How do I onboard users using their SAML service provider credentials?
You can enable SSO using one of the following applications:

Okta

PingIdentity

Azure
This use case begins when you want to allow users to onboard using their SSO credentials and ends when you have completed the configuration.
In this example, you enable SSO for user with their Okta credentials.
Before you begin:
Ensure that you:

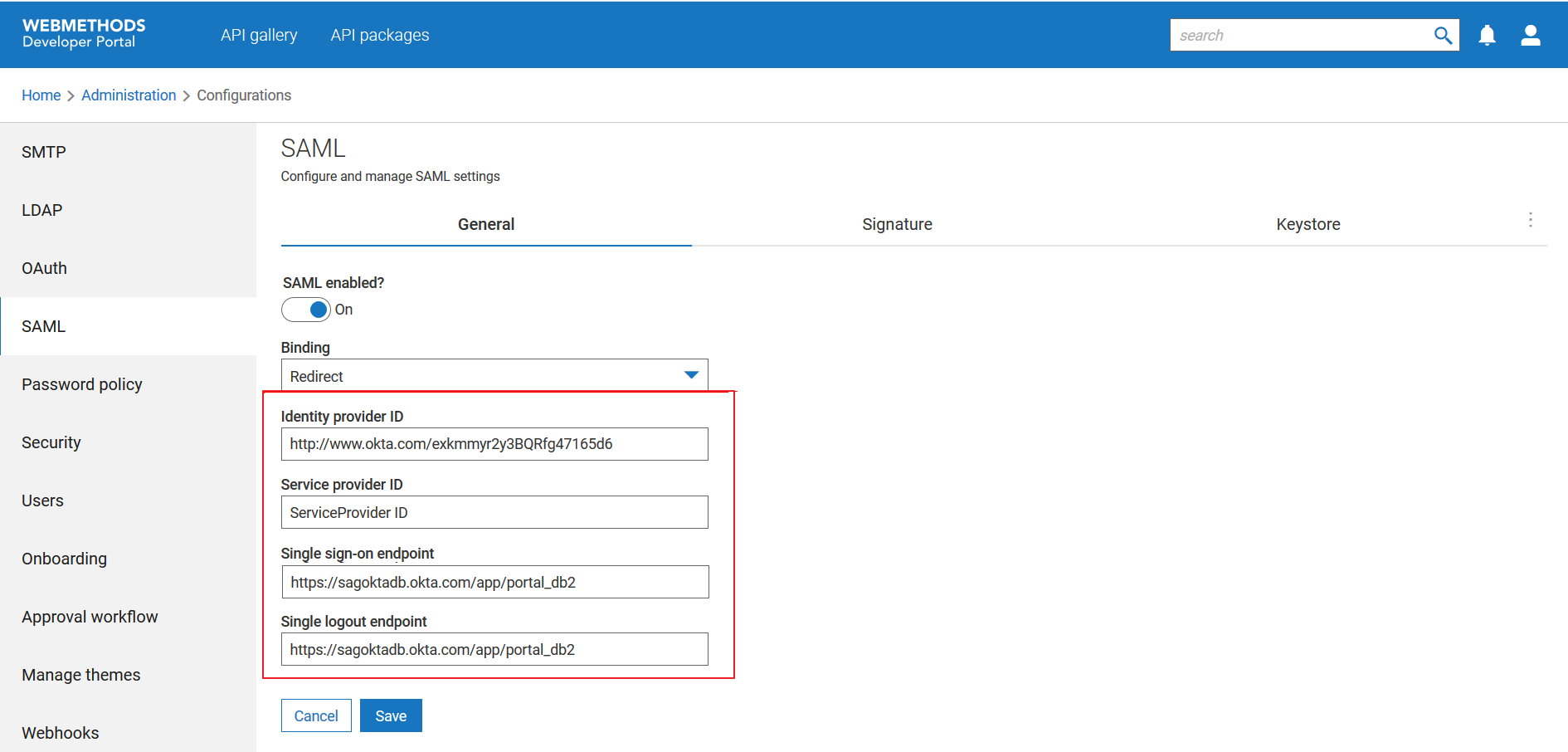
Enable SAML. You can enable SAML by turning the
SAML active slider on.

Create an application in Okta to register the service provider application (
Developer Portal) in the Okta, and keep the
Identity Provider Single Sign-on URL and
Identity Provider Issuer values ready. For information on creating an application in Okta, see https://developer.okta.com/docs/guides/add-an-external-idp/apple/register-app-in-okta/.
 To enable SSO onboarding using Okta credentials
To enable SSO onboarding using Okta credentials:
1. Click the menu options icon

from the title bar and click
Administration.
2. Select SAML.
3. Select Redirect from the Binding list.
4. Provide the following values copied from Okta SSO application that you created for Developer Portal:
 Identity provider Id
Identity provider Id. Id of the identity provider.
 Service provider Id
Service provider Id. Id of the service provider. This must be same as the value you specify in Okta.
 Single sign-on endpoint
Single sign-on endpoint and
Single logout endpoint. Endpoints that the identity provider must use to send single sign-on and logout payloads.
5. Click Save.
Your changes are saved.
Alternative steps:

Enable SSO to allow users to sign in to
Developer Portal using their PingIdentity or Azure AD credentials.
You must create an application in Okta to register the service provider application (Developer Portal) in the required service provider and provide the Identity Provider Single Sign-on URL and Identity Provider Issuer values in the SAML section:

For information on creating an application in PingIdentity, see https://docs.pingidentity.com/bundle/integrations/page/che1563995024790.html.

