This document describes the utility "ADARBA".
The following topics are covered:
The ADARBA utility is used to initialize and administrate the RBAC security definitions, which are stored in the RBAC system file in the database.
ADARBA initializes, creates, and modifies basic security objects such as users and roles, and is used to grant or revoke permissions. See Authorization for Adabas Utilities for further information.
The database to be used must be online.
Note
Each ADARBA command represents a transaction. This means that
modifications to the security definitions take effect immediately.
Important
Access to this utility should be strictly limited to the
person or persons responsible for database security.
This utility is a multi-function utility. For more information about single- and multi-function utilities, see Adabas Basics -> Using Utilities -> Single- and Multi-function utility.
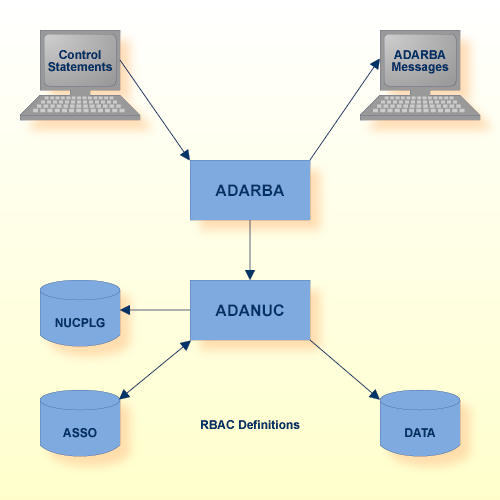
| Data Set | Logical Name | Storage Medium | Additional Information |
|---|---|---|---|
| RBAC Definitions | Database/RBAC System File | ||
| Control statements | stdin/SYS$INPUT | Utilities Manual | |
| ADARBA messages | stdout/SYS$OUTPUT | Messages and Codes |
The following table shows the nucleus requirements for each function and the checkpoints written:
| Fuction | Nucleus must be active | Nucleus must NOT be active | Nucleus is NOT re-quired | Checkpoint writ-ten |
|---|---|---|---|---|
| INITIALIZE | X | SYNX (see note) |
Note
In addition, an ADAFDU checkpoint is generated, indicating the RBAC system file
number.
The following control parameters are available:
[NO]ABORT CREATE ,{OPERATION|USER|OBJECT|ROLE} = string M DBID = number DROP ,{OPERATION|USER|OBJECT|ROLE} = string [NO]ECHO EXPORT = filepath GRANT ,ROLE = string [,TO] ,USER = string GRANT ,OPERATION = string [,OBJECT = string] [,TO] ,ROLE = string GRANT ,OPERATION = { ANY|DELETE|INSERT|READ|UPDATE} ,OBJECT = number [,TO] ,ROLE = string IMPORT = filepath INITIALIZE ,RBAC_FILE = number LIST ,{OPERATION|USER|OBJECT|ROLE} [= string] LIST ,ASSIGNMENT, {USER [= string]|ROLE [= string]|PERMISSION} MAINTAIN REVOKE ,ROLE = string [,FROM] ,USER = string REVOKE ,OPERATION = string [,OBJECT = string] [,FROM] ,ROLE = string REVOKE ,OPERATION = { ANY|DELETE|INSERT|READ|UPDATE} ,OBJECT = number [,FROM] ,ROLE = string [NO]STAT
Notes:
[NO]ABORT
This function turns forced termination on or off.
If ABORT is specified, ADARBA terminates execution in case of an error and returns an error status.
If ADARBA is executed in interactive mode, the default is NOABORT.
If ADARBA is called with parameters, the default is ABORT.
Note
[NO]ABORT can be specified in interactive mode or, if an input
script is used to provide the RBAC security definitions, in the input
script.
adarba: abort %ADARBA-I-INP, abort %ADARBA-I-PAR, forced termination enabled
For this ADARBA session, forced termination is enabled.
