The basic idea of security is to establish a secure connection between a server and a client so that reliable messages can be exchanged. According to the requirements of the system, this exchange of messages is designed for two types of authentication:
Authentication of the client to the server
Authentication of the server to the client
System Management Hub's functionality includes authentication for accessing the managed distributed systems. This authentication is necessary to start and execute the required services.
System Management Hub, with its n-tier architecture, distinguishes between several security levels.
This document covers the following topics:
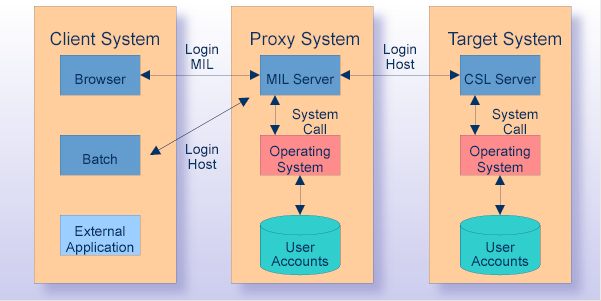
This is the first level of user authentication to provide access to the generic System Management Hub's proxy system. When you work under web or batch interface, you must provide valid user information (usually a user name and a password) for an existing user account on the proxy machine (on which the appropriate MIL server is running).
The MIL server is responsible for verifying that the user information is registered on that machine. It uses the machine's operating system-specific (native) method. There are also other validation methods that can be configured by the system administrator. For details, see the sections Product Security and Registry Settings.
Validation can be disabled at this level but this is not recommended except for testing purposes.
When you log on to the MIL, you establish a connection and create a session. Otherwise, no work with the system is possible.
After a connection with the MIL server has been established, authentication is performed on the target machine on which you install the server-side components of System Management Hub.
System Management Hub's Client/Server Layer Server is responsible for verifying that the user information provided (usually a user name and a password) is actually registered on that machine, using that machine's operating system-specific (native) method. There are also other validation methods available that can be configured by the system administrator. See the sections Product Security and Registry Settings.
If logging on to the target host is successful, a connection is established and it is possible to run the agents on it, to display products, and to manage System Management Hub. The product itself is then capable of setting up additional specific validations (see the next paragraph).
Product security is specific to each managed host. By default, the installation procedure creates an initial System Management Hub administrator. To see how to create new administrators or assign administrator rights to other users, see Defining New Administrators.
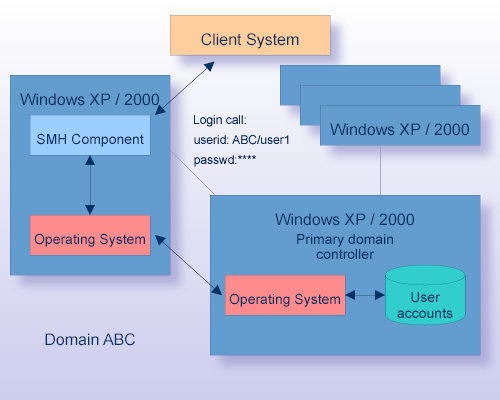
Authentication on Windows is performed in the same way as on other platforms.
If both the MIL machine and the target machine or only one of them belongs to a Windows domain, you can log on to the domain instead of to the local machine. Use the domain name in the user name string in the standard format: <domain_name>/<userid>. Both, the forward slash "/" and the back slash "\" characters can be used as delimiters.
In order to use Secure Sockets Layer (SSL), you must configure Software AG Runtime to use SSL.
When you configure SSL in Apache, you have a secure HTTPs connection between the client system and the proxy system. To have a secure connection from the proxy system to a product, you need to configure an SSL certificate.
For information on how to create or upload an SSL certificate, see Secure Sockets Layer (SSL) in System Management Hub.
SSX is Software AG' interface that contains functionality for authentication. The interfaces are written in C, and Java. Its components provide support for JAAS.
For details on the SSX module in System Management Hub, see Authentication in System Management Hub.