How Do I Secure API Gateway Server Communication using HTTPS?
Secure API Gateway server, a component in an API Management setup, to enable the other components in the API Management setup to communicate with the API Gateway server over HTTPS. This use case explains how to secure API Gateway server communication using HTTPS protocol by using the existing server and client certificates.
The use case starts when you have an API Gateway instance to be secured using HTTPS and you have the required server and client certificates to secure the communication channel between API Gateway server and other components. It ends when the secure channel is configured for communication between API Gateway server and the other components.
Before you begin
Ensure that you have:
 API Gateway
API Gateway administrator privileges

Required client and server certificates
To configure API Gateway server for secure communication
1. Ensure that the keystore and truststore with the required certificates are located at Installation_Dir\common\conf.
2. Configure keystore and truststore in the API Gateway UI.
This is required to set up a secure outbound communication from the API Gateway server to the client.
a. Log on to API Gateway user interface.
b. Navigate to Administration > Security > Keystore/Truststore.
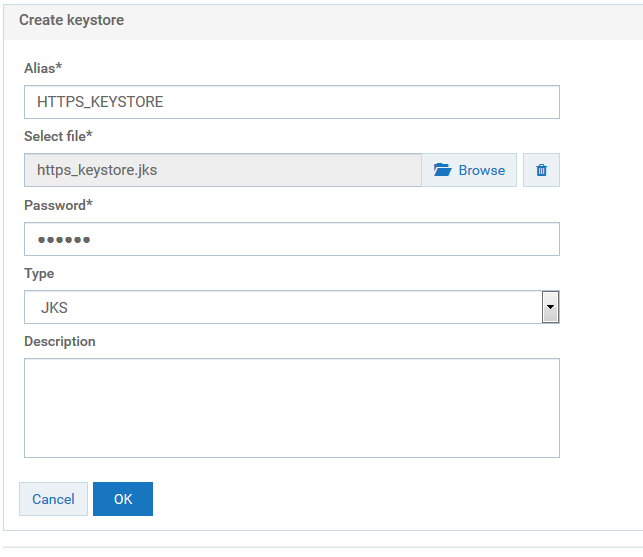
c. Click Add keystore.
d. Provide the following details:
 Alias
Alias. A text identifier for the keystore file. The alias name can contain only alphabets, numbers and underscores. It can not include a space, hyphen, and special characters.
 Select file
Select file. Browse and select the file https_keystore.jks file located at
Installation_Dir\common\conf.
 Password
Password. Specify the password for the saved keystore file associated with this alias.
 Type
Type. Specify the certificate file format of the keystore file, which, by default, is JKS for keystores.
e. Click OK.
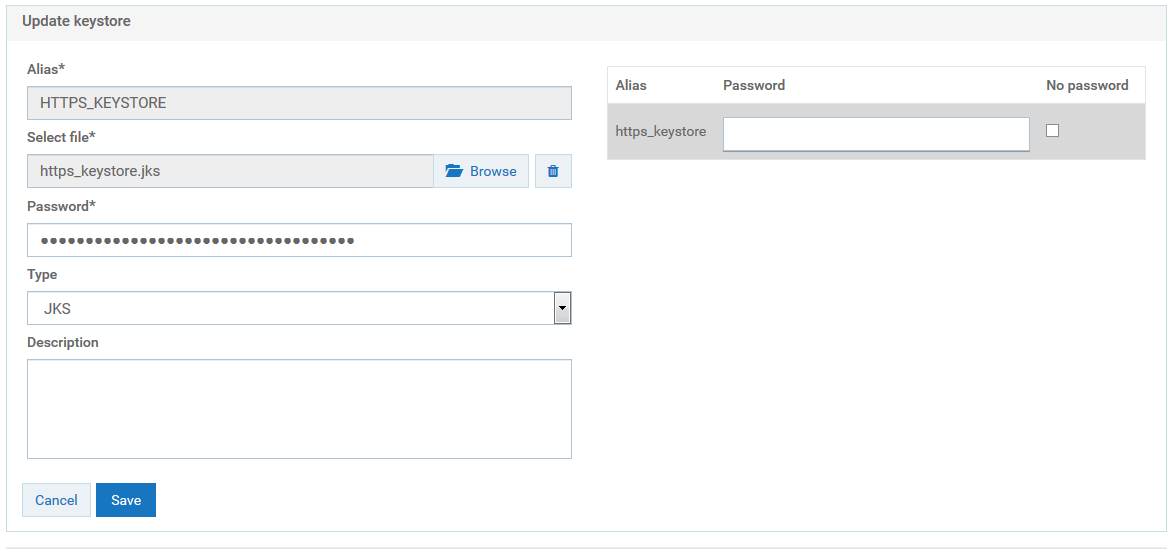
A warning appears, prompting you to create a password for the key alias.
f. Close the warning dialog box.
