This document covers the following topics:
Handling Security from the Application's - Status Link Point-of-View
Handling Security from the Change Control Log's Point-of-View
It is possible to use PAC under the following security approaches:
NSC profiles
PAC profiles
Activity Authorisation Exit
Every time, you are confronted with the object type Application, you have do deal with the security topic in PAC.
The following PAC entities belong to exactly application:
application
application - status link
migration path
migration event
object
token (record of archived or retired object)
object - status link
hostoric object - status link
change control log
The following diagram illustrates what happens in terms of security if an activity is invoked.
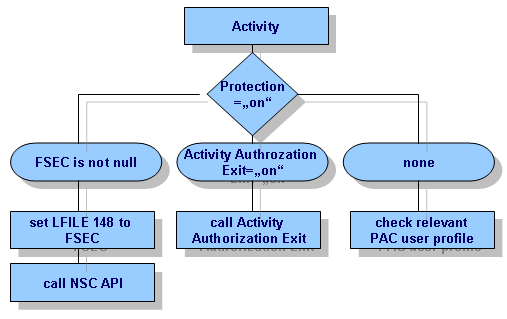
If the call of the NSC API fails (e.g. because NSC is not installed, the FSEC is unreachable or does not contain the NSC PAC user profile defaults, then PAC seeks a PAC profile for the current user ID. If such a profile is found and turns out to be one of a PAC administrator, it is used instead of the non-existent or unusable NSC profiles. If such a profile is not found or turns out not to be one of a PAC administrator, the activity will not be authorized. In particular, if this happens at the beginning of a PAC session, the user does not get access to PAC - even to functions that are allowed to anyone with some NSC PAC profile.
According to an FSEC, each user either is a PAC user or not. The NSC definitions do not differentiate between one ACF and another. If PAC works under the NSC regime, the relevant NSC definitions are sought in the FSEC specified in the ACF. A user will be allowed to start a PAC session if he is a PAC user according to the NSC definitions in the FSEC specified in the ACF. If the checking of the said definition fails because NSC is not installed in the current FNAT or because the relevant FSEC is unreadable or because it does not contain PAC related defaults, then a PAC profile of the user will be sought (in the ACF), and, if it is found and one of an administrator, then PAC will switch to PAC regime.
A USER is allowed to start a PAC session if and only if PACEX033 responds to a call with 0000 or 0001 (PACEX033-PARA.RESP).
A USER is allowed to start a PAC session if and only if he has a PAC profile (in the ACF).
A USER is considered a PAC administrator if he has a PAC profile (in the ACF) with the Administrator flag at 'Y'es.
A user is allowed to view an application record if he has NSC reading permission for the application. One is allowed to add an application record only if he has NSC reading and adding permissions for the application. A user is allowed to modify an application record only if he has NSC reading and modifying permissions for the application. He is allowed to purge an application record only if he has NSC reading and deleting permissions for the application.
A user is allowed to view an application record if PACEX033 responds to a call with 0000 or 0001 (PACEX033-PARA.RESP) and TRUE (or another odd value) in PACEX033-PARA.PERM(0). He is allowed to add an application record only if PACEX033 responds to a call with 0000 or 0001 (PACEX033-PARA.RESP) and TRUE (or other odd values) in both PACEX033-PARA.PERM(0) and PACEX033-PARA.PERM(1). A user is allowed to modify an application record only if PACEX033 responds to a call with 0000 or 0001 (PACEX033-PARA.RESP) and TRUE (or other odd values) in both PACEX033-PARA.PERM(0) and PACEX033-PARA.PERM(2). He is allowed to purge an application record only if PACEX033 responds to a call with 0000 or 0001 (PACEX033-PARA.RESP) and TRUE (or other odd values) in both PACEX033-PARA.PERM(0) and PACEX033-PARA.PERM(3).
A user is allowed to view an application record if the Applications flag in his PAC profile is at 'M'odify or 'R'ead. He is allowed to add, modify, or purge an application (record) only if the Applications flag in his PAC profile is at 'M'odify.
See Application.
See Application.
A user is allowed to view an application - status link if the Application Status Links flag in his PAC profile is at 'M'odify or 'R'ead. He is allowed to add, modify, or purge an application - status link only if the Application Status Links flag in his PAC profile is at 'M'odify.
