Asymmetric Binding Configuration
WS-SecurityPolicy specification deals with three types of Security Bindings. A security binding determines how the message transfer is to be done between the recipient and the initiator.
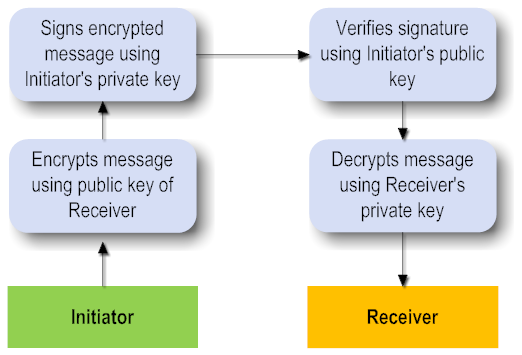
Asymmetric Binding is used when both the Initiator and the Recipient possess public and private keys. The message transfer takes place using Public Key Infrastructure.
An Asymmetric Binding element in the WSDL looks like this:
<sp:AsymmetricBinding
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:InitiatorToken>
</sp:InitiatorToken>
<sp:RecipientToken>
</sp:RecipientToken>
<sp:AlgorithmSuite>
<wsp:Policy>
<sp:TripleDesRsa15/>
</wsp:Policy>
</sp:AlgorithmSuite>
<sp:Layout>
<wsp:Policy>
<sp:Strict/>
</wsp:Policy>
</sp:Layout>
<sp:IncludeTimestamp/>
<sp:OnlySignEntireHeadersAndBody/>
</wsp:Policy>
</sp:AsymmetricBinding>
The following run-time actions that support WS-Security policies use a common Asymmetric Binding element:

The Require Encryption action.

The Require Signing action.

The Require WSS SAML Token action.

The Require WSS X.509 Token action.
The Asymmetric Binding Components
The components of a security binding are:
Recipient Token Inclusion
The value of Recipient Token Inclusion specifies how to include the Recipient token during message exchange from Initiator to Recipient or Recipient to Initiator. It takes the same values as Initiator Token Inclusion above.
Algorithm Suite
The value of Algorithm Suite specifies the algorithm suite to be used for this asymmetric binding. The possible algorithms supported are:

Basic 256

Basic192

Basic128

TripleDes

Basic256Rsa15

Basic192Rsa15

Basic128Rsa15

TripleDesRsa15

Basic256Sha256

Basic192Sha256

Basic128Sha256

TripleDesSha256

Basic256Sha256Rsa15

Basic192Sha256Rsa15

Basic128Sha256Rsa15
Layout
Layout describes the way information is added to the message header. The possible values are:
Value | Description |
Strict | Items are added to the security header in a principle of declare before use. |
Lax | Items are added to the security header in any order that conforms to WSS: SOAP Message Security. |
LaxTsFirst | Same as Lax except that the first item in the security header must be a wsse:Timestamp. The wsse:Timestamp property must also be set to true in this case. |
LaxTsLast | Same as Lax except that the last item in the security header must be a wsse:Timestamp. The wsse:Timestamp property must also be set to true in this case. |
