In CentraSite, access control is enabled through a system of roles and permissions. A permission enables a user to perform a specified operation on a specified object. Permissions also enable users to work with specified parts of the CentraSite Control user interface. A role is a collection of permissions that can be assigned to an individual user or a group. The roles to which you belong and the permissions they includes dictate what portions of the CentraSite Control user interface you see, what objects you can work with, and what operations you can perform.
This section describes how you use permissions and roles to apply access control to the objects in your registry.
A permission enables a user to perform a specified operation on a specified object. Permissions also enable users to work with specified parts of the CentraSite Control user interface. It is largely CentraSite's system of permissions and roles that enables it to manage and maintain the separation of organizations in the registry.
Within CentraSite, there are two basic types of permissions: instance-level permissions and role-based permissions.
Instance-level permissions enable access to one specific instance of an object. They provide very fine-grain control over objects in the registry. You can use an instance-level permission, for example, to give one specific user the ability to modify one particular asset in the catalog. Instance-level permissions are granted directly to individual users or to groups.
Role-based permissions enable access to an entire class of objects or give users the ability to perform certain general operations in CentraSite. Role-based permissions provide coarse-grain control over the objects in the registry. You might use role-based permissions, for example, to allow a group of users to edit all of an organization's assets. Role-based permissions are not granted directly to individual users or groups. Role based permissions are assigned to roles, and the roles are assigned to individual users or groups.
An instance-level permission enables access to:
A specific instance of an object in the registry
A specific folder in the repository
A specific file in the repository
Instance-level permissions are granted at the following levels: View, Modify and Full.
The following table describes the capabilities that each level gives to a user. Note that each level of access inherits the capabilities of the preceding level. That is, each level implicitly includes the lower levels of access. In CentraSite's permission model, it is not possible to give a user delete permission without also giving that user modify permission. The Full permission, which enables a user to delete an object, implicitly gives the user Modify and View permissions as well.
| This permission level... | Enables a specified user or group to do the following... |
|---|---|
| View | Read the object. |
| Modify | Read and edit the object; view the object's instance-level permissions. |
| Full | Read, edit and delete the object; modify the object's instance-level permissions. |
| This permission level... | Enables a specified user or group to do the following... |
|---|---|
| View | Read and browse the folder and its properties. |
| Modify | Read and browse the folder and its properties; create files and subfolders in the folder; view the folder's instance-level permissions. |
| Full | Read and browse the folder and its properties; create files and subfolders in the folder; delete files and subfolders in the folder; modify the folder's instance-level permissions. |
| This permission level... | Enables a specified user or group to do the following... |
|---|---|
| View | Read the file and its properties. |
| Modify | Read and edit the files and its properties; view the file's instance-level permissions. |
| Full | Read and edit the file and its properties; modify the file's
instance-level permissions.
Important: |
You can assign instance-level permissions to the following types of registry and repository objects:
Assets (of any type)
Design/change-time policies
Run-time policies
Report templates
Taxonomies
Repository folders
Repository files
CentraSite grants implicit View permission to all users on the following types of registry objects:
Organizations
Users
Groups
Roles
Design/change-time policies
Taxonomies
The View permission that CentraSite grants to users on these objects is permanent and irrevocable. It cannot be taken away from users through any instance-level or role-based permission.
To assign instance level permissions to registry or repository objects, you must have Full permission on the object itself or belong to a role that includes a permissions that effectively grants you Full access to the object.
By default, a user has implicit (and irrevocable) Full permission on all of the objects that he or she owns. Consequently, the object owner is one user that is always permitted to set the instance-level permissions on an object.
For information about how to set instance-level permissions on registry and repository objects, see the following procedures in the CentraSite user documentation.
| For procedures on... | See this section... |
|---|---|
| Assets | Setting Permissions on an Asset, in the document Using the Asset Catalog |
| Report templates | Setting Permissions on a Report Template, in the document Working with Reports and Report Templates |
| Design/change-time policies | Setting Permissions on a Design/Change-Time Policy, in the section Functional Scope in the document Working with Design/Change-Time Policies |
| Run-time policies | Setting Permissions on a Run-Time Policy, in the document Working with Run-Time Policies |
| Taxonomies | Setting Permissions on a Taxonomy, in the document Taxonomies |
Role-based permissions enable access to an entire set of objects or give users the ability to perform certain operations in CentraSite. Unlike instance-level permissions, which are assigned directly to individual users or groups, role-based permissions are assigned to roles, and roles are assigned to users and groups. You cannot assign a role-based permission to a user or group directly.
