Setting the STS Options
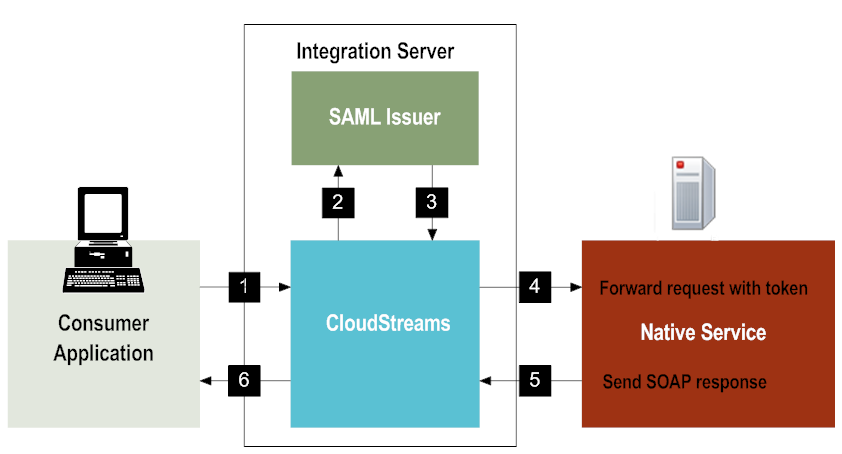
CloudStreams can act as a Security Token Service (STS) client. The following illustration shows what happens at run time.
CloudStreams as an STS Client
Step | Description |
1 | The user's client sends a SOAP request with SAML authentication information to CloudStreams. Integration Server authenticates the incoming request. |
2 |  CloudStreams CloudStreams sends a WS-Trust RST to the STS to request a SAML v2 token.  CloudStreams CloudStreams sends the <OnBehalfOf> element that contains the authenticated user name to the STS. |
3 | The SAML Issuer sends the SAML v1/v2 assertion to CloudStreams. |
4 | CloudStreams forwards the SOAP request (along with the SAML assertion) to the native service. CloudStreams also uses the IS keystore and signing alias you specified to sign the SAML token and the request body before sending the request to the native service. Also, if you have configured the predefined Java service pub.cloudstreams.security.ws.AddSamlSenderVouchesTokento add a timestamp in the outbound request, CloudStreams will sign the timestamp as well. |
5 | The native service sends a SOAP response to CloudStreams. |
6 | CloudStreams sends the response to the user's client. |
Use the following procedure to enable CloudStreams to act as a Security Token Service (STS) client.
To set the CloudStreams > Administration > STS options
1. In Integration Server Administrator, select Solutions > CloudStreams > Administration > STS.
2. You can use Integration Server’s default STS, DefaultSTS. To view its default parameters, click its name.
3. Alternatively, you can to use a third-party STS that has been defined in the Integration Server (as described in the Web Services Developer’s Guide, in the section Securing Web Services Using Policies Based on WS-SecurityPolicy). To use a third-party STS, click Add new STS configuration and complete the Add STS Configuration page as follows.
Option | Description |
Name | A unique name for the STS being configured. If this value is changed after creating an STS, the previous STS configuration will be deleted and replaced with the new one. |
Endpoint | The STS endpoint to which the WS-Trust request will be sent by CloudStreams to obtain the SAML token. |
Token Type | The type of token that CloudStreams should request from the STS. Value can be SAML_11 or SAML_20. Note: | Currently the default Integration Server STS only supports issuing SAML 2.0 Sender-vouches tokens. |
|
WS-Trust Version | The version of WS-Trust that CloudStreams should use to send the RST to the SAML Issuer. Value can be VERSION_05_02 or VERSION_05_12. |
Time-To-Live (TTL) | Indicates the time-to-live value in seconds that will be specified in the RST. If not specified, the default is 300 seconds (5 minutes). |
Keystore | Select a keystore that has been configured in Integration Server. To configure a keystore in Integration Server, see the section Securing Communications with the Server in the document webMethods Integration Server Administrator’s Guide. |
Sign Request?/Signing Alias | Select Sign Request? if the STS requires a signed request, and specify the signing alias in the Signing Alias field. |
Encrypt Request?/Encryption Alias | Select Encrypt Request? if the STS requires an encrypted request, and specify the encryption alias in the Encryption Alias field. |
HTTP Basic Authorization Username/Password | If the STS requires authentication, enter the HTTP Basic Authentication username and password. |
WS-Security Username Token/Username, Password, and Password Type | The WS-Security username token to send to the STS. Also specify the username's password and password type (None, Text or Digest). |
4. If you selected Integration Server’s default STS (DefaultSTS), edit the default STS's configuration file to specify the keystore and alias so that the STS can sign the SAML assertion that it is issuing.
The configuration file is:
IntegrationServer_directory\instances\instance_name\config\security\saml\esb_sts.xml
The contents of the file are shown below. Use the comments as a guide to configure this file for your system.
<?xml version="1.0" encoding="UTF-8"?>
<!-- This configuration file is used to configure the IntegrationServer token
issuer that generates the SAML Sender Vouches token for CloudStreams outbound
requests -->
<IDataXMLCoder version="1.0">
<record javaclass="com.wm.data.ISMemDataImpl">
<!-- IssuerName - will be used as the IssuerName for each SAML token issued by
this Service; the default value is ESB_STS -->
<value name="IssuerName">ESB_STS</value>
<!-- IssuerKeystoreAlias - specify an Integration Server Keystore Alias that
contains the private keys that can be used to sign the generated SAML
Assertion -->
<value name="IssuerKeystoreAlias">STS</value>
<!-- IssuerKeyAlias - the name of the key alias within the
IssuerKeystoreAlias that points to the private key files -->
<value name="IssuerKeyAlias">sts</value>
<!-- TimeToLiveSeconds - how long in seconds the generated token should be
valid? the default is 300 seconds (i.e. 5 minutes) from the time of token
creation -->
<number name="TimeToLiveSeconds" type="java.lang.Integer">300</number>
</record>
</IDataXMLCoder>
5. Configure the desired virtual services so they can use the STS. To do this, write an IS service that includes the predefined Java service pub.cloudstreams.security.ws.AddSamlSenderVouchesTokenand invoke this IS service in the "In Sequence" step of the virtual service. This service must reference an STS that is identified in CloudStreams. For details about the AddSamlSenderVouchesTokenservice, see Using the Security API in IS Services.