Restricting the Services or Web Service Descriptors Available from a Port
You can limit the services or provider web service descriptors that clients can invoke through a port by setting the access mode for the port. Integration Server provides two types of port access:
 Deny By Default.
Deny By Default. This is the default type for newly created ports. Use this type to deny access to all services and provider web service descriptors except those you specify in a list that is associated with the port.
You might use a Deny By Default port to restrict access so only the set of services that a single application uses are accessible through the port. Set the port to Deny By Default and specify the services for the application in the list associated with the port. Then, clients using the application can only access the specific services for the application. All ports, except 5555, are initially set to Deny By Default with a limited list of services available.
Note:
You can determine whether Integration Server adds the predefined list of internal and built-in services to the allow list of a port configured to deny access by setting the watt.server.security.createDefaultServicesOnPorts server configuration parameter. Some of the internal services have an Execute ACL set to anonymous which may be a security vulnerability in some environments.
 Allow By Default.
Allow By Default. Select this type if you intend to allow access to all services and provider web service descriptors except those you explicitly deny in a list that is associated with the port.
When Integration Server receives a service request through a port, Integration Server verifies that the service request is allowed through that port. If the service or web service descriptor can be invoked through the port, Integration Server continues with service or web service descriptor execution. If access is denied, Integration Server returns an access denied message or status to the client.
Integration Server verifies port access for the top-level service only. Integration Server does not verify port access for any child service invoked by the top-level service. For example, suppose that serviceA invokes serviceB. Additionally, suppose that port 5678 is configured to deny by default. serviceA is on the allow list for the port, but serviceB is not. When Integration Server receives a request for serviceA on port 5678, Integration Server verifies that serviceA can be invoked through the port. Integration Server does not verify that serviceB can be invoked through the port.
Similarly, Integration Server verifies port access for the provider web service descriptor only. Integration Server does not verify port access for any operations or handler services in the web service descriptor.
Any service URI can be included in port access control, including service URIs that are not part of the Integration Server namespace. As a result, web services that are defined on Web Services Stack can be added to the port access control lists. However, Integration Server validates and enforces web service URIs only.
Note:
By default, Integration Server performs an access check on all web services that were deployed directly into Axis2. This might be unwanted behavior. To disable the access check, set watt.server.portAccess.axis2 to false.
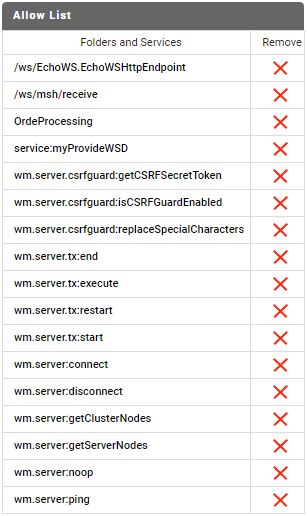
The following allow list for a port that is configured to deny by default includes two web services that are not part of the Integration Server namespace, a folder (OrderProcessing), a provider web service descriptor, and some internal services.
Allow List for a Port Configured to Deny by Default
Note:
By default, the Integration Server provides an HTTP port at 5555 that allows all service requests that come in on that port access (unless prohibited by an ACL). Although this port is ideal for initial Integration Server installation and configuration, as well as many development environments, for deployment, you should replace this port with ports that limit access to services you intend to make available to your partners and users.
Note:
Another way to control access to services through a port is to restrict access to clients that present particular client certificates. See
Customizing Authentication Using JAAS for more information.
Note:
In Software AG Command Central, the access mode functionality in which you restrict the services and web service descriptors accessible through port is referred to as URL Access.