There are two basic types of role-based permissions:
Permissions that enable access to areas of the CentraSite Control user interface.
Permissions that enable users to create and/or work with certain types of registry and repository objects.
Some permissions are granted implicitly when you assign other permissions.
These topics are described in the following sections:
Role-based permissions include a set of permissions that enable access to certain features and screen sets in the CentraSite Control user interface. These permissions determine which tabs a user sees in the navigation bar in CentraSite Control. For example, CentraSite will not display the navigation bar's Policies profile to a user unless the user has the "Use the Policy UI" permission. The UI-related permissions also include permissions that enable users to view certain logs and use certain controls in CentraSite Control.
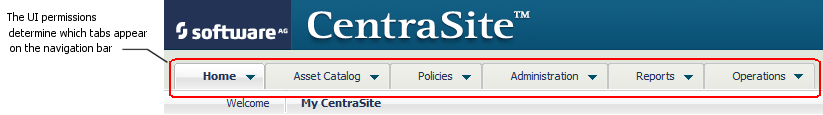
Note:
The user interface permissions apply only to the
CentraSite Control user interface. They do not affect access to
features or screen sets in the CentraSite plug-in for Eclipse.
By default, all CentraSite users have implicit (and irrevocable) permission to use the Asset Catalog area of the CentraSite Control user interface. To use the other parts of the user interface, a user must belong to a role that includes the appropriate user interface permission either explicitly (i.e., the role includes the permission itself) or implicitly (i.e., the role includes a permission that implicitly grants the UI permission). For more information about implicitly granted permissions, see Implication of Additional Permissions.
The following table describes the user interface permissions that are available in each CentraSite edition:
| Available Permissions in CentraSite full-feature edition | Available Permissions in Community Edition |
|---|---|
| Use the Home UI |
|
| Use the Policy UI | |
| Use the Administration UI |
|
| Use the Reports UI |
|
| Use the Operations UI | |
| View Policy Log | |
| View Approval History | |
| Register as Consumer |
|
For a complete description of the user interface permissions, see The Role-Based Permissions in CentraSite.
For more information about CentraSite editions, see the section CentraSite Editions in the document Introducing CentraSite.
Role-based permissions include a second type of permissions that enable users to create and/or work with an entire class of objects.
Generally speaking, these types of role-based permissions grant a specified level of access on objects of a specific type. For example, the "Modify Assets" permission grants Modify-level access on all objects of the type Asset. Role-based permissions enable you to apply access controls over an entire class of objects instead of assigning permissions on each object individually.
If a role-based permission grants access to an object, the name of the permission includes one of the following terms to indicate which level of access the permission provides.
| If the name includes the following term... | The permission grants the following levels of access... |
|---|---|
| View | Read objects of a specified type. This level is equivalent to giving a user View instance-level permission on all objects of a given type. |
| Modify | Read and edit objects of a specified type. This level is equivalent to giving a user Modify instance-level permission on all objects of a given type. |
| Create | Create and read objects of a specified type. This level is equivalent to giving a user View instance-level permission of all objects of a given type and giving them the ability to create new instances of that type. |
| Manage | Create, read, edit, delete and modify the instance-level permission of objects of a specified type. This level is equivalent to giving a user Full instance-level permission of all objects of a given type. |
Be aware that CentraSite does not provide role-based permissions at all levels for all object types. Access to certain objects types can only be granted at the Manage level, for example. For a complete list of the role-based permissions, see Predefined Roles in CentraSite.
Role-based permissions that enable access to objects are either organization-specific or system-wide.
A system-wide permission grants access to objects that are available to all organizations, such as taxonomies and asset types. Additionally, some system-wide permissions grant access to all objects of given type in any organization in the registry/repository.
