API Gateway Deployment Scenarios
API Gateway enforces threat protection, policies and routing capabilities for APIs. This section describes high-level API Gateway architecture for various deployment scenarios.
Software AG recommends you to view the System Requirements for Software AG Products document and then proceed with the deployment.
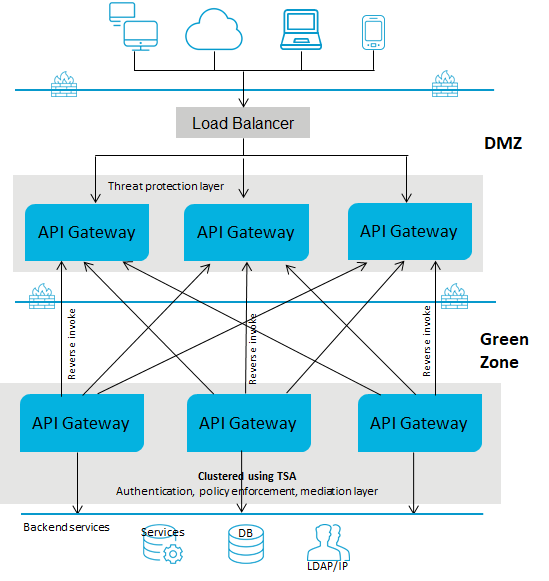
Deployment scenario 1: Paired gateway deployment
This setup consists of:

One or more standard edition
API Gateways for threat protection and connected to a load balancer in DMZ.

One or more advanced version
API Gateways clustered in the green zone to enforce policies and provide routing capabilities. You can have multiple instances of
API Gateways connected through a load balancer and clustered using Terracotta Server Array. You can add an extra layer of protection by using reverse invoke.
A firewall protects the API Gateway infrastructure in the paired deployment. You can add an extra layer of protection by using reverse invoke. The API Gateways communicate between the zones using the reverse invoke approach.
The following diagram provides an architectural overview of the paired gateway deployment:
Note:
If you have multiple instances of API Gateway connected using a load balancer for threat protection and you change the enforced rules on one of the API Gateway instances, you must restart the other instances to synchronize the rule enforcement across all the API Gateway instances.
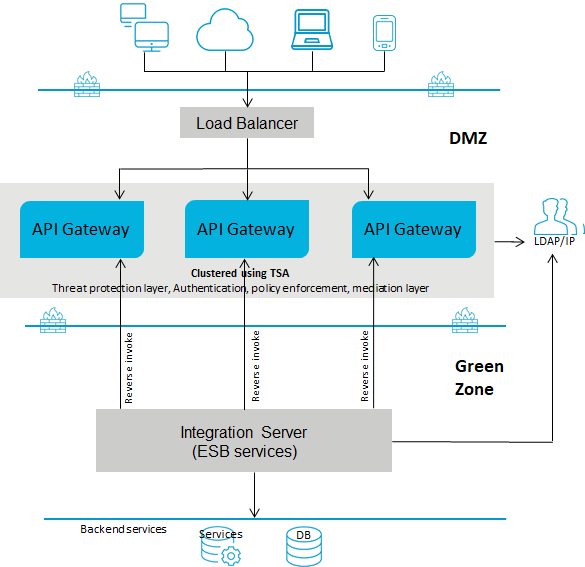
Deployment scenario 2: Single gateway in the DMZ for webMethods customers
This setup consists of:

One or more advanced edition
API Gateways clustered and connected to a load balancer in DMZ. You can have multiple instances of
API Gateways connected through a load balancer and clustered using Terracotta Server Array. A single
API Gateway is used for enforcing authentication and routing capabilities.

The ESB services in
Integration Server reside in the green zone behind the firewall.
If you use reverse invoke for communication between API Gateway and the internal ESB, ensure that the endpoint in the routing policy applied is configured as apigateway://registrationPort-aliasname/relative path of the service. For details, see the Ports section and the Routing policies section in the webMethods API Gateway User's Guide.
The following diagram provides an architectural overview of the API Gateway deployment in a DMZ for webMethods customers:
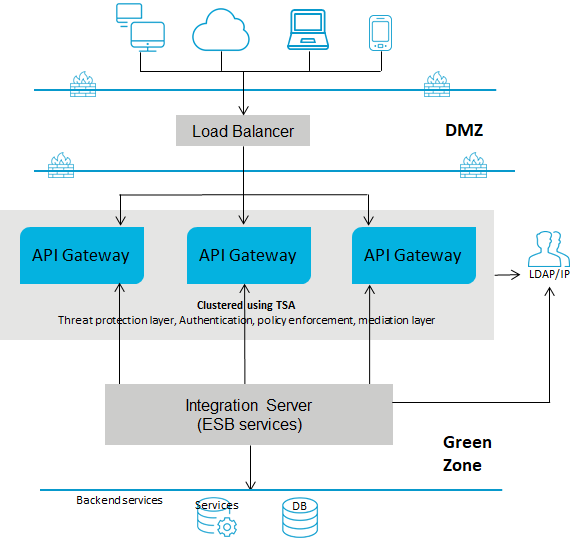
Deployment scenario 3: Single gateway in the green zone for webMethods customers
This setup consists of:

One or more advanced edition
API Gateways clustered in the green zone and connected to a load balancer in DMZ. A single
API Gateway is used for enforcing authentication and routing capabilities. This deployment does not require threat protection. However, you can configure and enforce threat protection, if required. You can have multiple instances of
API Gateways connected through a load balancer and clustered using Terracotta Server Array.

The ESB services in
Integration Server reside in the green zone behind the firewall. Because the
API Gateway and the ESB services reside in the green zone, the ESB services are directly invoked.
The following diagram provides an architectural overview of the API Gateway deployment in the green zone for webMethods customers:
Note:
Because the API Gateway instance and the ESB service are in the same network, you can either directly invoke the ESB service or use the reverse invoke approach as required.
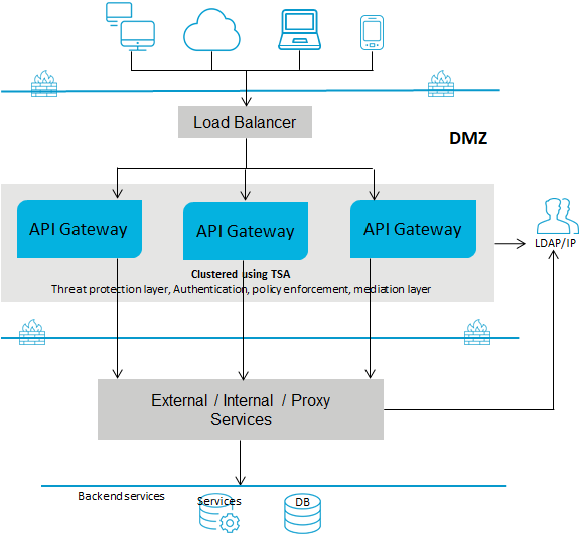
Deployment scenario 4: Single gateway for non-webMethods customers
This setup consists of:

One or more advanced edition
API Gateways clustered and connected to a load balancer in DMZ. A single
API Gateway is used for enforcing all policies or rules. You can have multiple instances of
API Gateways connected through a load balancer and clustered using Terracotta Server Array.

The native services reside in the green zone behind the firewall. As the native services are directly invoked, you must open the native service port to the gateway network.
The following diagram provides an architectural overview of the API Gateway deployment for non webMethods customers: