This document describes the utility "ADASCR".
The following topics are covered:
The security utility ADASCR creates, modifies and deletes file protection levels and user passwords, and enables the security capabilities of individual passwords. Additionally, the utility is used to display file and password security information. The output of the export functionality of ADASCR can be used to apply some of all of the security definitions of a database to another database.
Access to this utility should be strictly limited to the person or persons responsible for database security (DBA).
Multiple functions may be specified within a single run of ADASCR. There is no restriction on the number of functions which may be specified.
The affected database(s) must be online.
All updates resulting from ADASCR take effect immediately.
This utility is a multi-function utility.
Note:
To copy existing security definitions from one hardware
architecture or operating system to another you must use the EXPORT control
parameter. You cannot copy the security definitions from one hardware
architecture to another by using ADAULD/ADADCU and ADACMP/ADAMUP - this is
because the data stored in the security file are stored in a platform-dependent
internal format.
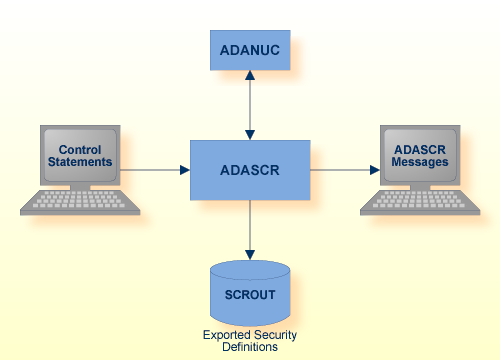
| Data Set | Logical Name/ Environment variable |
Storage Medium | Additional Information |
|---|---|---|---|
| Control Statements | stdin/ SYS$INPUT |
Utilities Manual | |
| ADASCR Messages | stdout/ SYS$OUTPUT |
Messages and Codes | |
| Exported Security Definitions | SCROUT | Disk | Utilities Manual |
The utility writes no checkpoints.
The following control parameters are available:
CHANGE {=|:} (string, string)
M DBID = number
DELETE = string
DISPLAY = [PASSWORDS |
PERMISSIONS, PASSWORD {=|:} {* | string} |
PROTECTIONS,
FILE = {* | (number[-number][,number[-number]]...)} |
VALUE_CRITERIA, PASSWORD {=|:} {* | string}]
EXPORT = {PASSWORDS,
D [TARGET_ARCHITECTURE = KEYWORD,]
PASSWORD {=|:} {* | string} |
PROTECTIONS,
D [TARGET_ARCHITECTURE = KEYWORD,]
FILE = {* | (number[-number][,number[-number]]...)} |
VALUE_CRITERIA,
D [TARGET_ARCHITECTURE = KEYWORD,]
FILE = {* | (number[-number][,number[-number]]...)}
PASSWORD = {* | string}}
INSERT {=|:} string, FILE = (number[-number][,number[-number]]...)
,ACCESS = (number[,number]...)
,UPDATE = (number[,number]...)
PROTECT = (number[-number][,number[-number]]...)
,ACCESS = (number[,number]...)
,UPDATE = (number[,number]...)
SECURITY_BY_VALUE {=|:} string, FILE = number
,ACCESS_CRITERION
,SEARCH_BUFFER = string *
,VALUE_BUFFER = string *
,UPDATE_CRITERION
,SEARCH_BUFFER = string *
,VALUE_BUFFER = string *
*The search/access buffer string parameters must be followed by <Newline> with no preceding comma.
