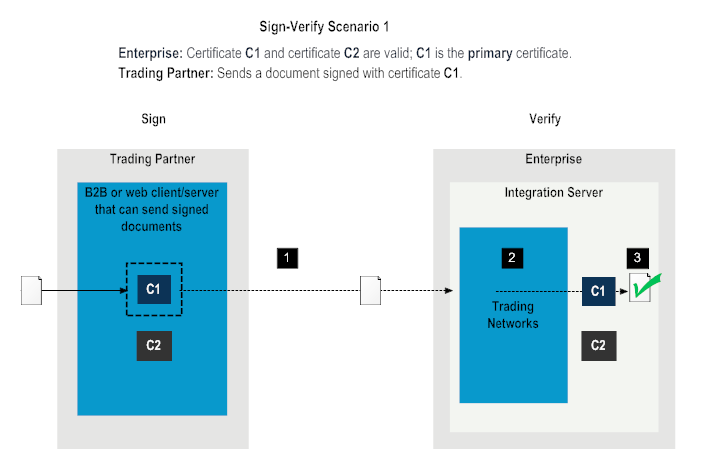
Step | Description |
1 | The trading partner sends a document signed with certificate C1 to the enterprise. |
2 | Trading Networks on the enterprise side retrieves the certificate C1 for the trading partner from Trading Networks. |
3 | Trading Networks on the enterprise side verifies the document with C1. Verification is successful. |
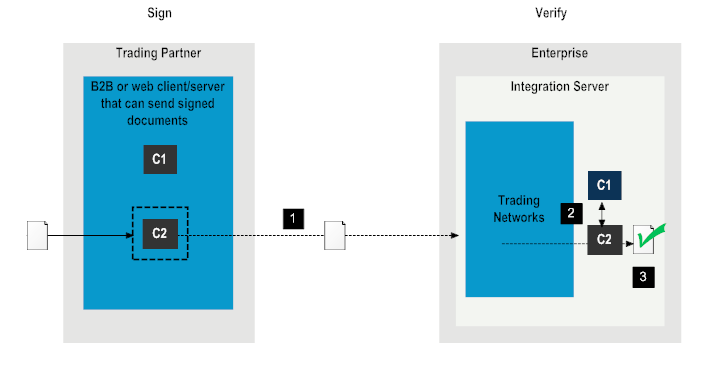
Step | Description |
1 | The trading partner sends a document signed with C2 certificate to the enterprise. |
2 | Trading Networks on the enterprise side switches the primary certificate to C2 and retrieves the certificate C2 because certificate C1 has expired. |
3 | Trading Networkson the enterprise side verifies the document with C2. Verification is successful. |
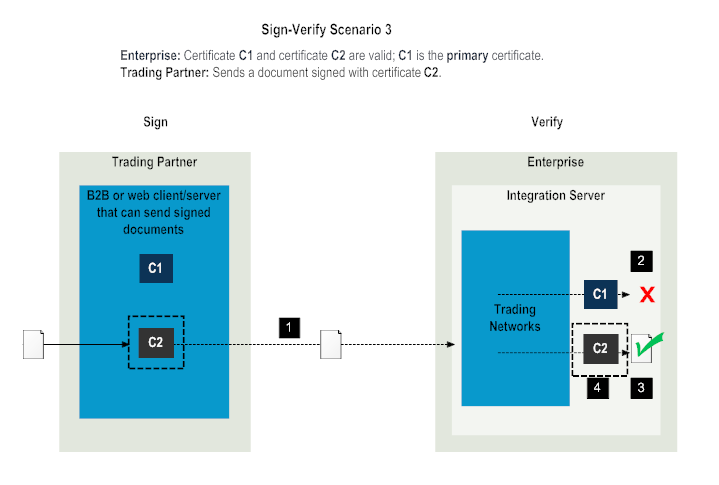
Step | Description |
1 | The trading partner sends a document signed with certificate C2 to the enterprise. |
2 | Trading Networks on the enterprise side retrieves the certificate C1 for the trading partner from Trading Networks and verifies the document with certificate C1. Verification fails as the document is signed with the certificate C2. |
3 | Trading Networks on the enterprise side retrieves the certificate C2 and verifies the document with C2. Verification is successful. |
4 | Trading Networks on the enterprise side sets the certificate C2 as the primary certificate for the trading partner. |
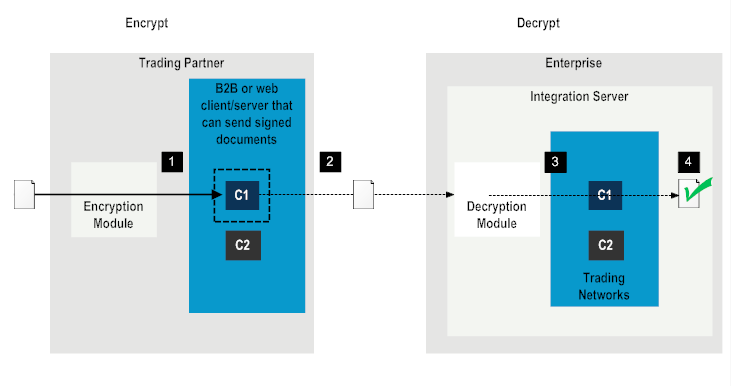
Step | Description |
1 | The encryption module on the trading partner requests the encryption certificate and gets the primary certificate C1. |
