This document covers the following topics:
PAC provides both online and batch security.
The following rules apply to PAC online security:
The startup transaction is MENU; no profile is needed if you are using Natural Security, otherwise a profile must be defined. "Steplib" must be set to SYSTEM.
Users who may authorize migration events are assigned when the migration path is defined by PAC. These users may or may not be a PAC administrator.
PAC user profiles can only be maintained using PAC administrator functions.
Under Natural Security, the protection of library SYSPAC determines the user's (or group's) ability to access PAC.
Under Natural Security, the protection of library SYSPACA determines the user's (or group's) ability to perform PAC administrator functions.
If running Natural Version with Natural Security, you may define library SYSPACUS as a steplib of library SYSPAC (in addition to SYSTEM). For details, see the PAC/PAA Installation documentation.
Define steblibs
If Natural Security is not
installed, the standard steplib setting and any additional site-specific
steplib setting must be applied as well, using the Natural LOGON user exit.
Modify LOGON
A sample of LOGON source is provided in
library SYSPACUS.
Move LOGON000 into the FNAT system library.
To accommodate environments that do not allow the same user ID to be used simultaneously for both online and batch, the PAC administrator must specify a batch user ID for each online user.
Depending on the installation standards, each user can be allocated a unique batch ID, or several users may use a single batch ID.
If a user's batch user ID is different from the online user ID, then the batch user ID also must be defined to PAC and must have the same PAC access authority as the online user ID. The batch user ID should then be included in the user's online user profile.
The batch jobs that carry out migration requests may use the Natural Security parameter AUTO=ON so that passwords need not be passed explicitly to Natural Security. When AUTO=ON is set, the job name on the first card of the JCL must be a valid user ID defined to Natural Security.
Alternatively, AUTO=OFF may be used if the migration jobs are modified.
Notes:
The Predict Security System controls access to a PAC environment either using security definitions stored in a Natural Security file or via user exit PACEX33
An individual environment can be defined for each user or group of users and protected against unauthorized access.
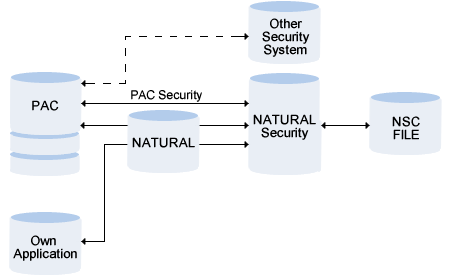
This section covers the following topics:
When a user logs on to a library, the Link ID is determined as follows:
If the user is linked directly to the library, the link ID is the same as the user ID.
If the user is linked to the library indirectly as member of a group, the link ID is the group ID.
See your Natural Security documentation for more information.
This file contains the security definitions used by the PAC Security System for protecting objects against unauthorized access.
In terms of PAC security, an instance of an external object type.
In terms of PAC security, an external object type is a class of objects to be protected. The following external object types are available for protecting PAC data:
PAC Application
PAC FTT
PAC JCL TEXT
PAC Security means the following:
the external object types in Natural Security, for example PAC Application
the security profiles defined to limit access to instances of external object types.
A security definition in Natural Security.
PAC Security is realized with the Software AG product Natural Security. This product allows you to
define the persons who can process the protected objects
define the objects to be protected
PAC transfers the administrative functions listed above to Natural Security. A security object is a security definition valid for different data types:
Range of PAC objects (for example all applications that start with USER1)
Fully qualified PAC object (for example application USER1-FI-ADA2)
When a PAC function is called, an internal PAC routine generates an Natural Security call. This call checks the security definitions in Natural Security for
the current link ID
the function the user wants to execute
the data the user wants to access.
The Security Check does not depend on whether Natural Security is installed. The PAC parameter Protection in the System Defaults determines whether PAC Security is called. This parameter can be defined for each ACF file.
The system checks whether the current user is authorized to logon to library SYSPAC.
PAC definitions are not protected in Natural Security as default. This means that when PAC is delivered, each user has access to every object and can execute any PAC function. PAC Security only takes effect when access to objects is explicitly restricted for individual users or groups of users. This section lists the steps necessary to set up your environment so you can protect objects and functions against unauthorized access.