For information on creating an application in Azure Active Directory, see https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app.
Next steps:

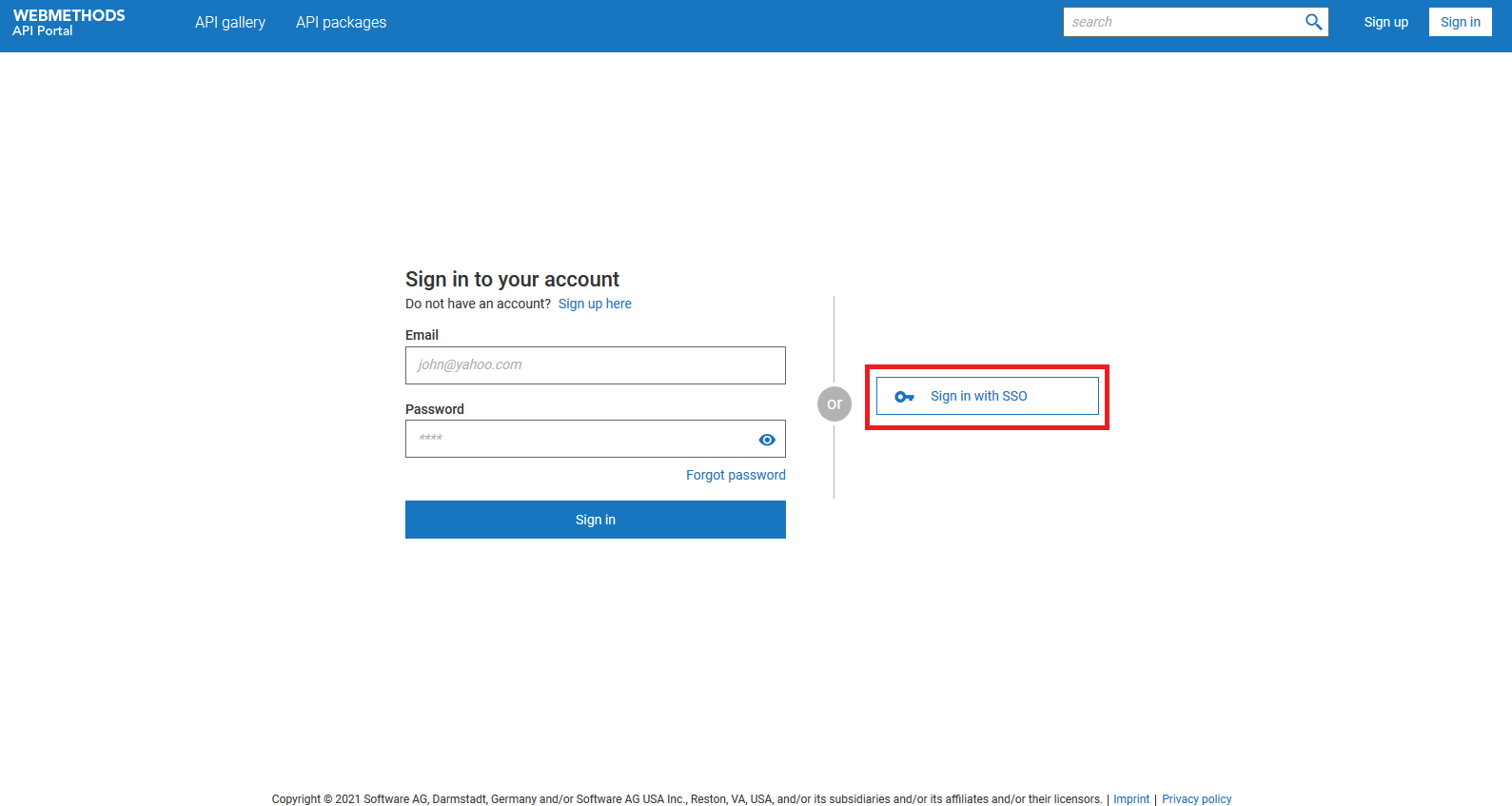
The
Sign in with SSO button appears in the
Sign in page.
User can click this button, provide their Okta credentials to sign up to Developer Portal. The sign up request goes through the onboarding strategy.
 from the title bar and click Administration.
from the title bar and click Administration.