User Identification to Support Identity and Access Management Policy
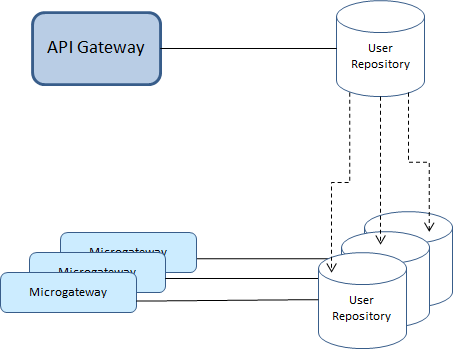
Microgateway supports authentication against users who are defined through API Gateway. The authentication is performed against a read-only user repository. This ensures that users can be authenticated even if Microgateway is not connected to any running API Gateway instance. The Microgateway user repository is populated by copying the API Gateway user repository (users.cnf) when provisioning a Microgateway.
The figure illustrates the Microgateway user repository being populated by copying the API Gateway user repository.
When you provision a Microgateway or start a Microgateway the users.cnf and related configurations are picked up from the location IntegrationServer\instances\default\config\users.cnf in the API Gateway installation directory.
The API Gateway installation directory can be specified using the Microgateway configuration parameter apigw_dir
The parameter can be specified either as a command line option or through the Microgateway configuration file.
The configuration parameter applies to the following Microgateway commands:

createInstance

createDockerFile
These commands create a copy of the users.cnf. The apigw_dir also affects the users.cnf lookup that happens during Microgateway start. The lookup procedure checks for local users.cnf (config/users.cnf). If there is no local users.cnf, then lookup users.cnf using apigw_dir. If apigw_dir or users.cnf is not found, then the startup fails.
Microgateway does not support user authentication by default. To activate user authentication you have to specify the parameter user_auth = internal when provisioning or starting a Microgateway.
If the user authentication is not activated, APIs with authentication policies are rejected. The users.cnf lookup is only performed when user authentication is activated.
Delegated authentication using API Gateway
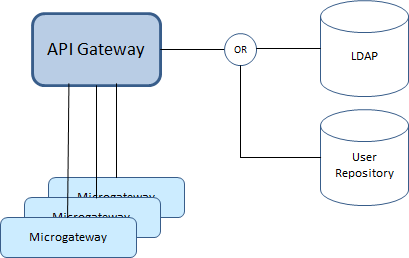
Microgateway supports the delegated authentication to API Gateway. API Gateway performs the authentication against the configured LDAP or the user repository.
The delegated authentication is activated by setting the parameter user_auth = delegated . When the delegated authentication is activated, Microgateway talks to the API Gateway authentication API.
The authentication API exposes the resource: /rest/apigateway/authenticate
The resource exposes a POST method. The a user authentication is triggered through the request:
POST /rest/apigateway/authenticate
{
"user-id":"",
"password:"",
"domain":""
"includeGroups":true
}
includeGroups is set to true only when Authorize User policy is configured. Based on the value, the groups details of the user are sent in response from API Gateway to Microgateway.
The password and user credentials are transferred in an unencrypted way. Therefore, the delegated authentication must happen through HTTPS.
On successful authentication the API returns a HTTP 200 response with user information and expiry information as follows:
HTTP 200 OK
{
"status": "Authenticated",
"accessProfiles": [
"Administrators",
"Tyche"
],
"groups": [
"Administrators",
"Tyche"
],
"user": "user1",
"expires":"60"
}
The response provides information about the user, accessProfiles, groups, and the expiry interval. This tells the Microgateway for how long the delegated authentication result can be cached.
If the authentication fails the API returns a HTTP 401 response.