In the following examples assume that the following ADASCR definitions have been made before:
PROTECT=9,ACCESS=9,UPDATE=9 PROTECT=9,NAME=(**,AC,AD,BC),ACCESS=(0,14,14,14),UPDATE=(0,14,14,14) PROTECT=9,NAME=(FC,FD,IC,ID),ACCESS=(14,14,14,14),UPDATE=(0,0,0,0) PROTECT=11,ACCESS=1,UPDATE=2 PROTECT=11,NAME=(**,AA,AC,AE),ACCESS=(0,6,3,5),UPDATE=(0,9,9,7) PROTECT=11,NAME=(AD,AI,AJ,AK),ACCESS=(4,10,10,10),UPDATE=(8,12,12,12) PROTECT=11,NAME=(AL,AR,AS,AT),ACCESS=(10,7,7,7),UPDATE=(12,9,9,9) PROTECT=11,NAME=(AX,AY,AZ),ACCESS=(11,11,8),UPDATE=(13,13,10) PROTECT=(12,13),ACCESS=(12,13),UPDATE=(12,13) INSERT=000009CD,FILE=(9,12,13),ACCESS=(0,0,0),UPDATE=(13,13,13) INSERT=00110203,FILE=(11),ACCESS=(2),UPDATE=(3) INSERT=00110304,FILE=(11),ACCESS=(3),UPDATE=(4) INSERT=00110506,FILE=(11),ACCESS=(5),UPDATE=(6) INSERT=00110809,FILE=(11),ACCESS=(8),UPDATE=(9) INSERT=09CD09CD,FILE=(9,12,13),ACCESS=(13,13,13),UPDATE=(13,13,13) SECURITY_BY_VALUE=09CD09CD,FILE=9,ACCESS_CRITERION,SEARCH_BUFFER=CA,1,EQ,O,CA,1,EQ. VALUE_BUFFER=AU UPDATE_CRITERION,SEARCH_BUFFER=CA,1,EQ. VALUE_BUFFER=U
CHANGE {=|:} (string, string)
This function changes an existing password.
The password specified by the first string must be an existing password.
The value specified by the second string must not be the same as an existing password. A password may be between 1 and 8 characters long. If less than 8 characters are specified, trailing blanks are added. The password may not contain any special characters or embedded blanks.
If you specify an equals sign, the value given for 'string' will be converted to upper case; if you specify a colon, no upper-case conversion is performed.
All entries in effect for the password specified by the first string remain in effect for the new password.
adascr: change:(000009CD,000009cd) %ADASCR-I-PWCHA, password "000009CD" changed to "000009cd"
The password OLDPW1 is changed to NEWPW1.
DBID = number
This parameter selects the current database.
Note:
The nucleus must be running.
adascr: dbid=155
The database currently being used is database 155.
DELETE = string
This function deletes the existing password specified by the string, together with its associated permission levels and Security by Value criteria.
adascr: delete=000009CD %ADASCR-I-PWDEL, password "000009CD" deleted
The password USERPW1 is deleted.
DISPLAY = { PASSWORDS |
PERMISSIONS, PASSWORD {=|:} {* | string} |
PROTECTIONS, FILE = {* | (number[-number][,number[-number]]...)} |
VALUE_CRITERIA, PASSWORD {=|:} {* | string}}
This function shows current security information for files and passwords, as defined by the ADASCR utility.
Details of file protection levels, passwords, password permission levels and Security by Value criteria may be displayed.
The FILE parameter provides the list, range or ranges of files for which the preceding DISPLAY function is to be applied.
The PASSWORDS parameter prints a list of the passwords currently contained in the security file in ascending, alphanumeric sequence.
adascr: display=passwords
List of defined passwords for Database 155 ("ALPHA-TS")
FORTYTWO
G6MON
USERPW1
VOYAGER
Total of 4 defined passwords
The PERMISSIONS parameter prints a list of the access and update capabilities of the specified password for each currently loaded file, by comparing the password permission information against the current file protection levels.
Where respective access or update capability is granted, this is shown by the letter Y; conversely, where the capability is not granted, this is shown by the letter N.
Where access or update permissions for a given file are granted and additional Security by Value restrictions apply to that file, this is indicated by enclosing brackets, i.e. (Y).
If field level security is defined for a file, and the permission for field access or update of a field is different from the file permission, the field and the corresponding permissions are displayed, too.
adascr: display=permissions,password=09CD09CD
password : "09CD09CD"
FILE | ACCESS | UPDATE
FIELD | |
--------------------------
1 | Y | Y
2 | Y | Y
3 | Y | Y
9 | (Y) | (Y)
AC | N | N
AD | N | N
BC | N | N
FC | N | (Y)
FD | N | (Y)
IC | (Y) | N
ID | (Y) | N
CN | N |
S2 | N |
11 | N | N
12 | Y | Y
13 | Y | Y
14 | N | N
--------------------------
Note:
CN and S2 are a collation descriptor and a superdescriptor;
for derived descriptors no update permission is displayed, because they cannot
be updated explicitly.