See Application.
See Application.
A user is allowed to view a migration path if the Migration Paths flag in his PAC profile is at 'M'odify or 'R'ead. He is allowed to add, modify, or purge a migration path only if the Migration Paths flag in his PAC profile is at 'M'odify.
A user is allowed to view a migration event (and its attachments: migration list, audit report, etc) if he has NSC reading permission for the application. A user is allowed to add a migration event only if he has NSC reading and event adding permissions for the application. A user is allowed to modify a migration event only if he has NSC reading and event modifying permissions for the application. To be allowed to authorise an event a user must be allowed to modify it and must have logged on to SYSPAC with an id (individual or chosen group) listed among the authorisers in the relevant migration path. A user is allowed to submit a migration event only if he has NSC reading and event submitting permissions for the application. A user is allowed to purge or refresh a migration event only if he has NSC reading and event deleting permissions for the application. A user is allowed to finalise an archiving event only if he has NSC reading and event submitting permissions for the application and has logged on to SYSPAC with an id (individual or chosen group) listed among the authorisers in the application's CONTROL to RETIRE migration path.
Like under NSC regime with [PACEX033-PARM.PERM(0,4,5,6,7)], for the application, defining the reading, event adding, event modifying, event submitting, and event deleting permissions respectively.
A user is allowed to view a migration event if the Migration Events flag in his PAC profile is at 'M'odify or 'R'ead. He is allowed to add, modify, or purge a migration event only if the Migration Events flag in his PAC profile is at 'M'odify. He is allowed to authorise an event only if the Authorize Migration Events flag in his PAC profile is at 'Y'es and he has logged on to SYSPAC with an id (individual or chosen group) listed among the authorisers in the relevant migration path. He is allowed to submit or refresh an event only if the corresponding flag in his PAC profile is at 'Y'es. He is allowed to finalise an archiving event only if he is a PAC administrator.
A user is allowed to view a PAC JCL text (job) if he has NSC reading permission for it. He is allowed to add, modify, purge, or submit (directly, not by submitting an event) a JCL text only if he has reading and a corresponding permission for the JCL text.
Like under NSC regime with [PACEX033-PARM.PERM(0,1,2,3,4)], for the JCL text, defining the reading, adding, modifying, deleting, and submitting permissions respectively.
A user is allowed to view or submit a JCL text if the Jobs flag in his PAC profile is at 'M'odify or 'R'ead. He is allowed to add, modify, or purge a JCL text only if the Jobs flag in his PAC profile is at 'M'odify.
A user is allowed to view a PAC FTT if he has NSC reading permission for it. He is allowed to add, modify, or purge an FTT only if he has reading and a corresponding permission for the FTT.
Like under NSC regime with [PACEX033-PARM.PERM(0,1,2,3)], for the FTT, defining the reading, adding, modifying, and deleting permissions respectively.
A user is allowed to view an FTT if the File Translation Tables flag in his PAC profile is at 'M'odify or 'R'ead. He is allowed to add, modify, or purge an FTT only if the File Translation Tables flag in his PAC profile is at 'M'odify.
A user is allowed to view a PAC object (and its attachments: source, USED list, etc) if he has NSC reading permission for the application. He is allowed to purge an object or its historical object - status link only if he has reading and event submitting permissions for the application and has logged on to SYSPAC with an id (individual or chosen group) listed among the authorisers in the application's CONTROL to RETIRE migration path. He is allowed to purge an object's archive token only if he has reading and event submitting permissions for the application and has logged on to SYSPAC with an id (individual or chosen group) listed among the authorisers in the application's ARCHIVE to RETIRE migration path.
Like under NSC regime with [PACEX033-PARM.PERM(0,6)], for the application, defining the reading and event submitting permissions respectively.
A user is allowed to view a PAC object if the Object Versions flag in his PAC profile is at 'R'ead. He is allowed to purge an object, its historical object - status link, or archive token only if he is a PAC administrator.
A user is allowed to view or purge a change control log only if he has NSC reading permission for the application.
Like under NSC regime with [PACEX033-PARM.PERM(0)], for the application, defining the reading permission.
A user is allowed to view a change control log if the Change Control Logs flag in his PAC profile is at 'R'ead. He is allowed to purge a change control log only if he is a PAC administrator.