not violated any rules, to the to the registration port from where the internal server pulls the requests of the internal network. These listener ports process the requests and send the responses to the DMZ API Gateway, which then passes the responses back to the client.
You can configure reverse invoke setup in one of the following ways: