pub.security.xml:encryptXML
WmPublic. Encrypt an XML document or node in an XML document.
Input Parameters
xmldata | String Optional. The XML to be encrypted. |
xmlStream | InputStream Optional. Input stream to the XML that needs to be encrypted. Note: | If both xmldata and xmlStream are provided, xmlStream takes precedence. |
|
nodeSelectors | String List XPaths to the node to be encrypted. If the value for this parameter is left empty, no XML will be encrypted. |
nsDecls | Document Optional. Mapping of the namespace prefixes to the namespace URIs. The first column contains the prefixes and the second column contains the corresponding URIs. |
recipientID | String Optional. Name of the client to which the XML will be sent. The user name and certificate must be configured with Integration Server certificate mapping. The client name entry is mapped to a valid X.509 certificate, and both are stored in Integration Server. For information about Integration Server certificate mapping, see webMethods Integration Server Administrator’s Guide. |
recipientCert | Byte[] Optional. The certificate containing the public key that will be used to encrypt the XML. If the input parameters recipientCert and recipientID are both provided, recipientCert is used. |
contentOnly | Boolean Optional. Indicates whether the XML tags surrounding the content will be encrypted along with the content. Set to: 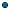 true true to encrypt only the content. 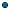 false false to encrypt both the tags and the content. This is the default. |
algorithm | String Optional. The symmetric key algorithm to use for encryption. Set to: 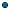 tripledes-cbc tripledes-cbc for the algorithm at http://www.w3.org/2001/04/xmlenc#tripledes-cbc This is the default. 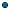 aes256-cbc aes256-cbc for the algorithm at http://www.w3.org/2001/04/xmlenc#aes256-cbc  aes192-cbc aes192-cbc for the algorithm at http://www.w3.org/2001/04/xmlenc#aes192-cbc  aes128-cbc aes128-cbc for the algorithm at http://www.w3.org/2001/04/xmlenc#aes128-cbc Note: | If you are using aes256-cbc or aes192-cbc with JVM 1.6, make sure the unlimited policy jar files have been installed. |
|
encryptedKeyAlgorithm | String Optional. The symmetric key that is randomly generated, and then encrypted with the receiver's public key. This encryption uses an asymmetric algorithm if public/private key pairs are being used. Set to:  rsa-1_5 rsa-1_5 for the algorithm at http://www.w3.org/2001/04/xmlenc#rsa-1_5 This is the default.  rsa-oaep-mgf1p rsa-oaep-mgf1p for the algorithm at http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p |
encoding | String Optional. Specifies the encoding to use if the encoding cannot be extracted from the XML. If encoding is not specified in the XML document or in the encoding parameter, Integration Server uses UTF-8. The encoding value must be a valid IANA encoding. |
Output Parameters
encryptedXMLData | String Conditional. Encrypted XML data. encryptedXMLData is returned when the input parameter xmldata is provided. |
encryptedXMLStream | OutputStream Conditional. Encrypted XML in the form of an OutputSream. encryptedXMLStream is returned when the input parameter xmlStream is provided. |
Usage Notes
If both xmldata and xmlStream are provided, xmlStream takes precedence.
There are several prerequisites to using the pub.security.xml:encryptXML service:
Certificates must be configured for
Integration Server and the client with which it is exchanging encrypted XML.
Before an encrypted XML document can be exchanged between
Integration Server and an external system, the external system must share its public key.
Prior to use of
pub.security.xml:encryptXML,
Integration Server must have access to the partner's public key. Such access is possible through:
An
Integration Server certificate mapping (for information, refer to
webMethods Integration Server Administrator’s Guide).
A copy of the partner's X.509 certificate that is available to
Integration Server.
In pub.security.xml:encryptXML, the certificate/public key is specified through one of the following input parameters: the client's name (through recipientID), or the public key of the partner application (through recipientCert).
Because encryption is a processing-intensive activity, it is recommended to only encrypt the XML nodes requiring protection.
Signing and Encrypting the Same XML Document
You can use both encryption and signing in the same XML document.
If you sign and encrypt
different XML elements in a document, you can run either
pub.security.xml:signXML or
pub.security.xml:encryptXML first.
Typically, if you sign and encrypt the
same XML elements in a document, you should sign the elements before encrypting them. That is, invoke
pub.security.xml:signXML before invoking
pub.security.xml:encryptXML.