This document covers the following topics:
The security solutions for your distributed applications using EntireX are described below.
EntireX Security
This is Software AG's standard security solution providing user authentication and user authorization, delivered with EntireX.
Most organizations that use EntireX choose EntireX Security instead of sample security exits for EntireX Broker security.
If your organization is deploying
distributed computer systems encompassing mainframe, UNIX and Windows
environments, you will use EntireX Security instead of sample security exits
for EntireX Broker security.
Sample Security Exits for Broker
This is an alternative, user-written security solution for use only in
exceptional processing situations.
SSL/TLS and Certificates with EntireX
For encrypted transport we strongly recommend using the Secure Sockets Layer/Transport Layer Security protocol. See SSL/TLS and Certificates with EntireX.
| Security Choice | Criteria for Choosing a Security Solution |
|---|---|
| EntireX Security | Choose this option if you want to use the standard security
functionality already provided with EntireX and your organization
uses one of the following security repositories:
The major advantages of EntireX Security:
|
| Sample Security Exits for Broker Security | Choose this option only if your organization requires an
alternative to standard SAF-based security on z/OS or local UNIX / Windows
security on these platforms.
Writing sample security exits is recommended only in exceptional processing situations - for example, if your organization wants to access its own user-written security system when operating EntireX Broker. Sample security exits are provided as skeleton programs only and must be completely customized before they can be deployed. |
| SSL/TLS and Certificates with EntireX | For encrypted transport we strongly recommend using the Secure Sockets Layer/Transport Layer Security protocol. |
Notes:
This diagram shows the locations where the broker kernel and broker stubs can be installed; it also shows the locations of the security components of the kernel and stubs.
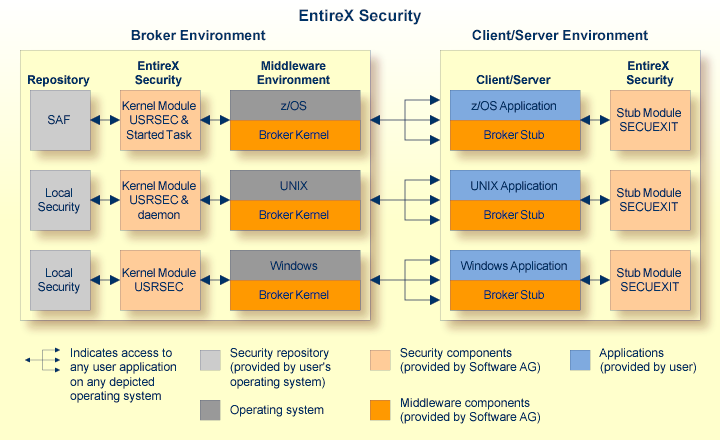
The List of Components per Platform shows where broker kernel and stubs are supported.
This diagram shows the locations where the broker kernel and broker stubs can be installed; it also shows the locations of the security components of the kernel and stubs.
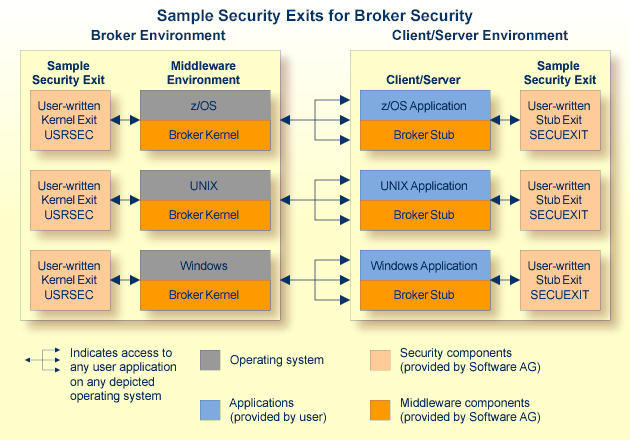
The List of Components per Platform shows where broker kernel and stubs are supported.