DISPLAY=PROTECTIONS displays the protection information for the specified files. For fields with access or update protection level greater than 0, the protection information is displayed, too.
adascr: disp=protections,file=(9-11,14)
FILE | ACCESS | UPDATE
FIELD | |
--------------------------
9 | 9 | 9
AC | 14 | 14
AD | 14 | 14
BC | 14 | 14
FC | 14 | 0
FD | 14 | 0
IC | 0 | 14
ID | 0 | 14
CN | 14 |
S2 | 14 |
11 | 1 | 2
AA | 6 | 9
AC | 3 | 9
AE | 5 | 7
AD | 4 | 8
AI | 10 | 12
AJ | 10 | 12
AK | 10 | 12
AL | 10 | 12
AR | 7 | 9
AS | 7 | 9
AT | 7 | 9
AX | 11 | 13
AY | 11 | 13
AZ | 8 | 10
PH | 3 |
S2 | 3 |
S3 | 7 |
S4 | 4 |
14 | 0 | 0
--------------------------
Note:
CN and S2 in file 9 and PH, S2, S3 and S4 are collation
descriptors, superdescriptors or phonetic descriptors; for derived descriptors
no update permission is displayed, because they cannot be updated
explicitly.
The VALUE_CRITERIA parameter prints all Security by Value criteria currently defined for the specified password.
adascr: display=value_criteria,password=* There are no value criteria defined for password "000009CD" There are no value criteria defined for password "00110203" There are no value criteria defined for password "00110304" There are no value criteria defined for password "00110506" There are no value criteria defined for password "00110809" There are no value criteria defined for password "09CD0000" password : "09CD09CD" | File | Security by Value criterion |------+---------------------------------------------------------------------- | 9 | ACCESS_CRITERION | | SEARCH_BUFFER: "CA,1,EQ,O,CA,1,EQ." | | VALUE_BUFFER: "AU" | | UPDATE_CRITERION | | SEARCH_BUFFER: "CA,1,EQ." | | VALUE_BUFFER: "U" |----------------------------------------------------------------------------- Total of 7 defined passwords
EXPORT = {PASSWORDS,
[TARGET_ARCHITECTURE = keyword,]
PASSWORD {=|:} {* | string} |
PROTECTIONS,
[TARGET_ARCHITECTURE = keyword,]
FILE = {* | (number[-number][,number[-number]]...)} |
VALUE_CRITERIA,
[TARGET_ARCHITECTURE = keyword,]
FILE = {* | (number[-number][,number[-number]]...)},
PASSWORD {=|:} {* | string}}
This function exports the current security settings (password definitions, file protection levels and security by value criteria) to the sequential file SCROUT. The output in the file SCROUT can be used as ADASCR input in order to import the security definitions into another database.
Note:
If the SCROUT file already exists, the current security
settings are appended to the existing file.
The security definitions may be exported either in mainframe syntax to import them on mainframe platforms (TARGET_ARCHITECTURE=MAINFRAME) or in open systems syntax to import them on opens systems platforms (TARGET_ARCHITECTURE=OPEN_SYSTEMS - this is the default
PASSWORDS,
TARGET_ARCHITECTURE = keyword,
PASSWORD {=|:} {*|string}
The PASSWORDS parameter exports password permission levels (access and update) and the associated file or file list for the given password/passwords.
The TARGET_ARCHITECTURE parameter defines the syntax of the target platform. The following keywords can be used:
| Keyword | Meaning |
|---|---|
| MAINFRAME | Export the defined password/passwords in mainframe syntax. |
| OPEN_SYSTEMS | Export the defined password/passwords in open systems syntax. |
The default TARGET_ARCHITECTURE is OPEN_SYSTEMS.
The PASSWORD parameter specifies the password for which the security settings have to be exported. It is also possible to export all defined passwords in the database - this can be done by specifying an asterisk for this parameter.
adascr: export=passwords,target_architecture=open_systems,password=09CD09CD %ADASCR-I-PWEXP, Password 09CD09CD and its access and update levels successfully exported.
Note:target_architecture=open_systems is optional and
can be omitted.
This results in the following output for SCROUT:
INSERT=09CD09CD,FILE=(9,12,13),ACCESS=(13,13,13),UPDATE=(13,13,13)
adascr: export=passwords,target_architecture=mainframe,password=09CD09CD %ADASCR-I-PWEXP, Password 09CD09CD and its access and update levels successfully exported.
