Software AG's webMethods suite of products has a common authentication infrastructure called SIN. It provides the products with security components for authentication of users, management of roles, and query of user, role, and group information. It works both on client-side applications and on server-side applications.
SIN's basic advantage is the re-use of existing security components. For example, SIN supports the same security mechanism for an application that uses Tamino and another one that uses LDAP directory without any change of code on the application level.
SIN is based on the Java Authentication and Authorization Service (JAAS).
The JAAS framework allows you to define stacks of
LoginModules that can be defined without code
changes.
SIN is distributed as part of Software AG Common Platform. It consists of a set of bundles located in: <installDir>/common/runtime/agent/repository/plugins SIN bundle names start with com.softwareag.security.sin.
All interfaces and common classes used by an application programmer are
contained in
com.softwareag.security.sin.common_<versionNumber>.jar.
The other SIN files contain LoginModules and OSGi
services that you can configure according to your environment and the desired
authentication process.
SIN's functionality enables you to have the following set of capabilities:
Provide JAAS support
Authenticate users
Retrieve group and role information for the authenticated user
Retrieve roles for arbitrary users from a role repository
Manage roles in a role repository
The authentication "tool" of SIN is the
LoginModules.
They are based on the Oracle JAAS framework, which is a security
framework for authenticating users. JAAS accommodates the information for
groups and roles in classes derived from
java.security.Principal. The API is integrated in JDK
since version 1.4.
With JAAS, you have the following benefits:
Authentication is independent from applications
Professional services do not need special know-how to customize and re-use standard components for different authentication schemes
Products have a high level of integration and can accommodate customer environments and requirements at install time
The process of authentication includes the successful calling of a
LoginModule.
LoginModules can prompt for and verify a user name
and a password. If authentication is successful, JAAS creates a
Subject that contains one or more
Principals with security-related attributes like
passwords and cryptographic keys.
A particular application defines a LoginModules
configuration that is instantiated from the application. The configuration
specifies the LoginModule that is to be used with a
particular application.
LoginContext?
The LoginContext is a grouping of
LoginModules. It provides the basic methods for user
authentication. The stack of login modules allows you to configure applications
to use more than one LoginModule. For example, you can
configure both a KerberosLoginModule and an
X500LoginModule.
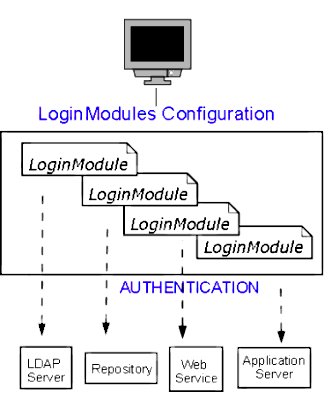
The LoginContext locates the JAAS configuration
file of the appropriate LoginModule.
The application uses the configuration file to authenticate the user.
After the application has authenticated the user, the
LoginContext creates Principals
and adds them to the Subject.
Principal and a
Subject?
The Principal interface represents the abstract
notion of a principal that can be any entity, such as an individual, a
corporation, and a logon ID, while the Subject class
represents a grouping of related information for a single entity. Such
information includes the Subject's identities, as well
as its security-related attributes (passwords and cryptographic keys).
For example, if a Subject is a person named
"John", he may have two Principals:
Principal 1
It represents "John" as the citizen of a particular country.
Principal 2
It represents "John" as the employee of a particular company.
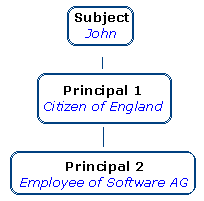
Both Principals refer to the same Subject even
though each has a different name.