Resource Owner Password Credentials Grant
The resource owner password credentials (ROPC) grant allows resource owners to provide trusted clients with their credentials which the clients can then use to obtain an access token. Clients can use the access token to access resources on the resource server. The intent of the ROPC grant is to provide access to resources in situations where there is an existing trust relationship between the resource owner and the client or when it is not possible to use other authorization grant types.
With the ROPC grant type, the client does not need resource owner approval nor does the client need a redirection endpoint. Instead the client calls the token endpoint on the authorization server directly, presenting the resource owner’s credentials for authentication. The token endpoint authenticates the credentials and issues an access token.
When using the ROPC grant type, the authorization server can issue a refresh token to the client application along with the access token. A refresh token enables clients to get a new access token without requesting additional approval from the resource owner. When the access token expires, the client application can use the pub.oauth:getToken service to pass the refresh token to the authorization server to request a new access token.
You use the ROPC grant type to authenticate and provide access to confidential clients and public clients.
The ROPC grant type is the least secure of all the grant type supported by Integration Server.
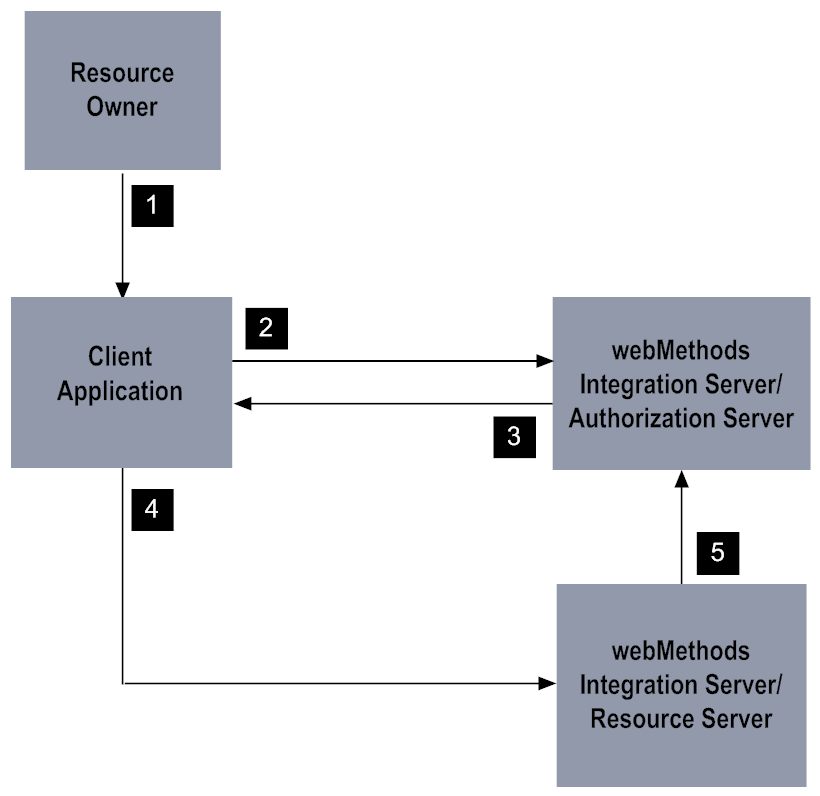
Resource Owner Password Credentials Grant Flow
The following table describes each steep in the ROPC grant flow.
Stage | Description |
1 | The resource owner provides their credentials to the client application |
2 | The client application presents the resource owner’s credentials to the token endpoint, the pub.oauth:getToken service, on the authorization server. |
3 | On the authorization server, the pub.oauth:getToken service authenticates the provided credentials and verifies that the credentials belong to a confidential client allowed to use the resource owner password credentials (ROPC) grant. The service also checks that the scopes specified with the client request are allowed for the client. The authorization sever returns an access token to the client. If set to do so, the authorization server also returns a refresh token to the client. |
4 | The client application uses the access token to request a resource on the resource server. |
5 | The resource server checks with authorization server to make sure the access token is valid. If it is, the resource server makes sure that the requested service is within the scope for which the access token was issued. It also checks that the resource owner is authorized to access the requested resource. |