2 | The encryption module on the trading partner encrypts the document with the certificate C1 and sends the document to the enterprise. |
3 | The decryption module on the enterprise side requests Trading Networks for the decryption certificate and gets the certificate C1. |
4 | The decryption module on the enterprise side decrypts the document using certificate C1. Decryption is successful. |
Step | Description |
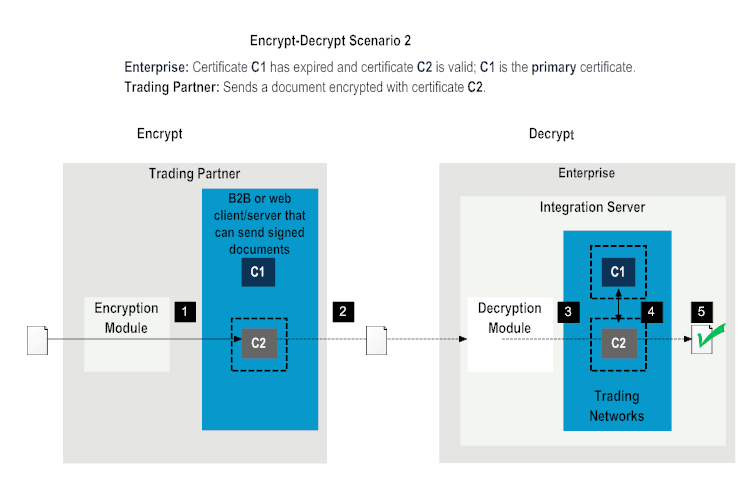
1 | The encryption module on the trading partner requests the encryption certificate and gets the certificate C2 because C1 has expired. |
2 | The encryption module on the trading partner encrypts the document with the certificate C2 and sends the document to the enterprise. |
3 | The decryption module on the enterprise side requests Trading Networks for the decryption certificate. |
4 | Trading Networks on the enterprise side switches the primary certificate to C2 because certificate C1 has expired, and returns C2. |
5 | The decryption module on the enterprise decrypts the document using certificate C2. Decryption is successful. |
Step | Description |
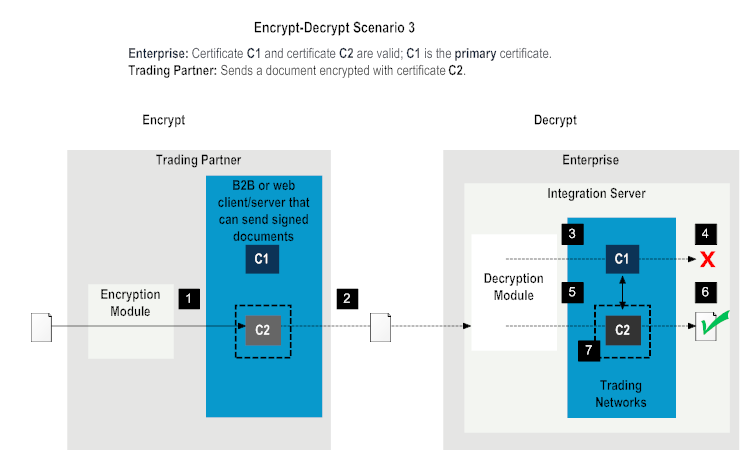
1 | The encryption module on the trading partner requests the encryption certificate and gets the certificate C2. |
2 | The encryption module on the trading partner encrypts the document with the certificate C2 and sends the document to the enterprise. |
3 | The decryption module on the enterprise side requests Trading Networks for the decryption certificate and gets the certificate C1. |
