This document introduces EntireX Security under z/VSE through overviews of the functionality and components of EntireX Security. The location where Broker Kernel is installed determines the functionality made available for EntireX Security. This document covers the following topics:
Note:
Installation of the security software is described under Installing EntireX Security under z/VSE.
This table lists the security functionality available with EntireX Security running Broker Kernel under the respective operating system. See also Configuration Options for Broker.
| Security Functionality | z/OS | UNIX | Windows | BS2000 | z/VSE | Comment |
|---|---|---|---|---|---|---|
| Authentication of user | Yes | Yes | Yes | Yes | Yes | Verify User ID password. |
| User password change | Yes | No | No | No | No | |
| LDAP authentication | No | Yes | Yes | No | No | Authenticate using LDAP repository. |
| Trusted user ID | Yes | No | No | No | No | Trusted computer base, avoiding plain text password. |
| Verified client user ID | Yes | No | No | Yes | Yes | Provide verified identity of client to server. |
| Authorization of client request | Yes | No | No | No | No | |
| Authorization of server register | Yes | No | No | No | No | |
| Authorize IP connection | Yes | No | No | No | No | |
| Authorization rules | No | Yes | Yes | No | No | An authorization rule is used to perform access checks for authenticated user IDs against lists of services defined within the rule. This feature is available on UNIX and Windows using EntireX Security on these platforms. Authorization rules can be stored in the Broker attribute file or in an LDAP repository. See Authorization Rules. |
| SSL/TLS | (1) | Yes | Yes | No | (2) | Industry standard encryption mechanism. See SSL/TLS and Certificates with EntireX. |
Notes:
This diagram depicts the location where the Broker kernel must be installed and where the Broker stubs can be installed. It also depicts the location of the security components of the kernel and stubs of Broker.
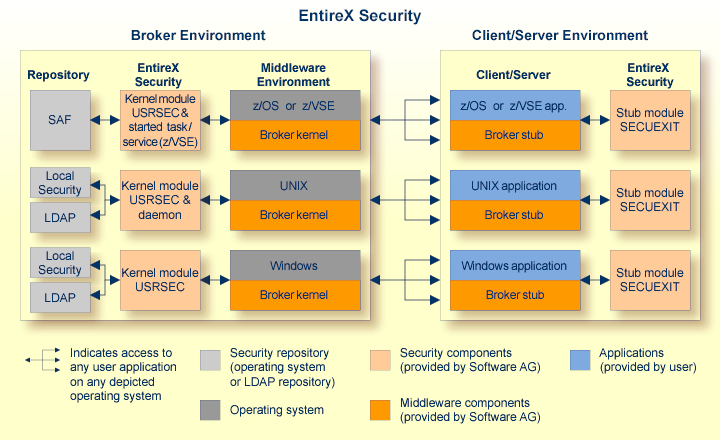
EntireX Broker acts as an agent to make the creation and operation of client/server applications simpler and more effective. Any number of server applications can be built for use by any number of clients. EntireX Security allows you to protect your server applications and clients independently.
Clients and servers are authenticated by user ID and password on their first contact with the system.
This section describes the parameters for configuring EntireX Security
under z/VSE. You may either accept or modify the default settings which are
specified in the Broker attribute file DEFAULTS=SECURITY.
See also Security-specific Attributes and
Operator Commands.
This section covers the following topics:
Authentication is mandatory and performed for both client and server applications based on user ID and password. First contact with the Broker results in the host security system being referenced. If authentication fails, access is denied and the application is informed with a suitable error message.
It is the responsibility of both client and server applications to supply a valid user ID and password when calling the Broker. The user ID must be supplied with all commands. The password is required only for the first command and should not be supplied subsequently, except when executing multiple instances of the same application.
Authentication expires after a period of non-activity after which it
must be repeated. User ID and password must be resupplied before further
access is possible. The time limits CLIENT-NONACT
and SERVER-NONACT
determine these timeout periods and are defined in the Broker attribute file.
To cater for situations where a site is in transition from uppercase to mixed case passwords setting this parameter can convert all passwords to uppercase. It is not recommended you use this option by default.
PASSWORD-TO-UPPER-CASE={NO,YES} |
Convert password to uppercase. |
The following parameter can be used to modify the functionality of EntireX Security:
SECURITY-LEVEL=AUTHENTICATION |
User authentication is performed but without any resource authorization (the normal default operation). |