CREATE ,{OPERATION|USER|OBJECT|ROLE} = string
This function creates an RBAC definition of a given type and value.
The value assigned to items of type USER must be a valid logon credential; e.g. user identification. These values are platform-specific:
Linux: user_identification
Windows: domain\user_identification
See Authorization for Adabas Utilities for further information.
adarba: create,user=domain\userid
The user definition domain\userid for Windows is created.
DBID = number
This parameter selects the database to be used.
Note
The nucleus must be running.
adarba: dbid=200
The database currently being used is database 200.
DROP ,{OPERATION|USER|OBJECT|ROLE} = string
This function deletes an RBAC definition with the given type and value. If this RBAC definition is referenced by a user or permission assignment, the corresponding assignment is revoked implicitly to avoid incomplete RBAC definitions.
adarba: drop,user=NEWUSER
The user definition NEWUSER is deleted.
[NO]ECHO
This function turns the echo of the command input on or off. The default is ECHO.
Note
[NO]ECHO can be specified in interactive mode or, if an input
script is used to provide the RBAC security definitions, in the input
script.
adarba: echo %ADARBA-I-INP, echo %ADARBA-I-PAR, echo input enabled
For this ADARBA session, echo input is enabled.
EXPORT = filepath
The export function creates a text file with the RBAC security definitions. This file contains:
the user-defined security definitions
the initial definitions, created by the initialize function.
The administrative user can edit this text file and add entries to create operation, user, object, or role, and to grant operations.
Note
This function can only be executed if the RBAC system file is initialized.
adarba: export=myRBAC %ADARBA-I-INP, export= %ADARBA-I-RDREC, Number of records processed: 59
The file myRBAC contains 59 security definitions.
GRANT ,ROLE = string [,TO] ,USER = string
This function grants a role to a user.
adarba: grant,role=NEWROLE,to,user=NEWUSER
The user NEWUSER is assigned the role NEWROLE.
GRANT ,OPERATION = string [,OBJECT = string] [,TO] ,ROLE = string
This function grants a role the permission to perform an operation on an object.
adarba: grant,operation=ada.uti.opr,to,role=ANYROLE
The role ANYROLE is assigned the permission to perform the operation ada.uti.opr on the default object (DBID.CURRENT).
GRANT ,OPERATION = { ANY|DELETE|INSERT|READ|UPDATE} ,OBJECT = number [,TO] ,ROLE = string
This function grants a role the permission to perform the corresponding Adabas commands on an Adabas file of the default database (DBID.CURRENT).
The predefined operations DELETE, INSERT, READ and UPDATE are used to group the Adabas direct commands according to their functionality. ANY is a short notation for DELETE, INSERT, READ and UPDATE .
OBJECT is interpreted as the Adabas file number if the value is a valid Adabas file number. Other values, in particular DBID.CURRENT, are accepted as object but not interpreted.
adarba: grant,operation=read,object=12,to,role=ANYROLE
The role ANYROLE is assigned the permission to perform the operation READ on file number 12 of the current database.
adarba: grant,operation=any,object=12,to,role=ANYROLE
The role ANYROLE is assigned the permission to perform the operations DELETE, INSERT, READ and UPDATE on file number 12 of the current database.
IMPORT = filepath
The import function reads a text file with definitions and creates the RBAC security definitions accordingly. This file can contain:
the user-defined security definitions
the initial definitions, created by the initialize function.
The order of the entries is irrelevant, whether granted operations are defined prior to the entity creation, the list will be sorted internally.
Note
This function can only be executed if the RBAC system file is initialized. The
function operates as an update function, existing security definitions will not be
deleted, and already existing definitions will be just ignored.
adarba: import=myRBAC %ADARBA-I-INP, import= %ADARBA-I-RDREC, Number of records processed: 0
The file myRBAC contains no new security definition.
INITIALIZE RBAC_FILE = number
The initialize function creates the RBAC system file and loads the initial security definitions.
