Single Sign-On
Note:
This page is not applicable if you have created your account using the Software AG Cloud sign-up page.
Single sign-on is a process that allows users to access all authorized network resources without having to log in separately to each resource.
Security Assertion Markup Language 2.0 (SAML 2.0) is a standard for exchanging authentication and authorization data between security domains. SAML 2.0 is an XML-based standard that uses security tokens containing assertions to pass information about a principal (usually an end user), between a SAML authority, that is, an identity provider (IdP), and a SAML consumer, that is, a service provider. Using SAML, a service provider can contact an identity provider to authenticate users who are trying to access secure content.
Note:
Currently, only SAML 2.0 is supported.
Integration Cloud supports single sign-on (SSO) that allows users to authenticate themselves against an Identity Provider (IdP) rather than obtaining and using a separate username and password. Under the SSO setup, Integration Cloud works as a Service Provider through SAML. You can put the IdP you already trust in charge of authentication, while your users can access Integration Cloud without another password to manage.
The following actions take place while logging into Integration Cloud using SAML 2.0:
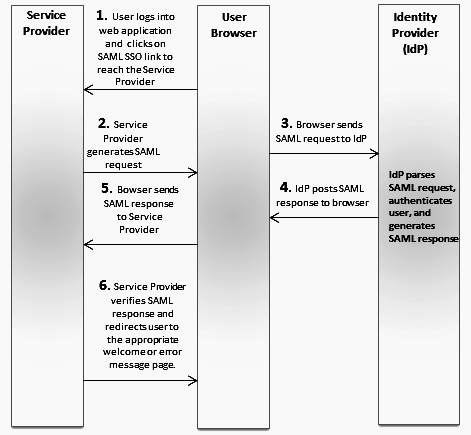
Service Provider: Integration Cloud
Identity Provider (IdP): Microsoft Azure, Okta, Oracle Access Manager
1. User logs into a web application and clicks on the SAML SSO link to access Integration Cloud.
2. Integration Cloud generates a SAML authentication request and posts the request to the user’s browser.
3. The browser sends the SAML request to the Identity Provider for authentication. The SAML request contains user information, Identity Provider URL, and the assertion response URL.
4. The Identity Provider decodes the SAML request, extracts the URL, authenticates the user, generates a SAML response, and posts the SAML response to the browser.
5. The browser sends the SAML response to Integration Cloud.
6. Integration Cloud checks if the Identity Provider authentication was successful, that is, verifies the SAML response, and redirects the user to the appropriate home page or the error message page.
Note:
Integration Cloud SSO capability has been tested to work with Microsoft Azure Active Directory (Azure), Oracle Access Manager (OAM), and Okta as Identity Providers.
You can click Edit to configure SAML 2.0 settings for single sign-on or click Export SAML 2.0 Metadata if you want to export the Integration Cloud SAML metadata.
See
Configuring SAML Settings for Single Sign-On on how to configure SAML settings for single sign-on.
Note:
If you have already configured SAML based single sign-on (SSO), the SSO Login option appears in the login page. If you click the SSO Login option, Integration Cloud redirects you to the Identity Provider (IdP) login page. After you provide the IdP login credentials, you will be logged into Integration Cloud.
Note:
You can access or edit the single sign-on configuration page only if you can edit the
Company Information, that is, have the
Manage Company Capabilities permission under
Settings  > Access Profiles > Administrative Permissions > Account Controls
> Access Profiles > Administrative Permissions > Account Controls.
 > Access Profiles > Administrative Permissions > Account Controls.
> Access Profiles > Administrative Permissions > Account Controls. > Access Profiles > Administrative Permissions > Account Controls.
> Access Profiles > Administrative Permissions > Account Controls.