This section covers the following topics:
Libraries SYSPAC, SYSPACA, SYSPACUS, SYSPAA and SYSPAAUS must be defined as libraries in Natural Security. See Library.
PAC users must be defined as Users in Natural Security. See User.
New users can be added manually with the function Add user in Natural Security.
The users must be authorized to logon to the library SYSPAC in Natural Security. See your Natural Security documentation for more information.
Enter database and file number of the NSC file in the General Defaults > System Defaults > Modify System Defaults screen.
Note:
Do not set the parameter Protection to Y at this point!
You must first add the Natural Security definitions as described in Step 4
below.
Add the standard definitions for Natural Security with the General Defaults > System Defaults > Modify NSC > PAC User Profile Defaults.
If you wish, you can create your own Security definitions for any object in Natural Security - either for an individual user or for a group of users.
To prevent users changing Security parameters, we recommend you to check the existing PAC user profiles for the administration authorization.
After you have added Natural Security default definitions, set the parameter Protection in the General Defaults > System Defaults screen to Y to activate Security. This parameter can defined for each ACF file.
This section describes the entities in Natural Security that are used for security definitions in PAC.
This section covers the following topics:
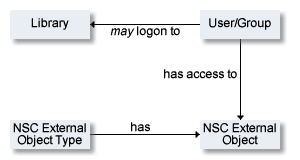
This example illustrates the following situation:
The user Smith is authorized to logon to library SYSPAC and has access to Application object PERSONNEL, an instance of NSC external object type PAC application.
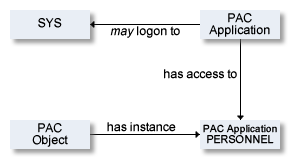
A user is the central point of the PAC Security system. This object represents a person that works with the system.
Users can be a member of one or more groups. See Group.
When a user logs on to a library, the link ID is determined as follows:
If the user is linked directly to the library, the link ID is the same as the user ID.
If the user is linked to the library indirectly as member of a group, the link ID is the group ID.
See your Natural Security documentation for more information.
A group in Natural Security is a collection of users. See User.
The number of users in a group is unlimited.
Groups have no relationships with other groups. This means a group cannot be part of another group.
A user can belong to several groups.
New groups can also be added in Natural Security with the function Add user.
To use PAC Security, the libraries SYSPAC, SYSPACUS, SYSPAA and SYSPAAUS must be defined as libraries in Natural Security.
An NSC external object type is a group of things to be protected.
These NSC external object types and their standard definitions are added in Natural Security with the General Defaults > System Defaults > Modify NSC PAC User Profile Defaults.
Application
FTT
JCL Text
The default value for all NSC external object types is allowed. If you keep the default value as allowed and do not add any security definitions, each user can execute any function and access any PAC object.
If you set the default value for a NSC external object type to disallowed, you have to give each user or group explicit access to all instances of this NSC external object type they needs for their work.
The following access can be given for instances of all NSC external object types:
| NSC External Object | Permission |
|---|---|
| Application
Note: |
read |
| FTT
Note: |
read |
| Job Control
Note: |
read |
Y: Access is granted
N: Access is denied
Security definitions can be added in Natural Security for PAC objects.
All instances must be added manually in Natural Security.
To add security definitions to documentation objects:
Logon to library SYSSEC
Select Maintenance, then choose PAC Application / PAC FTT / PAC JCL TEXT
In the command line enter ADD
In the upcoming window enter the object name. See also screen below.
+------------------------------------------------------------+ | ADD * | | | | Please enter object´s ID | | _______________________ | | | | | +------------------------------------------------------------+ |
Possible access modes for instances of this NSC external object type are READ, ADD, MODIFY and DELETE.
With PAC Security you can determine that certain users or groups only have access to certain objects. There are three strategies you can follow when protecting objects:
Protect Individual objects Example: The application SALARY can only be read/modified by certain users.
Protect a range of objects Use naming conventions to group objects and take advantage of asterisk notation in Natural Security. Example: User USER1 has been denied READ access to application objects in general, but READ access for applications that begin with his user ID. The more specific authorization has priority.
Protect all objects of a particular type.