The following table describes the system-level permissions that are available in each CentraSite edition:
| Available Permissions in CentraSite full-feature edition | Available Permissions in Community Edition |
|---|---|
| Manage Organizations |
|
| Manage System-wide Lifecycle Models | |
| Manage System-wide Design/Change-Time Policies | |
| Manage System-wide Runtime Policies | |
| Manage Report Templates |
|
| Manage System-wide Roles |
|
| Manage UDDI Subscriptions |
|
| Create UDDI Subscriptions |
|
| View UDDI Subscriptions |
|
| Manage Federations | |
| Manage Taxonomies |
|
| Manage Asset Types | |
| Manage Runtime Targets | |
| Manage Runtime Event Types | |
| Manage Supporting Documents |
|
| View Supporting Documents |
|
An organization-specific permission grants a specific level of access to all objects of a given type within a specified organization. Permissions that enable access to assets, policies and lifecycle models are organization-specific.
The following table describes the user interface permissions that are available in each CentraSite edition:
| Available Permissions in CentraSite full-feature edition | Available Permissions in Community Edition |
|---|---|
| Manage Assets |
|
| Create Assets |
|
| Modify Assets |
|
| View Assets |
|
| Manage Design/Change-Time Policies | |
| Manage Run-Time Policies | |
| Manage Lifecycle Models | |
| Manage Users |
|
| Manage Organizations |
|
For a complete description of the system-level and organization-level permissions, see The Role-Based Permissions in CentraSite.
For more information about CentraSite editions, see the section CentraSite Editions in the document Introducing CentraSite.
Most role-based permissions grant additional permissions by implication. That is, the permission grants not only the permission that its name indicates, it grants additional implied permissions.
For example, any permission that grant access to a particular type of object automatically includes (by implication) the UI permissions required to work with that object. Users that belong to roles that include the "Manage Taxonomy" permission, for instance, automatically receive the "Use the Administration UI" permission by implication.
The "Manage Organizations" permission is an example of another permission that grants additional permissions by implication. This permission, when given at the system-level, essentially implies all other role-based permissions. Consequently, a user with "Manage Organizations" permission at the system-level can manage virtually any object in any organization.
For a description of the individual permissions, and the permissions they each imply, see The Role-Based Permissions in CentraSite.
The following table describes the individual permissions and their implied permissions in CentraSite, if any.
| Permission | Scope | Purpose | Implied Permissions |
|---|---|---|---|
| Use the Home UI | System-wide | Grants the right to use the Home area in CentraSite Control. Without this permission the UI will hide the top-level navigation item. | None |
| Use the Policy UI | System-wide | Grants the right to use the Policy area in CentraSite Control. Without this permission the UI will hide the top-level navigation item. | None |
| Use the Administration UI | System-wide | Grants the right to use the Administration area in CentraSite Control. Without this permission the UI will hide the top-level navigation item. | None |
| Use the Reports UI | System-wide | Grants the right to use the Reports area in CentraSite Control. Without this permission the UI will hide the top-level navigation item. | None |
| Use the Operations UI | System-wide | Grants the right to use the Operations area in CentraSite Control. Without this permission, the UI will hide the top-level navigation item. | None |
| View Policy Log | System-wide | Grants the right to view the policy log. | "Use the Administration UI" |
| View Approval History | System-wide | Grants the right to view the approval history. | "Use the Administration UI" |
| Register as Consumer | System-wide | Grants the right to register as a consumer of assets. | None |
| Manage Assets | Organization | Grants the right to manage assets and supporting documents within an organization. | "Create Assets" "Modify Assets" "View Assets" |
| Create Assets | Organization | Grants the right to create new assets within an organization. | None |
| Modify Assets | Organization | Grants the right to modify all
assets and supporting documents within an organization. The "Modify Assets" permission is important not just for applying updates to existing assets but also for performing consumer registrations. |
"View Assets" |
| View Assets | Organization | Grants the right to view all assets and supporting documents within an organization. | None |
| Manage Design/Change-Time Policies | Organization | Grants the right to manage
design/change-time policies within an organization. Additionally, this implies the right to manage all policy-related objects such as policy conditions and policy parameters. Note that there is no explicit permission for viewing design/change-time policies, since design/change-time policies are visible for everyone. |
"Use the Policy UI" |
| Manage Run-Time Policies | Organization | Grants the right to manage
run-time policies within an organization. Additionally, this implies the right to manage all policy-related objects such as policy conditions and policy parameters. Note that there is no explicit permission for viewing run-time policies, since run-time policies are visible for everyone. |
"Use the Policy UI" |
| Manage Lifecycle Models | Organization | Grants the right to manage
lifecycle models (LCMs) within an organization. Note that there is no explicit permission for viewing LCMs, since LCMs are visible for everyone. |
"Use
the Administration UI" "Modify Assets" "Manage Design/Change-Time Policies" "Manage Runtime Policies" |
| Manage Users | Organization | Grants the right to manage users
of an organization. Additionally, this grants the right to manage groups and roles within an organization. |
"Use the Administration UI" |
| Manage Organizations | Organization | Grants the right to manage an
organization and all its child organizations. Also grants the right to manage the organization folder in Supporting Document Library (SDL). By default, the content of an organization folder is visible for every user of that organization. Note that all organizations are visible for everyone. |
"Manage Users" "Manage Design/Change-Time Polices" "Manage Run-Time Policies" "Manage Lifecycle Models" "Manage Assets" |
| Manage Organizations | System-wide | Grants the right to manage all
organizations in the CentraSite instance. Note that all organizations are visible for everyone. |
"Manage
Organizations" (org-level permission for every organization) "Manage System-wide Design/Change-Time Policies" "Manage System-wide Run-Time Policies" "Manage-System-wide Lifecycle Models" "Manage Report Templates" |
| Manage System-wide Lifecycle Models | System-wide | Grants the right to manage
lifecycle models. Note that there is no explicit permission for viewing system-wide lifecycle models, since system-wide lifecycle models are visible for everyone. |
"Use
the Administration UI" "Manage Lifecycle Models" (org-level permission for every organization) "Manage System-wide Design/Change-Time Policies" "Manage System-wide Runtime Policies" |
| Manage System-wide Design/Change-Time Policies | System-wide | Grants the right to manage
design/change-time policies. Additionally, this implies the right to manage the following policy-related objects: • Action Categories • Action Templates • Action Parameters Note that there is no explicit permission for viewing system-wide design/change-time policies, since system-wide design/change-time policies are visible for everyone. |
"Use the Policy UI" |
| Manage System-wide Runtime Policies | System-wide | Grants the right to manage
run-time policies. Additionally, this implies the right to manage the following policy-related objects: • Action Categories • Action Templates • Action Parameters Note that there is no explicit permission for viewing system-wide run-time policies, since system-wide run-time policies are visible for everyone. |
"Use the Policy UI" |
| Manage Report Templates | System-wide | Grants the right to manage
system-wide report templates. Note that there is no explicit permission for viewing system-wide report templates, since system-wide report templates are visible for everyone. |
"Use the Reports UI" |
| Manage System-wide Roles | System-wide | Grants the right to manage
system-level roles. Note that there is no explicit permission for viewing system-wide roles, since system-wide roles are visible for everyone. |
"Use the Administration UI" |
| Manage UDDI Subscriptions | System-wide | Grants the right to manage UDDI Subscriptions. | "Create UDDI
Subscriptions" "View UDDI Subscriptions" |
| Create UDDI Subscriptions | System-wide | Grants the right to create new UDDI Subscriptions and view existing UDDI Subscriptions. | "View UDDI Subscriptions" |
| View UDDI Subscriptions | System-wide | Grants the right to view UDDI Subscriptions. | "Use the Administration UI" |
| Manage Federations | System-wide | Grants the right to manage
federations. Note that there is no explicit permission for viewing federations, since federations are visible for everyone. |
"Use the Administration UI" |
| Manage Taxonomies | System-wide | Grants the right to manage
taxonomies. Note that there is no explicit permission for viewing system-wide taxonomies, since system-wide taxonomies are visible for everyone. |
"Use the Administration UI" |
| Manage Asset Types | System-wide | Grants the right to manage asset
types. Note that there is no explicit permission for viewing asset types, since asset types are visible for everyone. |
"Use the Administration UI" |
| Manage Runtime Targets | System-wide | Grants the right to manage
run-time targets and target types. Note that there is no explicit permission for viewing run-time targets and target types, since run-time targets and target types are visible for everyone. |
"Use the Operations UI" |
| Manage Runtime Event Types | System-wide | Grants the right to mange run-time
event types. Note that there is no explicit permission for viewing run-time event types, since run-time event types are visible for everyone. |
"Use the Operations UI" |
| Manage Supporting Documents | System-wide | Grants the right to manage the content of all folders in the Supporting Documents Library (SDL). | "View Supporting Documents" |
| View Supporting Documents | System-wide | Grants the right to view the content of all folders in the Supporting Documents Library (SDL). | None |
When a user receives multiple permissions for the same object, the permissions are combined and the user receives the union of all the permissions.
