Central Configurator Security Implementation
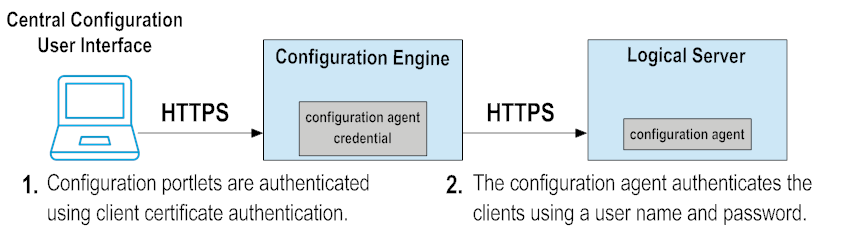
To encrypt communications between each configuration agent on each BAM logical server and the configuration engine, the certificates installed during SSL configuration are used to negotiate the SSL handshake. In addition, the certificates are used between the Central Configurator UI components and the Central Configurator Web application to provide client certificate authentication. All other authentication between Central Configurator and the BAM logical servers' configuration agents is done through simple user name and password authentication.
Figure 15. Central Configurator and SSL implementation
For instructions about installing certificates for SSL, see
Installing Certificates.