Setting up the Server for Kerberos Authentication
Use this procedure to configure the
Software AG common runtime web server to use the configured Active Directory and Kerberos authentication set up on the Windows Server. For details on how to set up the Active Directory and Kerberos authentication on a Windows server, see
Setting up the Windows Server and Active
Directory .
1. Create a krb5.conf file, and insert these Kerberos configuration details:
[libdefaults]
default_realm = <Active_Directory_Realm_Name>
default_tkt_enctypes = arcfour-hmac-md5 rc4-hmac des3-hmac-sha1 des-cbc-crc
default_tgs_enctypes = arcfour-hmac-md5 rc4-hmac des3-hmac-sha1 des-cbc-crc
dns_lookup_kdc = true
dns_lookup_realm = true
[realms]
<Active_Directory_Realm_Name> = {
kdc = <Active_Directory_Machine_with_Domain>
admin_server = <Active_Directory_Machine_with_Domain>
master_kdc = <Active_Directory_Machine_with_Domain>
default_domain = <Active_Directory_Realm_Name>
}
[domain_realm]
.<Active_Directory_Realm_Name> = <Active_Directory_Domain_Name>
[logging]
kdc = SYSLOG:INFO
admin_server = FILE=c:\kadm5.log
Example:
[libdefaults]
default_realm = DEV.RNDLAB.LOC
default_tkt_enctypes = arcfour-hmac-md5 rc4-hmac des3-hmac-sha1 des-cbc-crc
default_tgs_enctypes = arcfour-hmac-md5 rc4-hmac des3-hmac-sha1 des-cbc-crc
dns_lookup_kdc = true
dns_lookup_realm = true
[realms]
DEV.RNDLAB.LOC = {
kdc = MCKDC.DEV.RNDLAB.LOC
admin_server = MCKDC.DEV.RNDLAB.LOC
master_kdc = MCKDC.DEV.RNDLAB.LOC
default_domain = DEV.RNDLAB.LOC
}
[domain_realm]
.DEV.RNDLAB.LOC = DEV.RNDLAB.LOC
[logging]
kdc = SYSLOG:INFO
admin_server = FILE=c:\kadm5.log
2. Verify if the keytab file is created correctly:
a. Copy the krb5.conf file to C:\\Windows drive on the Windows machine where OneData is installed.
b. Change the krb5.conf file name to krb5.ini.
c. Run the following java command from <JAVA_INSTALL>/jre/bin:
kinit -J-Dsun.security.krb5.debug=true -k -t <ABSOLUTE_PATH>/
<Keytab_File_Name>HTTP/<FQDN_of_Active_Directory_Server>
d. On successful verification, delete this copy of the krb5.conf file .
3. On the machine where OneData is installed:
a. Navigate to <Software AG_directory>\profiles\ODE\configuration\tomcat\conf.
b. Open the server.xml and add a new JAASRealm (nested inside the LockOutRealm) to connect to the configured KDC as follows:
<Realm className="org.apache.catalina.realm.JAASRealm" appName="<JAASRealm Name>"
userClassNames="com.softwareag.security.jaas.principals.SagUserPrincipal"
roleClassNames="com.softwareag.security.jaas.principals.SagGroupPrincipal" />
Example:
<Realm className="org.apache.catalina.realm.JAASRealm" appName="ADLdapRealm"
userClassNames="com.softwareag.security.jaas.principals.SagUserPrincipal"
roleClassNames="com.softwareag.security.jaas.principals.SagGroupPrincipal" />
c. Navigate to <Software AG_directory>\profiles\ODE\configuration\com.softwareag.platform.config.propsloader.
d. Add a properties file with the name com.softwareag.jaas.realm.pid-<Active_Directory_Name>.properties.
Example: com.softwareag.jaas.realm.pid-ssoRealm.properties
e. In com.softwareag.jaas.realm.pid-<Realm_Name_for_SSO>.properties, add the required realm properties:
Note: The realm name should be the new JAASRealm name provided in server.xml.
realm=<JAASRealm_Name>
0.option.userrootdn=cn=<Common_Name>,dc=<Domain_Component_1>,dc=<Domain_Component_2>
0.flag=required
0.option.usecaching=false
0.option.url= ldap://<ldap_host:ldap_port>
0.option.useaf=false
0.option.uidprop=sAMAccountName
0.module=com.softwareag.security.sin.is.ldap.lm.LDAPLoginModule
0.option.memberinfoingroups=true
0.option.CreateGroups=true
0.option.prin=cn=<SERVER_USER>,cn=<Common Name>,dc=<Domain Component 1>,
dc=<Domain Component 2>
0.option.grouprootdn=cn=<Common Name>,dc=<Domain Component 1>,dc=<Domain Component 2>
0.option.mattr=member
0.option.ignorePasswordCheck=true
@secure.0.option.cred=<Clear_Text_Password>
Important: Do not change the values of the following properties:
0.flag=required
0.option.usecaching=false
0.option.useaf=false
0.module=com.softwareag.security.sin.is.ldap.lm.LDAPLoginModule
0.option.memberinfoingroups=true
0.option.CreateGroups=true
0.option.ignorePasswordCheck=true
Example:
realm=ADLdapRealm
0.option.userrootdn=cn=Users,dc=DEV,dc=RNDLAB,dc=LOC
0.flag=required
0.option.usecaching=false
0.option.url= ldap://MCKDC.DEV.RNDLAB.LOC:389
0.option.useaf=false
0.option.uidprop=sAMAccountName
0.module=com.softwareag.security.sin.is.ldap.lm.LDAPLoginModule
0.option.memberinfoingroups=true
0.option.CreateGroups=true
0.option.prin=cn=sso_user,cn=Users,dc=DEV,dc=RNDLAB,dc=LOC
0.option.grouprootdn=cn=Builtin,dc=DEV,dc=RNDLAB,dc=LOC
0.option.mattr=member
0.option.ignorePasswordCheck=true
@secure.0.option.cred=DF432
4. Navigate to <Software AG_directory>\profiles\ODE\configuration\, and follow these steps:
a. Open the custom_wrapper.conf file and add the following java system properties:
wrapper.java.additional.7=-Djava.security.krb5.conf=<Absolute_Path_of_krb5.conf_File>
\krb5.conf
wrapper.java.additional.8=-Dsun.security.krb5.debug=true
wrapper.java.additional.9=-Djavax.security.auth.useSubjectCredsOnly=false
b. Save and close the file.
