Configuring Restriction to IP Address based on Authentication
You must have the Manage Security Configuration functional privilege to configure this restriction.
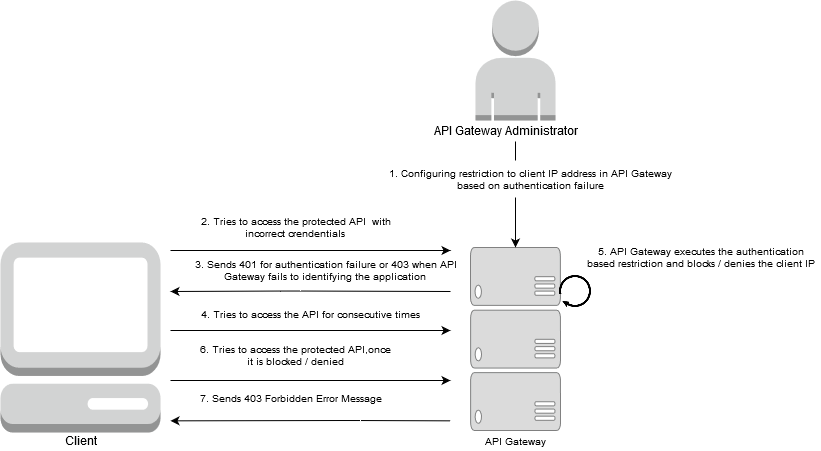
You can configure the restriction to client IP address based on authentication failure in API Gateway to prevent malicious attack that occurs when a client floods a server with many requests in an attempt to interfere with server processing. This restriction prevents the malicious attack by blocking or denying the unauthenticated client from accessing the APIs, when API Gateway fails to authenticate the client. Using API Gateway, you can limit the number of times a client fails to authenticate the API in a specified time interval. The reason for authentication failure can be either of the following:

when
API Gateway fails to authenticate the client (
or)

when
API Gateway fails to identify the client and its respective application.
When the above mentioned authentication failure occurs, API Gateway sends the 401 or 403 error message to the client.
When API Gateway detects that the failed authentication limit has been exceeded, it blocks or denies that particular client IP address from accessing any of the APIs and sends the 403 Forbidden error to the client.
Note:

If an API is enforced with Identify and Access Application policy, and if the invocation fails due to non-preemptive authentication failure.
API Gateway does not take such non-preemptive authentication failure into count and increase the failed authentication count.

When you use Load Balancer for configuring high availability between the
API Gateway instances,
API Gateway honours the X-Forwarded-For (XFF) header from the client. As the XFF header has the actual client IP address,
API Gateway can block or deny the problematic client from accessing the protected API based on your configuration.

To configure restriction to IP address based on authentication
1. Expand the menu options icon  , in the title bar, and select Administration.
, in the title bar, and select Administration. 2. Select Security > Global IP Access Settings.
3. Click Authentication based restrictions - Block/Deny by IP address section and provide the following information.
Field | Description |
Enable | Specifies whether restriction to IP address based on authentication is enabled. Click the toggle button to change the state to  to enable IP address restriction. By default this option is disabled. |
Maximum failed authentication | Specifies the maximum number of failed authentication that API Gateway can accept from a specific IP address in a given time interval. |
In (seconds) | Specifies the time interval, in seconds, in which maximum authentication failure can be permitted. |
Action when limit exceeds | Specifies the action to be performed when the number of failed authentication from an IP address exceeds the specified limits. Select one of the following:  Add IP address to deny list Add IP address to deny list. Permanently denies the IP address from accessing any APIs.  Block the IP address Block the IP address. Temporarily blocks the IP address from accessing any APIs for specified time interval.  In (seconds) In (seconds). Specify the time interval for which you want to block the IP address. |
Denied IP list | Specifies the list of IP addresses that are denied from access. Click  in the Action column to remove an IP address from the denied list. |
4. Click Save.
The configuration is saved.
 to enable IP address restriction.
to enable IP address restriction.