The Update keystore dialog box appears.
g. Provide the password for the https_keystore file, for example, manage.
h. Click Save.
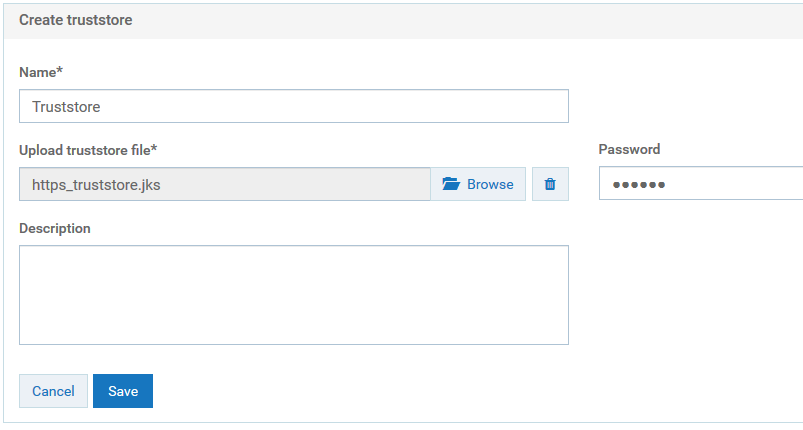
i. Click Add truststore.
j. Provide the following details.
 Name
Name. A name for the truststore file.
 Upload truststore file
Upload truststore file. Browse and select the https_truststore.jks file located at
Installation_Dir\common\conf.
 Password
Password. Specify the password that is used to protect the contents of the truststore.
k. Click Save.
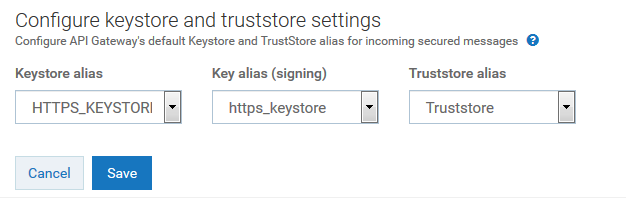
l. In the Configure keystore and truststore settings section, provide the details of keystore and truststore configured.
m. Click Save.
API Gateway, by default, uses the configured keystore and truststore files for keys and certificates for any in and out HTTPS communication.
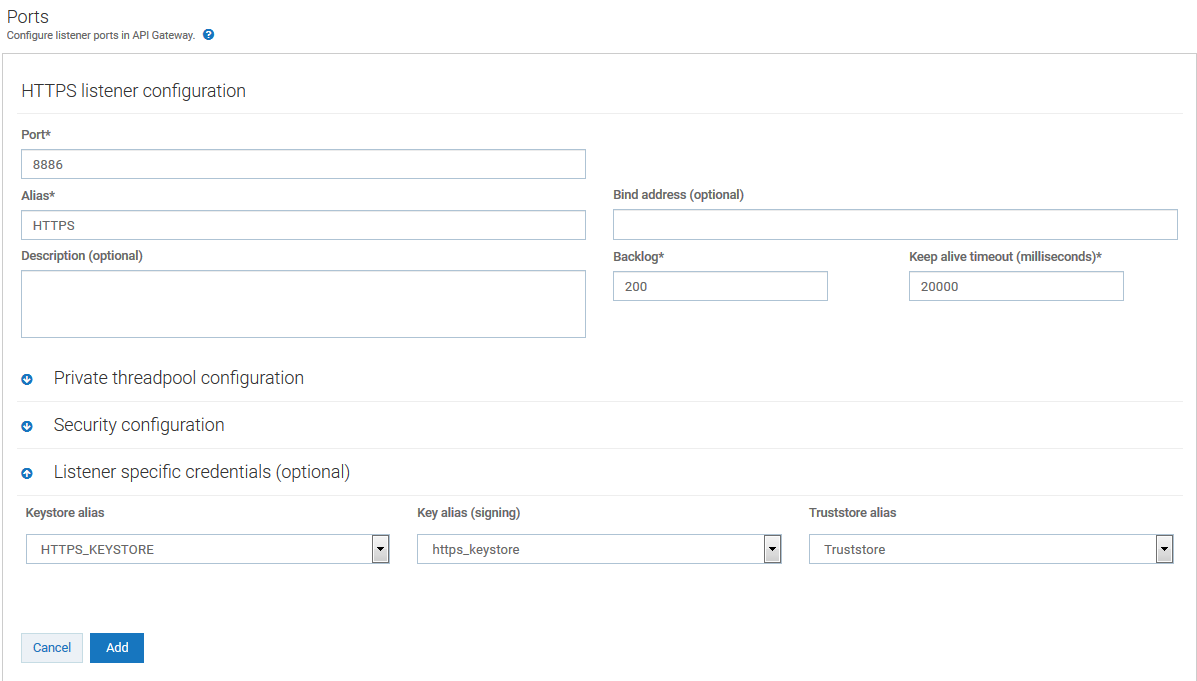
3. Create an HTTPS port in API Gateway and associate the keystore and truststore aliases.
This is required to set up the inbound communication.
