This document covers the following topics:
The EntireX Adapter uses adapter services to send synchronous or asynchronous requests to various back-end systems. Access to these systems can be secured in the following ways:
Provide security credentials in the adapter connection for
security-protected back-end systems
If access to a back-end system is security protected, security
credentials (user ID and password) have to be provided in the corresponding
adapter connection. This can be done when the connection is configured or
edited, see EntireX Adapter Connections. This security support is optional and not
available for all connection types, see the overview of available connection
parameters in Editing Adapter Connections.
The credentials can also be provided dynamically when calling the adapter service, see EntireX Adapter Services.
Set access control permissions for the adapter service
Using the Designer you can set access control
permissions to restrict the right to execute an adapter service to a particular
user group of the Integration Server:
![]() To set access control permissions using the
Designer
To set access control permissions using the
Designer
Choose Service Development > Package Navigator > Permissions.
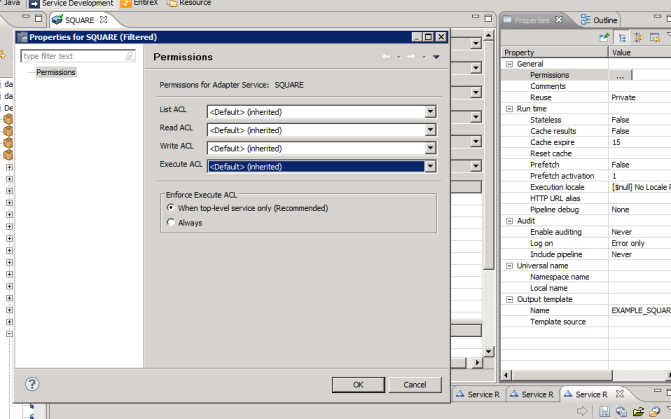
Set Enforce Execute ACL to When top-level service only to select the group that is specified on the top-level service. This way, access control is already checked when executing the top-level service.
Or:
Set Enforce Execute ACL to
Always and select a user group in Execute
ACL.
Adapter listeners receive synchronous or asynchronous requests from external RPC clients. If the RPC request is sent to the EntireX Adapter using a broker that is configured to use security, the credentials of the RPC clients are checked to see if the client is permitted to call the adapter listener.
By enabling the listener property Execute Service with Client Credentials, an adapter listener can be configured to use the credentials (user ID and password) provided by the RPC client to execute the Integration Server service:
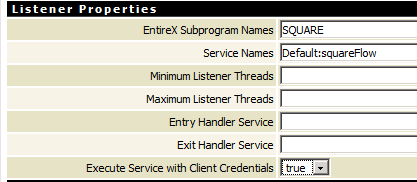
Then the RPC client has to provide credentials (RPC user ID and RPC password) which are used to execute the Integration Server service. Note that currently the RPC user ID and password are limited to eight characters.
Communication between the Adapter and the back-end systems is done using TCP/IP or, for secure communication, SSL/TLS. The configuration of SSL depends on the connection type:
| Connection Type | Description |
|---|---|
| Connection types using the EntireX Broker | Use the URL-style syntax by which Broker IDs are defined to
select SSL as transport method and to define the SSL parameters. For example:
ssl://host:1958?definition_of_sslparameters.
The syntax for defining SSL parameters is described in the notes below.
|
| IMS Connect and CICS ECI | Specify the SSL port in the Port property and the SSL parameters in the SSL Parameters property as described in Editing a Connection. The syntax for defining SSL parameters is described in the notes below. |
| Direct RPC | Specify the SSL port and SSL parameters in the configuration wizard for Direct RPC. |
Notes:
trust_store=file, where
file is the path name of a Java keystore file that
contains the list of trusted certificate authorities. Specify
verify_server=no if you do not want to check that the certificate
of the SSL server is issued for the specified hostname. Example:
ssl://host:1958?trust_store=/temp/ExxCACert.jks&verify_server=no
key_store=file and
key_passwd=pwd. Again,
file is the path name of a Java keystore file that
contains the private key and pwd is the password
that is needed to access the private key entry in the keystore. Example:
ssl://host:1958?trust_store=/temp/ExxCACert.jks&key_store=/temp/ExxJavaAppCert.jks&key_passwd=ExxJavaAppCert