The RBAC system file can be created with all possible block sizes for the ASSO container and the DATA container.
adarba: initialize rbac_file=200
LIST ,{OPERATION|USER|OBJECT|ROLE} [= string]
This function displays the RBAC definition, if a string value is supplied and the specified definition exists.
This function displays all active RBAC definitions of the type specified if no value is supplied.
adarba: list,role=PUBLIC PUBLIC
The role PUBLIC is displayed.
adarba: list,role= PUBLIC
The role PUBLIC is displayed because it is the only active role definition.
LIST ,ASSIGNMENT ,{USER [= string]|ROLE [= string]|PERMISSION}
This function displays, according to the type specified, active user, active role, or permission assignments. It displays assignments for the specific user and/or specific role if a string value is supplied, otherwise, it displays all active user and role as-signments.
adarba: list,assignment,user PUBLIC,PUBLIC
All user assignments are displayed.
adarba: list,assignment,role PUBLIC,PUBLIC
All role assignments are displayed.
adarba: list,assignment,user=NEWUSER PUBLIC,NEWUSER
Assignments for the user NEWUSER are displayed.
adarba: list,assignment,role=NEWROLE NEWROLE,PUBLIC
Assignments for the role NEWROLE are displayed.
adarba: list,assignment,user=NEWUSER,role=NEWROLE NEWROLE,PUBLIC
Assignments for the role NEWROLE and the user NEWUSER are displayed.
MAINTAIN
This function deactivates obsolete user assignments.
NoteMAINTAIN can be specified in interactive mode or, if an
input script is used to provide the RBAC security definitions, in the input
script.
adarba: maintain any_role,inactive_user
The obsolete user assignment ‘any_role,inactive_user' is now deactivated.
REVOKE ,ROLE = string [,FROM] ,USER = string
This function revokes a role, which was granted to the user.
adarba: revoke,role=NEWROLE,from,user=NEWUSER
The role NEWROLE is revoked from user NEWUSER.
REVOKE ,OPERATION = string [,OBJECT = string] [,FROM] ,ROLE = string
This function revokes a permission, which a role was granted, to execute an operation on an object.
adarba: revoke,operation=ada.uti.dbm,from,role=NEWROLE
The permission, which the role NEWROLE had been granted, to perform the operation ada.uti.dbm on the default object DBID.CURRENT, is revoked.
REVOKE ,OPERATION = { ANY|DELETE|INSERT|READ|UPDATE} ,OBJECT = number [,FROM] ,ROLE = string
This function revokes a permission, which a role was granted, to perform the corresponding Adabas commands on an Adabas file of the default database (DBID.CURRENT).
The predefined operations DELETE, INSERT, READ and UPDATE are used to group Adabas direct commands according to their functionality. ANY is a short notation for DELETE, INSERT, READ and UPDATE .
OBJECT is interpreted as the Adabas file number if the value is a valid Adabas file number.
adarba: revoke,operation=read,object=12,from,role=NEWROLE
The permission, which the role NEWROLE had been granted, to perform the operation READ on file number 12 of the current database, is revoked.
adarba: revoke,operation=any,object=12,from,role=NEWROLE
The permission, which the role NEWROLE had been granted, to perform the operations DELETE, INSERT , READ, and UPDATE on file number 12 of the current database, is revoked.
[NO]STAT
This function enables or disables the display of command statistics. The default is STAT.
Note
[NO]STAT can be specified in interactive mode or, if an input
script is used to provide the RBAC security definitions, in the input
script.
adarba: stat %ADARBA-I-INP, stat %ADARBA-I-PAR, command statistics enabled
Command statistics are enabled for this ADARBA session.
If command statistics are enabled, statcmd will display the number of errors which occurred when a valid function is executed through interactive or non-interactive mode.
adarba: dbid=50 %ADARBA-I-INP, dbid=050 %ADARBA-E-NOONLF, No online-functions possible, Nucleus not running %ADARBA-I-STATCMD, 1 error(s) occurred