For example, if you give a user instance-level View permission on an asset and that user belongs to a role that gives him or her Modify permission on the asset, that user will get View permission plus Modify permission on the asset (or, in effect, Modify permission since it implies View permission).
You will need to keep this concept in mind when granting role-based access to a large group of users (particularly to an entire organization). Anytime you use a role-based permission to give a group of users access to the entire set of assets in an organization, you can no longer use instance-level permissions to reduce the level of access for those users. For example, when everyone in your organization is given "View Assets" permission, you no longer have a way to use instance-level permission to selectively hide assets from certain users in the organization. In effect, the View permission becomes irrevocable for the users in the organization.
A role is a collection of role-based permissions. Assigning a role to a user gives the user the permissions specified in the role. Roles can be assigned to individual users or to groups.
CentraSite provides many predefined roles for you to use. You can also create custom roles as needed.
CentraSite provides many predefined roles. These roles fall into two categories:
System-level roles, which contain permissions for working with system-wide objects (i.e., objects that affect or are available to all organizations). Asset types and taxonomies are examples of system-wide objects.
The following table identifies the predefined system-level roles that are available in each CentraSite edition:
| Available Roles in CentraSite full-feature edition | Available Roles in Community Edition |
|---|---|
| CentraSite Administrator (CSA) |
|
| Asset Type Administrator (ATA) | |
| Operations Administrator (OPA) | |
| Guest (G) |
|
For detailed information about these roles, see System-Level Roles.
Organization-level roles, which contain permissions for working with organization-specific objects (i.e., objects that belong to and are used by one particular organization). Assets, policies and lifecycle models are examples of organization-specific objects. CentraSite maintains a set of organization-level roles for each organization in the registry/repository.
The following table identifies the predefined organization-level roles that are available in each CentraSite edition:
| Available Roles in CentraSite full-feature edition | Available Roles in Community Edition |
|---|---|
| Organization Administrator (OA) |
|
| Asset Administrator (AA) |
|
| Policy Administrator (PA) | |
| Asset Provider (AP) |
|
| Asset Consumer (AC) |
|
For detailed information about these roles, see Organization-Level Roles.
The following table summarizes the permissions that CentraSite assigns to each of the predefined roles by default. Be aware that the permission assignments for most of these roles can be customized by an administrator. If an administrator has customized a predefined role at your site, it might have different permissions than what is shown here.