This results in the following output for SCROUT:
ADASCR INSERT PW=09CD09CD,FILE=9,ACC=13,UPD=13 ADASCR FILE=12,ACC=13,UPD=13 ADASCR FILE=13,ACC=13,UPD=13
PROTECTIONS,
TARGET_ARCHITECTURE = keyword,
FILE = {*|(number[-number][,number[-number]]…)}
The PROTECTIONS parameter exports the protection levels of the given file, file range or ranges.
The TARGET_ARCHITECTURE parameter defines the syntax of the target platform. The following keywords can be used:
| Keyword | Meaning |
|---|---|
| MAINFRAME | Export the defined password/passwords in mainframe syntax. |
| OPEN_SYSTEMS | Export the defined password/passwords in open systems syntax. |
The default TARGET_ARCHITECTURE is OPEN_SYSTEMS.
The FILE parameter specifies the files for which protection levels are to be exported.
adascr: export=protections,file=(9,11,13) %ADASCR-I-PREXP, Protection settings for file 9 successfully exported. %ADASCR-I-PREXP, Protection settings for file 11 successfully exported. %ADASCR-I-PREXP, Protection settings for file 13 successfully exported.
This results in the following output for SCROUT:
PROTECT=9,ACCESS=9,UPDATE=9 PROTECT=9,NAME=(**,AC,AD,BC),ACCESS=(0,14,14,14),UPDATE=(0,14,14,14) PROTECT=9,NAME=(FC,FD,IC,ID),ACCESS=(14,14,14,14),UPDATE=(0,0,0,0) PROTECT=11,ACCESS=1,UPDATE=2 PROTECT=11,NAME=(**,AA,AC,AE),ACCESS=(0,6,3,5),UPDATE=(0,9,9,7) PROTECT=11,NAME=(AD,AI,AJ,AK),ACCESS=(4,10,10,10),UPDATE=(8,12,12,12) PROTECT=11,NAME=(AL,AR,AS,AT),ACCESS=(10,7,7,7),UPDATE=(12,9,9,9) PROTECT=11,NAME=(AX,AY,AZ),ACCESS=(11,11,8),UPDATE=(13,13,10) PROTECT=13,ACCESS=13,UPDATE=13 PROTECT=13,NAME=(**),ACCESS=(0),UPDATE=(0)
adascr: export=protections,target_architecture=mainframe,file=11 %ADASCR-I-PREXP, Protection settings for file 11 successfully exported.
This results in the following output for SCROUT:
ADASCR PROTECT FILE=11,ACC=1,UPD=2 ADASCR PROTECT FILE=11,NAME=(AA,AC,AE,AD),ACC=(6,3,5,4),UPD=(9,9,7,8) ADASCR PROTECT FILE=11,NAME=(AF,AG,AH,AI),ACC=(0,0,0,10),UPD=(0,0,0,12) ADASCR PROTECT FILE=11,NAME=(AJ,AK,AL,AN),ACC=(10,10,10,0),UPD=(12,12,12,0) ADASCR PROTECT FILE=11,NAME=(AM,AO,AP,AR),ACC=(0,0,0,7),UPD=(0,0,0,9) ADASCR PROTECT FILE=11,NAME=(AS,AT,AU,AV),ACC=(7,7,0,0),UPD=(9,9,0,0) ADASCR PROTECT FILE=11,NAME=(AX,AY,AZ),ACC=(11,11,8),UPD=(13,13,10)
VALUE_CRITERIA,
TARGET_ARCHITECTURE = (keyword [,keyword]),
FILE = {*|(number[-number][,number[-number]]…)},
PASSWORD {=|:} {*|string}
The VALUE_CRITERIA parameter exports defined security-by-value settings for a specific file, for the password specified by ‘string’.
The TARGET_ARCHITECTURE parameter defines the syntax and also the byte order of the target platform. The following keywords can be used:
| Keyword Group | Valid Keywords |
|---|---|
| Syntax | MAINFRAME OPEN_SYSTEMS |
| Byte Order | HIGH_ORDER_BYTE_FIRST LOW_ORDER_BYTE_FIRST |
The default TARGET_ARCHITECTURE is OPEN_SYSTEMS.
The default byte order corresponds to the architecture of the machine on which ADASCR is running.
Note:
If you export security-by-value definitions from open systems
to mainframe platforms, a warning will be issued if the search buffer contains
W-formatted fields. This is because W-formatted fields are not supported on
mainframe platforms in security-by-value definitions. Any search buffer that
contains W-formatted fields will not be exported.
