Deploying API Gateway as a Kubernetes Service
This section describes the different deployment models for API Gateway as a Kubernetes service.
With the API Gateway Kubernetes support you can deploy API Gateway in one of the following ways:

A pod with
API Gateway container and an Elasticsearch container.

A pod with
API Gateway container connected to an Elasticsearch Kubernetes service.
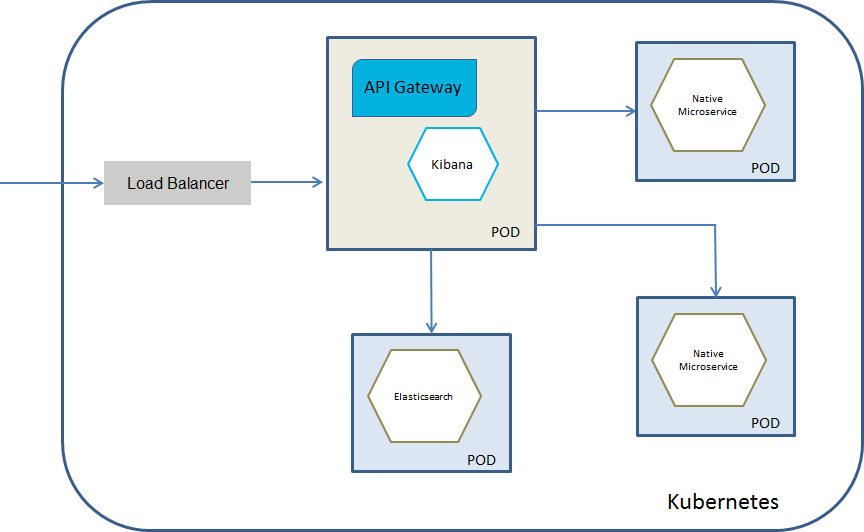
API Gateway pod with API Gateway and Elasticsearch containers
You would select this deployment model if you want API Gateway as a Kubernetes service protecting the native services deployed to Kubernetes. Here, API Gateway runs in dedicated pods, and each pod has Elasticsearch and Kibana containers. API Gateway routes the incoming API requests to the native services. The invocation of the native services by the consumers happens through APIs provisioned by the API Gateway.
The diagram depicts the API Gateway Kubernetes service deployment model where you have a single API Gateway pod that contains API Gateway and Elasticsearch containers. The Kibana can either be embedded in the API Gateway container or can reside as a separate container within the pod.
To deploy API Gateway Kubernetes pod that contains an Elasticsearch container perform these steps:
1. Ensure that the vm.max_map_count variable is set to a value of at least 262144 to run an Elasticsearch container within a pod. This is done in an init container as follows:
initContainers:
- command:
- sysctl
- -w
- vm.max_map_count=262144
image: busybox
imagePullPolicy: IfNotPresent
name: init-sysctl
resources: {}
securityContext:
privileged: true
2. Ensure that you have an API Gateway Docker image and an Elasticseach image for this deployment. For the API Gateway container, the following environment variable has to be set.
apigw_elasticsearch_hosts=localhost:9200
This assumes that Elasticsearch runs on the standard port 9200 and the xpack.security is disabled. The following YAML snippet displays how the environment variable apigw_elasticsearch_hosts is set.
spec:
containers:
- env:
- name: apigw_elasticsearch_hosts
value: localhost:9200
You can disable the xpack.security by setting the environment variable xpack.security.enabled to false for the Elasticsearch container.
The following sample YAML file defines a Kubernetes deployment with a pod that constitutes the API Gateway container apigw, the Elasticsearch container elasticsearch and the init container init-sysctl. For details on Kubernetes YAML files, see Kubernetes documentation.