a. Navigate to Administration > Security > Port.
b. Click Add ports, and select HTTPS as the port type.
c. Click Add.
d. Provide the following details
 Port
Port. Specify the port number you want to use for the HTTPS communication.
 Alias
Alias. Specify an alias for the port that is unique for this API Gateway instance. The alias must be between 1 and 255 characters in length and include one or more of the following: alphabets (a -z, A-Z), numbers (0-9), underscore (_), period (.), and hyphen (-).
 Backlog
Backlog. Specify the number of requests that can remain in the queue for an enabled port before API Gateway begins rejecting requests. The default is 200. The maximum value is 65535.
 Keep alive timeout
Keep alive timeout. Specify when to close the connection if the server has not received a request from the client within this timeout value (in milliseconds) or when to close the connection if the client has explicitly placed a close request with the server.
e. In the Listener-specific credentials section provide the following information:
 Keystore alias
Keystore alias. Select HTTPS_KEYSTORE.
 Key alias(signing)
Key alias(signing). Select https_keystore.
 Truststore alias
Truststore alias. Select Truststore.
f. Click Add.
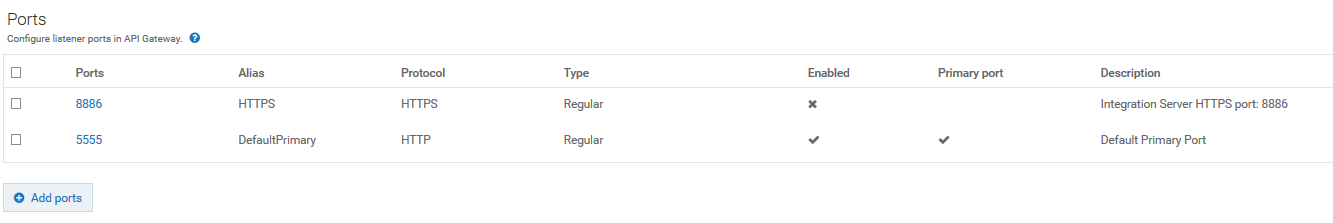
The HTTPS port 8886 is added and displayed in the list of ports.
g. Enable the new port 8886 by clicking the X mark in the port's Enabled column.
The port 8886 is now enabled and API Gateway server is now ready to accept requests over HTTPS port 8886.
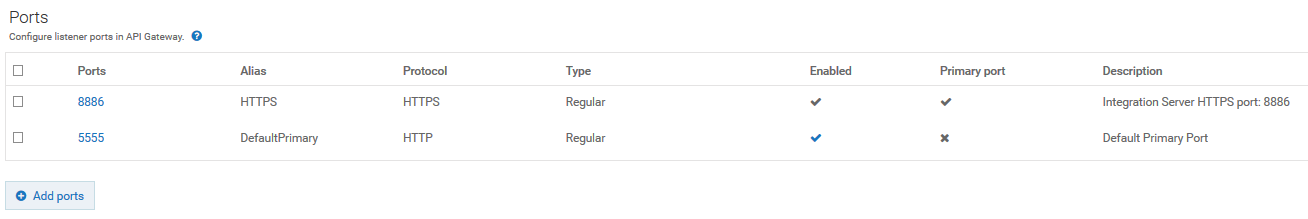
h. Set the port 8886 as primary port by clicking in the port's Primary port column.
The port 8886 is now set as the primary port and the port 5555 is no more the primary port.
i. Disable the port 5555 by clicking the tick mark in the port's Enabled column.
The default primary port 5555 that accepts requests on HTTP is now disabled.
4. Configure the API Gateway UI to access the API Gateway server securely.
a. Open the file uiconfiguration.properties located in the folder Installation_Dir\profiles\IS_default\apigateway\config\.
b. Modify the following properties:
#IS properties
apigw.is.base.url = https://localhost:8886
apigw.is.rest.directive = /rest
apigw.user.lang.default = en
Here we configure the HTTPS port 8886 in the base URL property to point the API Gateway to communicate to the server URL.
You now have a secure communication channel established between the API Gateway server and the client.