The FILE parameter specifies the file list or range(s) of files for which security-by-value definitions are to be exported. Multiple specifications of the same file number are not permitted.
The PASSWORD parameter specifies the password for which security-by-value definitions are to be exported. If you specify an asterisk, the export will be for all defined passwords.
adascr: export=value_criteria,file=9,PASSWORD=* There are no value criteria defined for password "000009CD" There are no value criteria defined for password "00110203" There are no value criteria defined for password "00110304" There are no value criteria defined for password "00110506" There are no value criteria defined for password "00110809" There are no value criteria defined for password "09CD0000" %ADASCR-I-SBVEXP, Security by value settings on file 9 for password 09CD09CD succ essfully exported.
This results in the following output for SCROUT:
SECURITY_BY_VALUE=09CD09CD,FILE=9,ACCESS_CRITERION,SEARCH_BUFFER=CA,1,EQ,O,CA,1,E Q. VALUE_BUFFER=AU UPDATE_CRITERION,SEARCH_BUFFER=CA,1,EQ. VALUE_BUFFER=U
adascr: export=protections,target_architecture=mainframe,file=11 %ADASCR-I-PREXP, Protection settings for file 11 successfully exported.
This results in the following output for SCROUT:
ADASCR PROTECT FILE=11,ACC=1,UPD=2 ADASCR PROTECT FILE=11,NAME=(AA,AC,AE,AD),ACC=(6,3,5,4),UPD=(9,9,7,8) ADASCR PROTECT FILE=11,NAME=(AF,AG,AH,AI),ACC=(0,0,0,10),UPD=(0,0,0,12) ADASCR PROTECT FILE=11,NAME=(AJ,AK,AL,AN),ACC=(10,10,10,0),UPD=(12,12,12,0) ADASCR PROTECT FILE=11,NAME=(AM,AO,AP,AR),ACC=(0,0,0,7),UPD=(0,0,0,9) ADASCR PROTECT FILE=11,NAME=(AS,AT,AU,AV),ACC=(7,7,0,0),UPD=(9,9,0,0) ADASCR PROTECT FILE=11,NAME=(AX,AY,AZ),ACC=(11,11,8),UPD=(13,13,10)
This example shows how to export existing security settings of a Windows Adabas database 33 in order to subsequently import them into a UNIX Adabas database 34.
The export function of ADASCR is used as follows:
>adascr db=33 export=passwords,password=* %ADASCR-I-STARTED, 12-JAN-2017 16:17:29, Version 6.5.1.0 (Windows 64Bit) %ADASCR-I-DBON, database 6 accessed online %ADASCR-I-PWEXP, Password 000009CD and its access and update levels successfully exported. %ADASCR-I-PWEXP, Password 00110203 and its access and update levels successfully exported. %ADASCR-I-PWEXP, Password 00110304 and its access and update levels successfully exported. %ADASCR-I-PWEXP, Password 00110506 and its access and update levels successfully exported. %ADASCR-I-PWEXP, Password 00110809 and its access and update levels successfully exported. %ADASCR-I-PWEXP, Password 09CD0000 and its access and update levels successfully exported. %ADASCR-I-PWEXP, Password 09CD09CD and its access and update levels successfully exported. %ADASCR-I-TERMINATED, 12-JAN-2017 16:17:30, elapsed time: 00:00:01 >adascr db=33 export=protections,file=(9,11) %ADASCR-I-STARTED, 12-JAN-2017 16:17:55, Version 6.5.1.0 (Windows 64Bit) %ADASCR-I-DBON, database 6 accessed online %ADASCR-I-PREXP, Protection settings for file 9 successfully exported. %ADASCR-I-PREXP, Protection settings for file 11 successfully exported. %ADASCR-I-TERMINATED, 12-JAN-2017 16:17:55, elapsed time: 00:00:00 D:\ada_build\ada\v6_5>adascr db=33 export=value_criteria,file=9,password=* %ADASCR-I-STARTED, 12-JAN-2017 16:18:30, Version 6.5.1.0 (Windows 64Bit) %ADASCR-I-DBON, database 33 accessed online adascr: target_architecture=(open_systems,high_order_byte_first) adascr: file=9 adascr: password=09CD09CD %ADASCR-I-SBVEXP, Security by value settings on file 9 for password 09CD09CD succ essfully exported. adascr: q %ADASCR-I-TERMINATED, 12-JAN-2017 16:19:46, elapsed time: 00:01:16
The file “scrout.txt” can now be edited as required, for example, to secure more files other than the ones exported with the given password.
