Protect RTBS webservice access
You can use your own keystore and truststore to protect RTBS webservice of unauthorized access.
After the installation, MashZone NextGen uses a default keystore and truststore. For security reason we recommend to change that configuration for production environments. Please make sure that the truststore, referenced by RTBS, contains the appropriate certificate for the key, referenced by MashZone NextGen. RTBS is only available, with a valid configuration.
If multiple MashZone NextGen nodes are used in a clustered scenario, it is recommended to use the same key for all MashZone NextGen instances.
The default keystore and truststore are located in the common and conf folders of the MashZone NextGen installation.
For authentication MashZone NextGen webapp sends an HTTP header "Authorization" with "Bearer [JWT]" as value.
Procedure
1. Edit the following parameters, used by MashZone NextGen, to use your own keystore file to generate the JWT required for authentication.
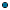
jwt.keystore.file
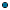
jwt.keystore.passwd
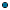
jwt.keystore.alias
The parameters are contained in the presto.config file in the following directory.
<MashzoneNG_install>\apache-tomcat\webapps\mashzone\WEB-INF\classes\
2. Edit the following parameters, used by RTBS, to use your own truststore file to verify the JWT.
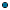
truststore.file
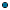
truststore.passwd
The parameters are contained in the rtbs.config file in the following directory.
<MashzoneNG_install>\apache-tomcat\webapps\rtbs\WEB-INF\classes\