Entire Event Management consists of the following functional areas:
These are described in more detail below.
In addition to the conventional views of all messages from a single operating system, Entire Event Management displays selected messages from selected operating systems. Messages from multiple operating systems can be displayed together; irrelevant messages can be excluded from display.
In Entire Event Management, the conventional operator console of an operating system is called a "Physical Console". It displays all the messages from one operating system. Entire Event Management enables the user to switch the operator console to any Physical Console, thus providing quick and easy access to every Physical Console in a computer network.
Using Entire Event Management, you can select from multiple Physical Consoles the messages that are relevant to a particular topic and you can log those messages for display in a Logical Console. A Logical Console can be restricted to a particular subsystem; it need not be restricted to a single operating system. Any Logical Console can be viewed at the operator console in the same way as a Physical Console. The display at a Logical Console can be restricted to messages with high priority.
A Logical Console provides a selective view of messages from one or more operating systems. In this way, Entire Event Management achieves centralized control of different operating systems.
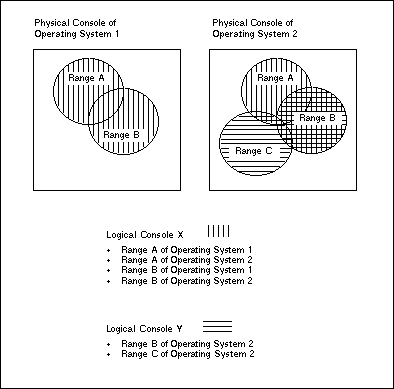
The concept of Logical Consoles provides a wide range of uses. Some examples are listed below:
Important messages can be extracted from one or more operating systems and logged in one Logical Console;
All messages relevant to particular subsystems on various operating systems in the Entire Event Management environment can be selected and logged in a Logical Console, for example:
Messages from Adabas databases;
VTAM messages;
TP system messages;
z/OS messages in general;
Irrelevant messages can be suppressed.
Benefits for the computer operator of logging messages to Logical Consoles include:
Easy monitoring and control of a particular subsystem, facilitating faster response when abnormal situations or problems arise;
Ability to control a departmental computer to which no particular operator is assigned.
Automatic operator responses to system Events are achieved by defining Automation Rules. An Automation Rule links an Action to an Event. The Action is triggered by the occurrence of the Event. An automatic operator response consists of one or more Actions that are triggered by an Event. An Event occurs if a message satisfies the conditions set in the Event definition, this means that parameters such as job name, message ID, or character strings appear in the message.
Events can be made inter-dependent by defining an Event Tree that relates them. The following figure illustrates this concept:
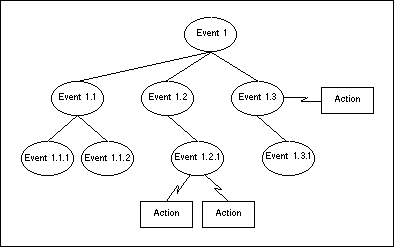
An Event Tree is a special kind of decision tree. Events on a higher level must occur before dependent Events on a lower level can occur. Any path in this tree is active if each constituent Event has occurred. For example, in the figure above, Event 1.2.1 can only occur when Event 1 and Event 1.2 have already occurred.
The following types of Action can be triggered by an Event; multiple Actions for a single Event can be defined:
Display in a Logical Console an information box containing text;
Issue operator commands;
Submit a job;
Send a message to users, WTOs or Logical Consoles;
Execute a Natural program;
Start an Entire Operations job network.
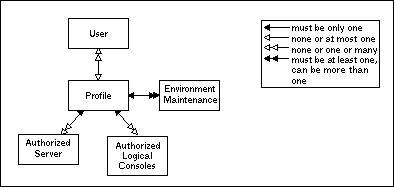
Access to Entire Event Management objects and functions can be restricted by assigning a Profile to the User.
A Profile can forbid access to any Entire Event Management object or can grant access on four levels: display, modify, add and delete. This ensures enhanced security of sensitive subsystems within the Entire Event Management environment.
Access to the defined environment of Entire Event Management can also be limited. In a Profile, you can define:
which Logical Consoles can be accessed;
which Entire System Server Server and Entire Event Management Server can be accessed;
which security-sensitive functions can be used such as issuing operator commands and controlling the Entire Event Management Servers.
Entire Event Management's security concept is: what a user can see, the user can use.