How Integration Server Uses a Keystore and Truststore
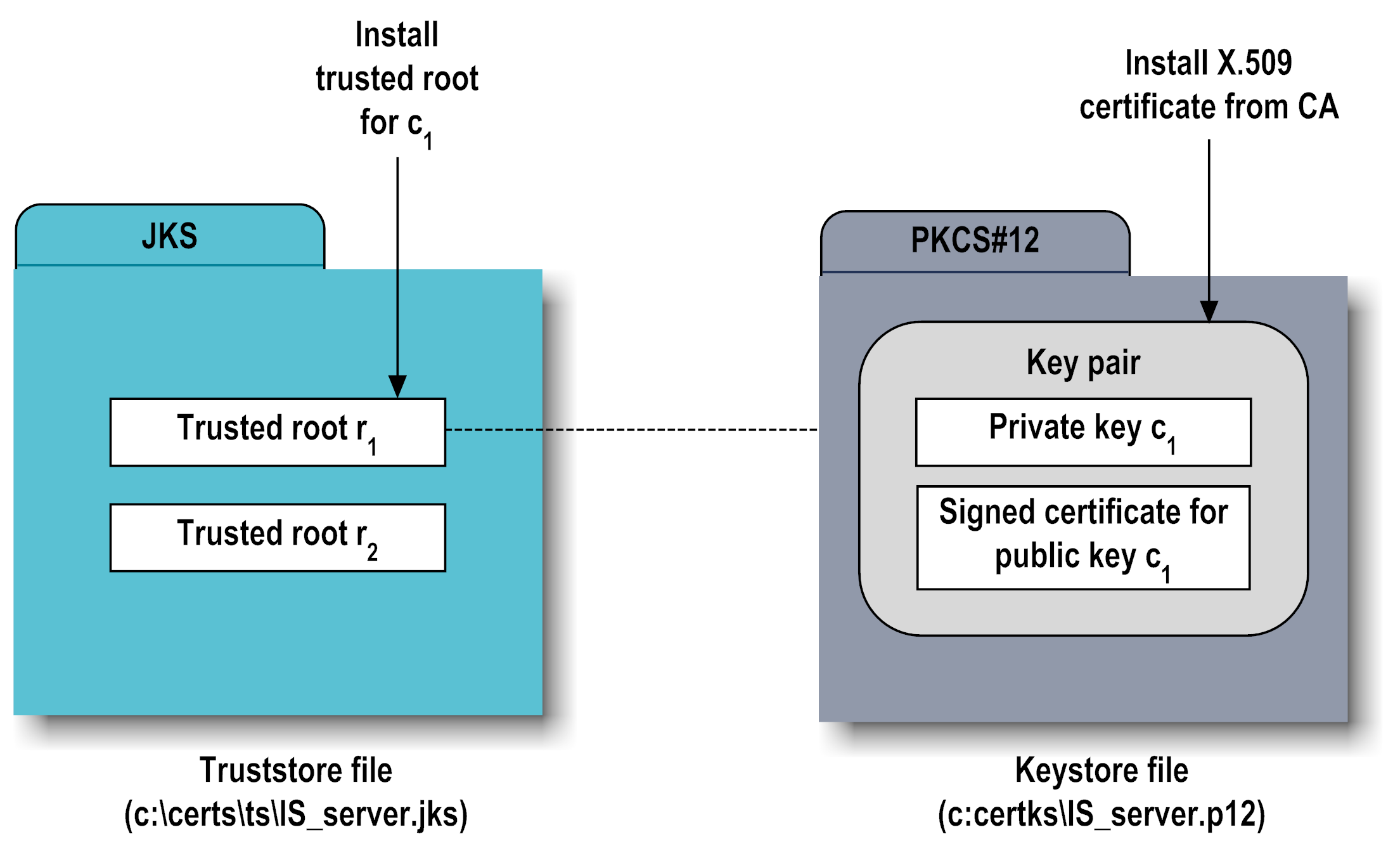
For an Integration Server component to be SSL authenticated, it must have a valid, authorized X.509 certificate installed in a keystore file and the private key and signing certificate for the certificate issuer (CA) installed in a truststore file. The following figure illustrates these requirements and the relationship between the two files.
Example Truststore File and Keystore File Showing Relationship
As shown in the above figure, the same truststore file can contain multiple trusted root certificates (public keys for the signing CAs). These trusted roots might be associated with numerous keystore files. A keystore file can contain the key pairs for multiple Integration Server components, and the entire certificate chain required for a component's authentication.
With a certificate chain, it is necessary to validate each subsequent signature in the list until a trusted CA certificate is reached. For Integration Server, you must include the entire chain of certificates in a keystore and truststore. Also, any root CA certificates in use by clients must be in an Integration Server truststore.