| Permission | Type | Scope | System-Level Roles | Organization-Level Roles | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| CSA | ATA | OPA | Guest | OA | PA | AA | AP | AC | |||
| Use the Home UI | UI | System-wide |
|
|
|
|
|
|
|
|
|
| Use the Policy UI | UI | System-wide |
|
|
|
|
|||||
| Use the Administration UI | UI | System-wide |
|
|
|
||||||
| Use the Reports UI | UI | System-wide |
|
|
|
|
|
|
|||
| Use the Operations UI | UI | System-wide |
|
|
|||||||
| View Policy Log | UI | System-wide |
|
|
|
|
|
|
|||
| View Approval History | UI | System-wide |
|
|
|
|
|
|
|||
| Register as Consumer | UI | System-wide |
|
|
|
|
|
||||
| Manage Assets | ORG | Organization |
|
|
|||||||
| Create Assets | ORG | Organization |
|
|
|
||||||
| Modify Assets | ORG | Organization |
|
|
|||||||
| View Assets | ORG | Organization |
|
|
|
|
|
||||
| Manage Design/Change-Time Policies | ORG | Organization |
|
|
|||||||
| Manage Run-Time Policies | ORG | Organization |
|
|
|||||||
| Manage Lifecycle Models | ORG | Organization |
|
|
|||||||
| Manage Users | ORG | Organization |
|
||||||||
| Manage Organizations | ORG | Organization |
|
||||||||
| Manage Organizations | SYS | System-wide |
|
||||||||
| Manage System-wide Lifecycle Models | SYS | System-wide |
|
|
|
||||||
| Manage System-wide Design/Change-Time Policies | SYS | System-wide |
|
|
|
||||||
| Manage System-wide Runtime Policies | SYS | System-wide |
|
|
|||||||
| Manage Report Templates | SYS | System-wide |
|
|
|||||||
| Manage System-wide Roles | SYS | System-wide |
|
||||||||
| Manage UDDI Subscriptions | SYS | System-wide |
|
|
|||||||
| Create UDDI Subscriptions | SYS | System-wide |
|
|
|||||||
| View UDDI Subscriptions | SYS | System-wide |
|
|
|||||||
| Manage Federations | SYS | System-wide |
|
||||||||
| Manage Taxonomies | SYS | System-wide |
|
|
|||||||
| Manage Asset Types | SYS | System-wide |
|
|
|||||||
| Manage Runtime Targets | SYS | System-wide |
|
|
|||||||
| Manage Runtime Event Types | SYS | System-wide |
|
|
|||||||
| Manage Supporting Documents | SYS | System-wide |
|
||||||||
| View Supporting Documents | SYS | System-wide |
|
||||||||
The following predefined roles in CentraSite are system-level roles. Generally speaking, these roles contain permissions that enable users to work with system-wide objects. Some of these roles also enable users to manage (view, edit or delete) all instances of a given object type in any organization in the CentraSite registry/repository. For example, a user in the Centrasite Administrator role has, in effect, Full permission on every asset in every organization.
The main characteristic that distinguishes a system-level role from an organization-level role is that a system-level role is not generated for each new organization.
As noted in the following descriptions, some system-level roles can be edited and/or deleted and others cannot.
The CentraSite Administrator role includes all available permissions. Users in this role have all the permissions to manage the complete system (that is, users with "superuser" permissions). The CentraSite Administrator only can change the permission set for a system role. Additionally, the CSA has permission to create and delete a system role. This role cannot be modified or deleted.
Users in the Asset Type Administrator role can manage the type definitions and taxonomies in CentraSite.
Users in the Operations Administrator role can manage the operational aspects of CentraSite. For example, the Runtime Event Types and Runtime Targets.
Users in the Guest role can browse and use the asset catalog.
For a summary of the permissions that CentraSite assigns to these predefined roles by default, see Predefined Roles in CentraSite.
CentraSite automatically populates any new organization that is created with the following organization-level roles and permissions.
Users in the Organization Administrator role can manage objects within a particular organization. This includes all child organizations of that organization. This role cannot be modified or deleted.
Users in the Asset Provider role can create new assets and view assets. This role also has the ability to register users to consume assets.
Users in the Asset Consumer role can view all assets. This role also has the ability to register users to consume assets.
Users in the Asset Administrator role can manage all assets within the organization.
Users in the Policy Administrator role can manage design/change-time and run-time policies within an organization.
Note:
By default, the Asset Provider and Asset Consumer roles are
automatically assigned to the Users group that CentraSite creates for an
organization. Consequently, every user in an organization is assigned these
roles. If you do not want every user in your organization to have these roles
(for example, if you do not want every user to have the Asset Provider role),
edit the role assignments for your organization's Users group. For procedures,
see Assigning Roles to a
Group.
For a summary of the permissions that CentraSite assigns to these predefined roles by default, see Predefined Roles in CentraSite.
