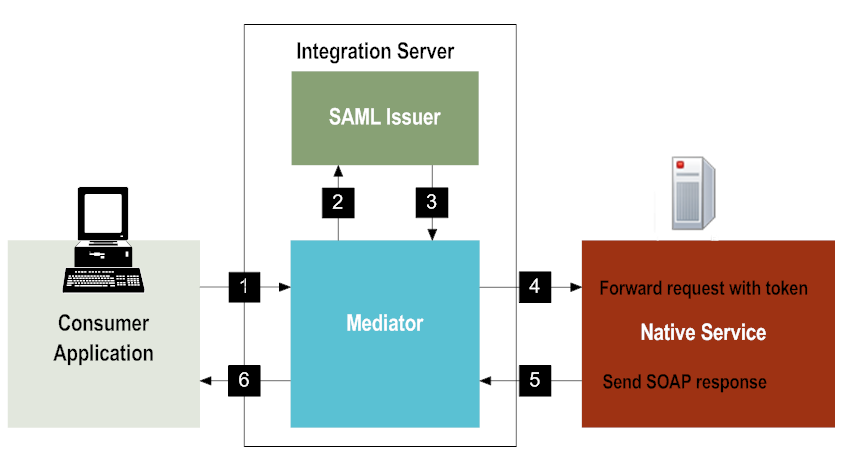
Step | Description |
1 | The user's client sends a SOAP request with SAML authentication information to Mediator. Integration Server authenticates the incoming request. |
2 | |
3 | The SAML Issuer sends the SAML v1.0 or v2.0 assertion to Mediator. |
4 | Mediator forwards the SOAP request along with the SAML assertion to the native service. Mediator also uses the Integration Server keystore and signing alias you specified to sign the SAML token and the request body before sending the request to the native service. Also, if you have configured the predefined Java service pub.mediator.security.ws.AddSamlSenderVouchesToken to add a timestamp in the outbound request, Mediator signs the timestamp. |
5 | The native service sends a SOAP response to Mediator. |
6 | Mediator sends the response to the user's client. |