apiVersion: apps/v1beta2
kind: Deployment
metadata:
name: apigw-elastic-search
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
workload.user.cattle.io/workloadselector:
deployment-gateway-apigw-elastic-search
strategy:
rollingUpdate:
maxSurge: 1
maxUnavailable: 0
type: RollingUpdate
template:
metadata:
labels:
workload.user.cattle.io/workloadselector:
deployment-gateway-apigw-elastic-search
spec:
containers:
- env:
- name: apigw_elasticsearch_hosts
value: localhost:9200
image: apigateway
imagePullPolicy: Always
livenessProbe:
failureThreshold: 3
initialDelaySeconds: 140
periodSeconds: 10
successThreshold: 1
tcpSocket:
port: 5555
timeoutSeconds: 2
name: apigw
ports:
- containerPort: 5555
name: 5555tcp01
protocol: TCP
- containerPort: 9072
name: 9072tcp01
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /rest/apigateway/health
port: 5555
scheme: HTTP
initialDelaySeconds: 140
periodSeconds: 10
successThreshold: 2
timeoutSeconds: 2
resources: {}
securityContext:
allowPrivilegeEscalation: false
capabilities: {}
privileged: false
readOnlyRootFilesystem: false
runAsNonRoot: false
stdin: true
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
tty: true
- env:
- name: xpack.security.enabled
value: "false"
image: docker.elastic.co/elasticsearch/elasticsearch:5.6.4
imagePullPolicy: Always
name: elasticsearch
ports:
- containerPort: 9200
name: 9200tcp01
protocol: TCP
resources: {}
securityContext:
allowPrivilegeEscalation: false
privileged: false
readOnlyRootFilesystem: false
runAsNonRoot: false
stdin: true
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
tty: true
dnsPolicy: ClusterFirst
initContainers:
- command:
- sysctl
- -w
- vm.max_map_count=262144
image: busybox
imagePullPolicy: IfNotPresent
name: init-sysctl
resources: {}
securityContext:
privileged: true
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
terminationGracePeriodSeconds: 30
status: {}
API Gateway pod with API Gateway container connected to an Elasticsearch Kubernetes service
You would select this deployment model if you want to have a separate Elasticsearch service. This deployment allows you to scale Elasticsearch independently or to use an already existing Elasticsearch service. Ensure you have an Elasticsearch Kubernetes service for Elasticsearch 5.6.4.
The diagram depicts the API Gateway Kubernetes service deployment model where you have a separate API Gateway pod that constitutes an API Gateway container connected to an Elasticsearch service. Kibana can run as a separate container within the API Gateway pod or can be embedded in the API Gateway container.
To deploy an API Gateway Kubernetes pod that communicates with an Elasticsearch Kubernetes service, perform these steps:
1. Ensure you have an Elasticsearch Kubernetes service for Elasticsearch 5.6.4.
For more details on deploying Elasticsearch on Kubernetes, see Elasticsearch and Kubernetes documentation.
2. Ensure you have an API Gateway Docker image for this deployment. For the API Gateway container, the following environment variable has to be set.
apigw_elasticsearch_hosts=elasticsearch-host:elasticsearch-port
A sample YAML file that has API Gateway communicating with an external Elasticsearch service is as follows:
apiVersion: apps/v1beta2
kind: Deployment
metadata:
name: apigateway-external-elasticsearch
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
workload.user.cattle.io/workloadselector:
deployment-gateway-apigw-external-elastic-search
strategy:
rollingUpdate:
maxSurge: 1
maxUnavailable: 0
type: RollingUpdate
template:
metadata:
labels:
workload.user.cattle.io/workloadselector:
deployment-gateway-apigw-external-elastic-search
spec:
containers:
- env:
- name: apigw_elasticsearch_hosts
value: 10.20.198.90:30999
image: apigateway
imagePullPolicy: Always
livenessProbe:
failureThreshold: 6
initialDelaySeconds: 60
periodSeconds: 10
successThreshold: 1
tcpSocket:
port: 5555
timeoutSeconds: 2
name: apigateway-external-elasticsearch
ports:
- containerPort: 5555
name: 5555tcp01
protocol: TCP
- containerPort: 9072
name: 9072tcp01
protocol: TCP
readinessProbe:
failureThreshold: 6
httpGet:
path: /rest/apigateway/health
port: 5555
scheme: HTTP
initialDelaySeconds: 60
periodSeconds: 10
successThreshold: 2
timeoutSeconds: 2
resources: {}
securityContext:
allowPrivilegeEscalation: false
capabilities: {}
privileged: false
readOnlyRootFilesystem: false
runAsNonRoot: false
stdin: true
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
tty: true
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
terminationGracePeriodSeconds: 30
status: {}