Now copy the exported text file “scrout.txt” to the desired target platform, in this case to a UNIX platform. Import the exported security settings using ADASCR with the following statement:
>adascr db=34 + < scrout.txt %ADASCR-I-STARTED, 12-JAN-2017 17:16:59, Version 6.5.1.0 (Solaris 64Bit) %ADASCR-I-DBON, database 34 accessed online %ADASCR-I-PWINS, password "000009CD" inserted %ADASCR-I-PWINS, password "00110203" inserted %ADASCR-I-PWINS, password "00110304" inserted %ADASCR-I-PWINS, password "00110506" inserted %ADASCR-I-PWINS, password "00110809" inserted %ADASCR-I-PWINS, password "09CD0000" inserted %ADASCR-I-PWINS, password "09CD09CD" inserted %ADASCR-I-FILPRO, protections (access 9, update 9) set for file 9 %ADASCR-I-FIELDPRO, protections (access 0, update 0) set for field ** in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 14) set for field AC in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 14) set for field AD in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 14) set for field BC in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 0) set for field FC in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 0) set for field FD in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 0) set for field IC in file 9 %ADASCR-I-FIELDPRO, protections (access 14, update 0) set for field ID in file 9 %ADASCR-I-FILPRO, protections (access 1, update 2) set for file 11 %ADASCR-I-FIELDPRO, protections (access 0, update 0) set for field ** in file 11 %ADASCR-I-FIELDPRO, protections (access 6, update 9) set for field AA in file 11 %ADASCR-I-FIELDPRO, protections (access 3, update 9) set for field AC in file 11 %ADASCR-I-FIELDPRO, protections (access 5, update 7) set for field AE in file 11 %ADASCR-I-FIELDPRO, protections (access 4, update 8) set for field AD in file 11 %ADASCR-I-FIELDPRO, protections (access 10, update 12) set for field AI in file 1 1 %ADASCR-I-FIELDPRO, protections (access 10, update 12) set for field AJ in file 1 1 %ADASCR-I-FIELDPRO, protections (access 10, update 12) set for field AK in file 1 1 %ADASCR-I-FIELDPRO, protections (access 10, update 12) set for field AL in file 1 1 %ADASCR-I-FIELDPRO, protections (access 7, update 9) set for field AR in file 11 %ADASCR-I-FIELDPRO, protections (access 7, update 9) set for field AS in file 11 %ADASCR-I-FIELDPRO, protections (access 7, update 9) set for field AT in file 11 %ADASCR-I-FIELDPRO, protections (access 11, update 13) set for field AX in file 1 1 %ADASCR-I-FIELDPRO, protections (access 11, update 13) set for field AY in file 1 1 %ADASCR-I-FIELDPRO, protections (access 8, update 10) set for field AZ in file 11 %ADASCR-I-SEVINS, Value criteria for file 9 added to password "09CD09CD" %ADASCR-I-TERMINATED, 12-JAN-2017 17:17:00, elapsed time: 00:00:01
You can check the imported security settings with the DISPLAY control parameter of ADASCR:
adascr
adascr: dbid=34 display=passwords
List of defined passwords for Database 34 ("GENERAL_DATABASE")
MYSECRET
Total of 1 defined password
adascr: dbid=34 display=permissions,password=MYSECRET
password : "MYSECRET"
FILE | ACCESS | UPDATE
-----------------------
1 | Y | Y
2 | Y | Y
3 | Y | Y
9 | (Y) | (Y)
11 | N | N
12 | (Y) | (Y)
13 | (Y) | (Y)
14 | N | N
-----------------------
( ) Further value restrictions apply where brackets shown.
adascr: db=34 display=protections,file=(9,12,13)
FILE | ACCESS | UPDATE
-----------------------
9 | 7 | 11
12 | 2 | 2
13 | 4 | 4
-----------------------
adascr: db=34 display=value_criteria,password=MYSECRET
password : "MYSECRET"
| File | Security by Value criterion
|------+----------------------------------------------------------------------
| 9 | ACCESS_CRITERION
| | SEARCH_BUFFER: "AZ,2,GE."
