Server Authorization
After a user request has been authenticated by the server, it is usually necessary to do some authorization checks to make sure that the user making the request has the necessary privilege to act on that resource. In My webMethods Server, the most common way to do authorization checks is by evaluating Access Control Lists (ACLs). ACLs can be associated with every kind of server resource, such as pages, portlets, and so forth.
More advanced concepts like verbs and mechanics (groupings of business logic) are server resources as well, and therefore also participate in the ACL evaluation model. This feature allows developers to programmatically lock down capabilities of the server.
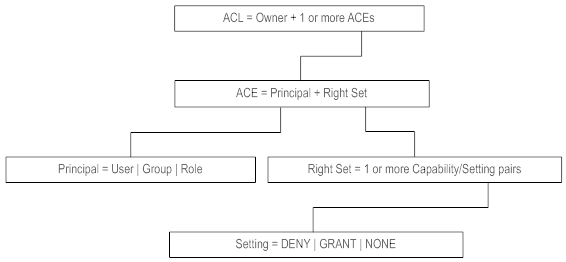
To understand the authorization engine in My webMethods Server, look at the composition of an ACL. An ACL is a list of Access Control Entries (ACEs). An ACE is a simple structure containing an element called a Principal and an element called a Right Set.
A Principal is a user, group or role. Some examples of Principals are:
Principal | Example of a Principal |
User | Myles Perkins |
Group | Members of the Perkins family |
Role | A role definition that resolves to Myles, such as, “Users who have the ‘Job Title attribute value set to ‘Product Manager.’ |
Right Sets are groupings of actions that can be performed on a server resource. An example of a Right Set is “Grant the ability to read. Right Sets themselves are broken down into two distinct parts, Capabilities and Settings. Different types of server resources have different Capabilities associated with them. For example, pages have Capabilities that include “Add Portlet To Page” while folders have Capabilities that include “Create Sub Folder” and “Can Read Items in this Folder.”
The other part of a Right Set, the Setting, can have four possible values: DELEGATE, DENY, GRANT or NONE. Each Capability that makes up a Right Set has a Setting value. Right Sets are made up of many Capability-Setting pairings. Here is an example of a Right Set:
DENY + create sub folder
GRANT + read
This particular Right Set is made up of two Capability-Setting pairings. If associated with a folder resource, this Right Set is resolved to deny a Principal the ability to create sub folders but grant the ability to actually read the folder.
The values for Settings have the following meanings:
This Setting value... | Has this effect for the Principal... |
DENY | Denies the access to perform the capability. |
GRANT | Explicitly grants access to perform the capability. |
DELEGATE | Explicitly grants access and gives the right to assign the capability to another Principal. |
NONE | Provides no explicit Setting. Authorization for this server resource will be determined from another source. |
The following figure shows the relationships described in this section.
Anatomy of an ACL
As an example, to deny read access to Brian and the Marketing Group from the Engineering page, we would have the following setup:
The server resource is the Engineering page.
The Engineering page has an ACL associated with it that contains two ACEs:
Principal | Right Set |
Brian | DENY read |
Marketing Group | DENY read |