c. Open the jaas.config file and add the Kerberos login module just above the existing OneData login module:
com.sun.security.jgss.krb5.initiate {
com.sun.security.auth.module.Krb5LoginModule required
doNotPrompt=true
principal="HTTP/<SPN with http>"
useKeyTab=true
keyTab="<Absolute_Path_of_Keytab_File>\\<Keytab_Filename>.keytab"
storeKey=true
isInitiator=false
debug=true;
};
com.sun.security.jgss.krb5.accept {
com.sun.security.auth.module.Krb5LoginModule required
doNotPrompt=true
principal="HTTP/<SPN with http>"
useKeyTab=true
keyTab="<Keytab_File_Location>\\<Keytab_Filename>.keytab"
storeKey=true
isInitiator=false
debug=true;
};
Example:
com.sun.security.jgss.krb5.initiate {
com.sun.security.auth.module.Krb5LoginModule required
doNotPrompt=true
principal="HTTP/MCSERVER.DEV.RNDLAB.LOC@DEV.RNDLAB.LOC"
useKeyTab=true
keyTab="C:\\Home\\keytabfile3.keytab"
storeKey=true
isInitiator=false
debug=true;
};
com.sun.security.jgss.krb5.accept {
com.sun.security.auth.module.Krb5LoginModule required
doNotPrompt=true
principal="HTTP/MCSERVER.DEV.RNDLAB.LOC@DEV.RNDLAB.LOC"
useKeyTab=true
keyTab="C:\\Home\\keytabfile3.keytab"
storeKey=true
isInitiator=false
debug=true;
};
d. Save and close the file.
5. Navigate to <Software AG_directory>\profiles\ODE\workspace\webapps\onedata\WEB-INF.
6. Open web.xml, and follow these steps:
a. Add the following servlet mapping:
<servlet>
<servlet-name>KerberosSSORedirector</servlet-name>
<servlet-class>com.datafoundations.onedata.security.auth.sso.kerberos.KerberosSSORedirector
</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>KerberosSSORedirector</servlet-name>
<url-pattern>/KerberosSSORedirector</url-pattern>
</servlet-mapping>
b. Search for the tag <security-constraint> and comment it out as follows:
<!- <security-constraint> ---contents--- </security-constraint> -->
c. Add the following security constraint in web.xml to enable Simple and Protected GSSAPI Negotiation Mechanism (SPNEGO) authentication:
Tip: The name of the OneData user (in <role-name><OneData_User_Group></role-name>) should be the same as the Active Directory user group used.
<security-constraint>
<web-resource-collection>
<web-resource-name>All JSP Files</web-resource-name>
<url-pattern>/KerberosSessionGenerator.jsp</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name><OneData_User_Group></role-name>
</auth-constraint>
<web-resource-collection>
<web-resource-name>restricted methods</web-resource-name>
<url-pattern>/*</url-pattern>
<http-method>DELETE</http-method>
<http-method>PUT</http-method>
<http-method>HEAD</http-method>
<http-method>OPTIONS</http-method>
<http-method>TRACE</http-method>
</web-resource-collection>
</security-constraint>
<login-config>
<auth-method>SPNEGO</auth-method>
</login-config>
<security-role>
<role-name><OneData_User_Group></role-name>
</security-role>
7. Navigate to <Software AG_directory>\profiles\ODE\bin\webapps\onedata\config and follow these steps:
a. Open the onedata.properties file.
b. Set the value of the property onedata.kerberos.sso.enabled to true.
c. Set the value of the property onedata.sso.enabled to false.
d. Save and close file.
8. Set up the OneData URL to one of these formats:
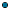 http://<Host_Name>:<port>/onedata/
http://<Host_Name>:<port>/onedata/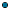 http://<Host_Name>:<port>/onedata/Home.jsp
http://<Host_Name>:<port>/onedata/Home.jsp9. To verify if the SSO configuration is successful, access the OneData URL using any preferred web browser.
Note: Ensure that you complete the web browser configuration before verifying the SSO configuration.
You should be able to view the OneData user interface.
10. If verification of the SSO configuration is not successful, perform these checks:
a. Verify that all the required SSO configurations are done correctly.
b. Check the <Software AG_directory>\profiles\ODE\logs\wrapper.log file for the following HTTP header error:
INFO: Error parsing HTTP request header
INFO | jvm 1 | <timestamp> | Note: further occurrences of HTTP header parsing
errors will be logged at DEBUG level.
c. If the HTTP error appears in the wrapper.log, open <Software AG_directory>\profiles\ODE\configuration\com.softwareag.platform.config.propsloader\com.softwareag.catalina.connector.http.pid-<HTTP-port>.properties and increase the parameter maxHttpHeaderSize value as suitable.
Tip: The default HTTP header size is 8. Double this value to 16 or more depending on your requirement.