| | VALUE_BUFFER: "FR"
| | UPDATE_CRITERION
| | SEARCH_BUFFER: "AH,8,GE,D,AH,8,LE,D,AA,8,LE. "
| | VALUE_BUFFER: "195201011952020160000000"
| 12 | ACCESS_CRITERION
| | SEARCH_BUFFER: "AM,3,GE."
| | VALUE_BUFFER: 0x33000C
| | UPDATE_CRITERION
| | SEARCH_BUFFER: "AM,3,GE."
| | VALUE_BUFFER: 0x50000C
| 13 | ACCESS_CRITERION
| | SEARCH_BUFFER: "B0,GE."
| | VALUE_BUFFER: 0x01000000
| | UPDATE_CRITERION
| | SEARCH_BUFFER: "B0,3,GE."
| | VALUE_BUFFER: 0xFF0201
|-----------------------------------------------------------------------------
INSERT {=|:} string, FILE = (number[-number][,number[-number]]...)
,ACCESS = (number[,number]...)
,UPDATE = (number[,number]...)
This function inserts a password specified by 'string' into the password table.
If you specify an equals sign, the value given for 'string' will be converted to upper case; if you specify a colon, no upper-case conversion is performed.
The password may be between 1 and 8 characters long. If less than 8 characters are specified, trailing blanks are added. The password may not contain any special characters or embedded blanks.
The ACCESS parameter specifies the access protection levels to be associated with the files or file ranges specified in the FILE parameter. Each protection level corresponds to one file or one file range. A value may be specified in the range 0 - 14. The protection levels must be specified in the same order as the corresponding files or file ranges in the FILE parameter.
The FILE parameter specifies the file list or range(s) of files for which permission levels are being provided. Multiple specifications of the same file number are not permitted.
The UPDATE parameter specifies the update protection levels to be associated with the files or file ranges specified in the FILE parameter. Each protection level corresponds to one file or one file range. A value may be specified in the range 0 - 14. The protection levels must be specified in the same order as the corresponding files or file ranges in the FILE parameter.
adascr: insert=userpwx, file=(1,2,3),
access=(7,7,7), update=(0,8,8)
adascr: insert=userpwy, file=(1,2,3),
access=(7,2,2), update=(8,0,0)
adascr: insert=userpwz, file=(1-3,5),
access=(2,3), update=(4,6)
PROTECT = (number[-number][,number[-number]]...)
[,NAME = (field_name [, field_name] …)]
,ACCESS = (number[,number]...)
,UPDATE = (number[,number]...)
This function inserts (or updates) the access and/or update protection levels for the file(s) specified or for fields within a file:
If NAME is not specified, file protection levels are defined. Multiple specifications of the same file number are not allowed.
If NAME is specified, field protection levels are defined. Specifying NAME is only allowed, if a single file number has been specified. Multiple specifications of the same field name are not allowed. If the name of a group or a periodic group is specified, the specified field protection levels are set for all component fields of the group / periodic group, which are not specified themselves in the list of field names. For fields not specified explicitly or implicitly as component of a group or periodic group, the field protection levels are not changed.
Default for file and field protection level is access protection level 0 and update protection level 0.
Values may be specified in the range 0 - 15.
If NAME is not specified, the UPDATE parameter specifies the update protection levels to be associated with the file(s) specified in the PROTECT parameter. Each protection level corresponds to one file or one file range. The protection levels must be specified in the same order as the corresponding files or file ranges in the PROTECT parameter. The number of values specified must be identical to the number of files or file ranges in the PROTECT parameter.
If NAME is specified, the UPDATE parameter specifies the update protection levels to be associated with the fields specified via NAME. Each protection level corresponds to one field name. If you set the protection level lower than that of the file, the file protection level becomes effective field protection level. The protection levels must be specified in the same order as the corresponding field names in the NAME parameter. The number of values specified must be identical to the number of field names in the NAME parameter.
Note that the maximum protection level for update for the INSERT function is 14, whereas the PROTECT function allows a maximum of 15. Therefore, with UPDATE=15, a file or field can be protected to prevent any user from updating it.
Values may be specified in the range 0 - 15.
If NAME is not specified, the ACCESS parameter specifies the access protection levels to be associated with the file(s) specified in the PROTECT parameter. Each protection level corresponds to one file or one file range. The protection levels must be specified in the same order as the corresponding files or file ranges in the PROTECT parameter. The number of values specified must be identical to the number of files or file ranges in the PROTECT parameter.