You can create custom roles in CentraSite as needed. Custom roles can contain system-level permissions and/or organization-level permissions. A custom role can contain organization-level permissions for multiple organizations (i.e., you can create a role that allows a user to manage the policies in two different organizations). You can also modify many of the predefined organizations that CentraSite installs. For information about which predefined roles can be modified, see the topics System-Level Roles and Organization-Level Roles in the section About Roles and Permissions in the document Users, Groups, Roles and Permissions.
To create and manage (i.e., view, edit and delete) roles for an organization, you must belong to a role that has the "Manage Users" permission for the organization. Users in the Organization Administrator role have this permission, although an administrator can assign this permission to other roles.
Note:
Users that belong to a role that includes the "Manage
Organizations" permission have the "Manage
User" permission by implication. Such users can create and mange
groups in any organization to which their "Manage
Organizations" permission applies.
Be aware that you when you define a role, you cannot assign permissions to the role that you do not have yourself. Therefore, if you belong to the Organization Administrator role (and you have no additional role assignments), you cannot create roles that have any additional permissions than the ones provided by the Organization Administrator role. For example, you could not create a role that included system-level permission or permissions for other organizations. A user with the "Manage Organizations" permission at the system-level (such as someone in the CentraSite Administrator role) would need to do that.
![]() To create a custom role
To create a custom role
In CentraSite Control, go to .
On the Roles page, click .
In the Role Information panel, specify the following fields:
| In this field... | Do the following... |
|---|---|
| Name |
Enter a name for the new role. A role name can contain any character (including spaces). Note: |
| Description |
Optional. Enter a short description for the new role. This description appears when the user displays the list of roles in CentraSite Control. |
| Organization | Specify the organization to which this role belongs. (The drop-down list only displays organizations for which you have "Manage Users" permission.) |
In the Permissions panel, click .
In the Assign Permissions dialog box, do the following
Select the permission(s) that you want to assign to this role. (The list will only contain permissions that you are authorized to assign.)
Click .
Click to create the new custom role in the CentraSite registry/repository.
You use the Edit Role page to examine and/or edit the properties of a role. When viewing or editing a role, keep the following points in mind:
You cannot modify the CentraSite Administrator role.
You cannot modify the Organization Administrator.
![]() To view or edit the properties of a role
To view or edit the properties of a role
In CentraSite Control, go to .
By default, all of the available roles are displayed.
If you want to filter the list to see just a subset of the available roles, type a partial string in the Search field. CentraSite applies the filter to the Name column. The Search field is a type-ahead field, so as soon as you enter any characters, the display will be updated to show only those roles whose name contains the specified characters. The wildcard character "%" is supported.
Locate the role that you want to view or edit.
From the role's context menu, select the Details command.
Examine or modify the attributes on the Edit Role page as necessary.
| Field | Description |
|---|---|
| Name |
The name of the role. A role name can contain any character (including spaces). Note: |
| Description | Additional comments or descriptive information about the role. |
| Organization |
Read-only. The organization to which the role belongs. |
| Permissions | The settings on this profile identify the permissions that are assigned to this role. |
If you want to add or remove permissions to/from the role, select the Permissions profile and do the following:
To add permissions to the role, click and select the permission that you want to add.
To remove permissions from the role, select the permissions that you want to remove and click .
If you have edited the settings on the Edit Role page, click to save the updated role.
You use the Roles page to delete the custom roles. When deleting a role, keep in mind that you cannot delete the CentraSite Administrator role or the Organization Administrator role (not even if you belong to the CentraSite Administrator role).
![]() To delete a role
To delete a role
In the CentraSite Control, go to to display the roles list.
Enable the checkbox next to the name of the role that you want to delete.
Click .
When you are prompted to confirm the delete operation, click .
You can delete multiple roles in a single step. The rules described above for deleting a single role apply also when deleting multiple roles.
Important:
If you have selected several roles where one or more of them
are predefined roles, you can use the button to
delete the roles. However, as you are not allowed to delete predefined roles,
only roles you have permission for will be deleted. The same applies to any
other roles for which you do not have the required permission.
![]() To delete multiple roles in a single operation
To delete multiple roles in a single operation
In CentraSite Control, go to to display the roles list.
Mark the checkboxes of the roles that you want to delete.
From the Actions menu, choose Delete.
When you are prompted to confirm the delete operation, click .