Authorization Workflows
The flow of authorization requests and responses between the end user, client application, authorization server, and resource server depends on the grant type defined by the OAuth framework.
API Gateway supports the following authorization flows for OAuth 2.0 authentication:

Authorization code grant

Implicit grant

Client credentials
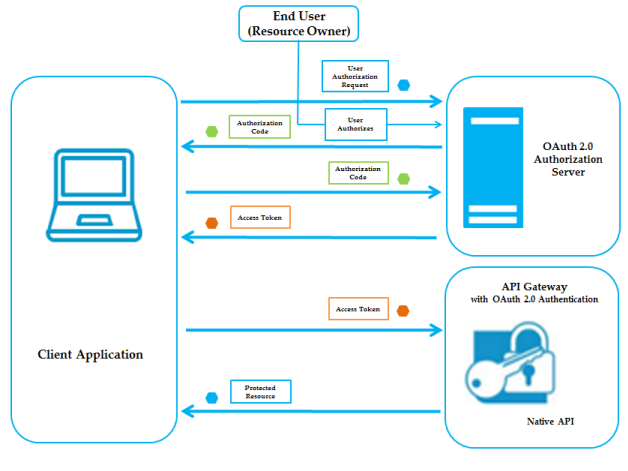
Authorization Code Grant Flow
The authorization code grant type is used to authenticate and provide access to clients that have credentials on the authorization server. This grant type requires the client to authenticate to the authorization server before obtaining an access token.
You use this type of grant to authenticate and provide access to confidential clients.
When using the authorization code grant type, the authorization server can optionally issue a refresh token to the client application along with the access token. A refresh token enables clients to get a new access token without requesting additional approval from the resource owner. When the access token expires, the client application can pass the refresh token to the authorization server to request a new access token.
Authorization Code Grant Flow
The Authorization Code Grant OAuth flow has the following steps:
1. Client application initiates the flow to authorize endpoint to request access to end user's data.
2. Authorization server validates the request and informs the user that the client is requesting access within a specified scope. The user then approves or denies the request.
3. When the user approves the request, authorization server generates an authorization code for the client. Authorization server transmits this authorization code through the redirection URI provided by client.
If the user denies the request, authorization server returns an error response.
4. The client's redirection URI passes the authorization code to the token endpoint to exchange the authorization code for an access token.
When making the request, the client authenticates with authorization server. The client includes the redirection URI that was used to obtain the authorization code for verification.
5. Authorization server authenticates the client, validates the authorization code, and ensures that the redirection URI received matches the URI used to redirect the client.
If the access token request is valid and authorized, authorization server responds with an access token and, optionally, a refresh token.
If the request is invalid, authorization server returns an error response.
6. Client uses this access token to send HTTP requests to API Gateway. The access token is validated by authorization server.
7. API Gateway checks with authorization server to make sure the requested API is within the scope for which the access token was issued, and whether the client is authorized to access the resources in the scope.
8. If the access token is expired, authorization server returns a specific error response.
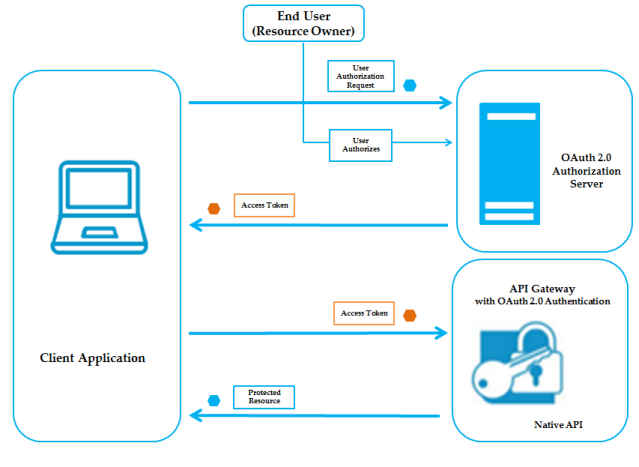
Implicit Grant Flow
The implicit grant type is used to authenticate browser-based applications and mobile applications. This grant type is less secure than the authorization code grant because it does not require the client to authenticate with the authorization server. The authorization server grants any client with a valid client ID an access token. In addition, the implicit grant type passes the access token through the resource owner's browser, exposing it to theft by malicious applications on the resource owner's device.
You use this type of grant to authenticate and provide access to public clients.
Note: The implicit grant type does not support refresh tokens.
Implicit Grant Flow
The Implicit Grant OAuth flow has the following steps:
1. Client application initiates the flow to authorize endpoint to request access end user's data.
2. Authorization server validates the request and informs the user that the client is requesting access within a specified scope. The user then approves or denies the request.
3. When the user approves the request, authorization server generates an access token for the client. Authorization server transmits the access token through the redirection URI provided by client.
If the user denies the request, authorization server returns an error response.
4. Client uses this access token to send HTTP requests to API Gateway. The access token is validated by authorization server.
5. API Gateway checks with authorization server to make sure the requested API is within the scope for which the access token was issued, and whether the client is authorized to access the resources in the scope.
6. If the access token is expired, authorization server returns a specific error response.
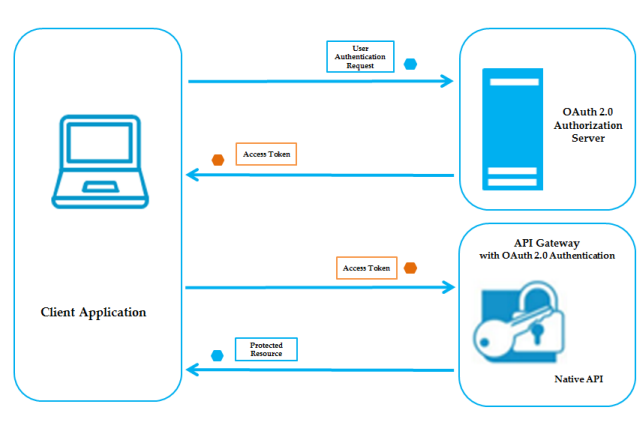
Client Credentials Flow
The client credentials grant type is used to authenticate and provide access to clients using their own credentials.
You use this type of grant for fully trusted clients since it allows them to authenticate and get access token for any user. You can use the client credentials grant for confidential clients only.
Client Credentials Grant Flow
The Client Credentials Grant OAuth flow has the following steps:
1. The client application initiates the flow to token endpoint to request access to end user's data.
2. Authorization server validates the request and generates an access token for the client.
3. Client uses this access token to send HTTP requests to API Gateway. The access token is validated by authorization server.
4. API Gateway checks with authorization server to make sure the requested API is within the scope for which the access token was issued and whether the client is authorized to access the resources in the scope.
5. If the access token is expired, authorization server returns a specific error response.