If NAME is specified, the ACCESS parameter specifies the access protection levels to be associated with the fields specified via NAME. Each protection level corresponds to one field name. If you set the protection level lower than that of the file, the file protection level becomes effective field protection level. The protection levels must be specified in the same order as the corresponding field names in the NAME parameter. The number of values specified must be identical to the number of field names in the NAME parameter.
Note that the maximum protection level for access for the PROTECT function is 15, whereas the INSERT function allows a maximum of only 14. Therefore, with ACCESS=15, a file or field can be protected to prevent any user from accessing it.
adascr: protect=25,access=7,update=11 adascr: protect=25,name=(AA,AB,AC),access=(6,8,7),update=(14,13,12) adascr: protect=(1,2,3),access=(7,7,7),update=(8,8,8) adascr: protect=(4-6),access=10,update=12
In the second example, assume that AA is an elementary field, and AB is a group consisting of elementary fields AC, AD and AE. Then the following table shows the resulting protection levels:
| Field AA | Group AB | |||
|---|---|---|---|---|
| Field AC | Field AD | Field AE | ||
| Access protection level | 6 | 7 | 8 | 8 |
| Update protection level | 14 | 12 | 13 | 13 |
If the file number of a security-protected file is subsequently changed as a result of running the RENUMBER function of the ADADBM utility, the PROTECT function has to be reexecuted in order to reestablish the security protection levels for the file. The passwords also have to be reestablished, since they reflect the old file number.
SECURITY_BY_VALUE {=|:} string, FILE = number
,ACCESS_CRITERION
,SEARCH_BUFFER = string *
,VALUE_BUFFER = string *
,UPDATE_CRITERION
,SEARCH_BUFFER = string *
,VALUE_BUFFER = string *
* The search/access buffer string parameters must be followed by <Newline> with no preceding comma.
This function inserts (or updates) the Security by Value criteria for a specific file, for the given password specified by `string'. The password must already have been inserted into the security file, using the INSERT function. Each password can have Security by Value criteria defined for a maximum of 99 files.
If you specify an equals sign, the value given for 'string' will be converted to upper case; if you specify a colon, no upper-case conversion is performed.
The ACCESS_CRITERION keyword must precede the search buffer and value buffer which will define the criterion for restricting access to data using the provided password.
In order for the access value criterion to be specified, the ACCESS password permission level for the file must also have previously been set (i.e. non-zero); in the case where the level is not set, the ACCESS_CRITERION keyword cannot be specified.
The FILE parameter specifies the file for which the value criteria are to be defined. Exactly one file must be specified and the file must be currently loaded in the database.
The UPDATE_CRITERION keyword must precede the search buffer and value buffer which will define the criterion for restricting the update of data using the provided password.
In order for the update value criterion to be specified, the UPDATE password permission level for the file must also have previously been set (i.e. non-zero); in the case where the level is not set, the UPDATE_CRITERION keyword cannot be specified.
The SEARCH_BUFFER parameter is used to provide the search expressions for the access/update criterion. Syntax and examples of search buffer construction are provided in Command Reference, Calling Adabas, Search and Value Buffers.
Certain restrictions apply to the search buffer when used for defining Security by Value criteria; soft coupling and sub-, super-, hyper- and phonetic descriptors are not supported.
If the required criterion is that no restrictions should apply, then the associated search buffer should be specified containing only the terminator, i.e.:
SEARCH_BUFFER = .
In this case, the VALUE_BUFFER parameter is not required and does not need to be supplied.
The VALUE_BUFFER parameter is used to provide the corresponding values for the search expressions for the access/update value criterion, specified in the preceding search buffer. The string may be specified either directly, as an alphanumeric string or as a string using hexadecimal notation.
adascr: security_by_value=fortytwo, file=10,
access_criterion, search_buffer=CA,4,U,LT.
adascr: value_buffer=1707
adascr: update_criterion, search_buffer=A,4,S,CA,4,D,AA,O,AA.
adascr: value_buffer=01001599MS
adascr: security_by_value=g6mon, file=3 adascr: access_criterion, search_buffer=. adascr: update_criterion, search_buffer=AC,3. adascr: value_buffer=HAM
If the either the access or update protection level for the specified file is zero, the associated value criterion will not be tested when the password is used for accessing/updating records for that file.