4 | The decryption module on the enterprise side decrypts the document using certificate C1. Decryption fails. |
5 | The decryption module requests for the secondary certificate C2 using the wm.tn.security:getAllCertificateData service. |
6 | The decryption module decrypts the document with certificate C2. Decryption is successful. |
7 | The decryption module calls the Trading Networks setPrimaryCertificate service to switch the primary certificate to C2. |
Step | Description |
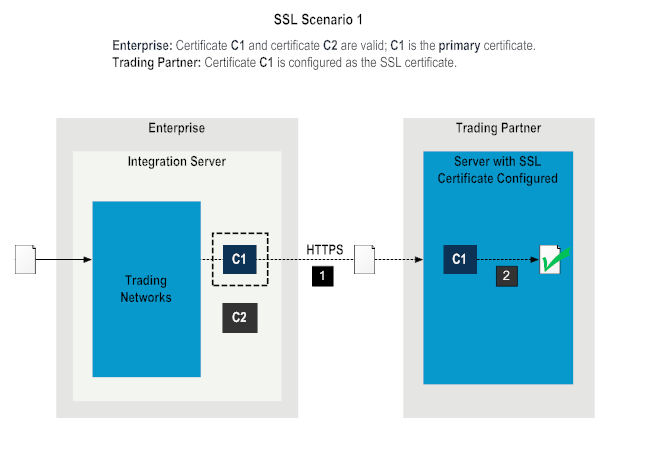
1 | The enterprise sends a document to the trading partner over HTTPS using the private key from certificate C1. |
2 | The trading partner's server authenticates the document using the SSL certificate C1 configured on the server. Authentication is successful and the transaction is complete. |
Step | Description |
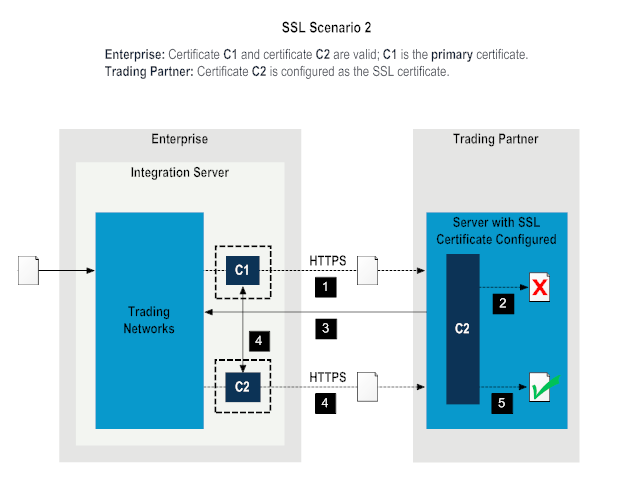
1 | The enterprise sends a secure document to the trading partner over HTTPS using the private key from certificate C1. |
2 | The trading partner's server authenticates the document using the SSL certificate C2 configured on the server. Authentication fails. |
3 | The trading partner's server sends an error message to the enterprise. |
4 | The enterprise switches the SSL certificate to C2 and resends the document to the trading partner over HTTPS. |
5 | The server on the trading partner authenticates the document using the SSL certificate C2 configured on the server. Authentication is successful. The transaction is complete. |