Configuring OAuth2 Authentication with Refresh Token
This use case explains how to secure the API using OAuth2 authentication strategy with authorization_code and refresh_token grant types.
The use case starts when you create an API and ends when you create an application strategy with OAuth2 authentication scheme.

To configure OAuth2 Authentication with Refresh Token
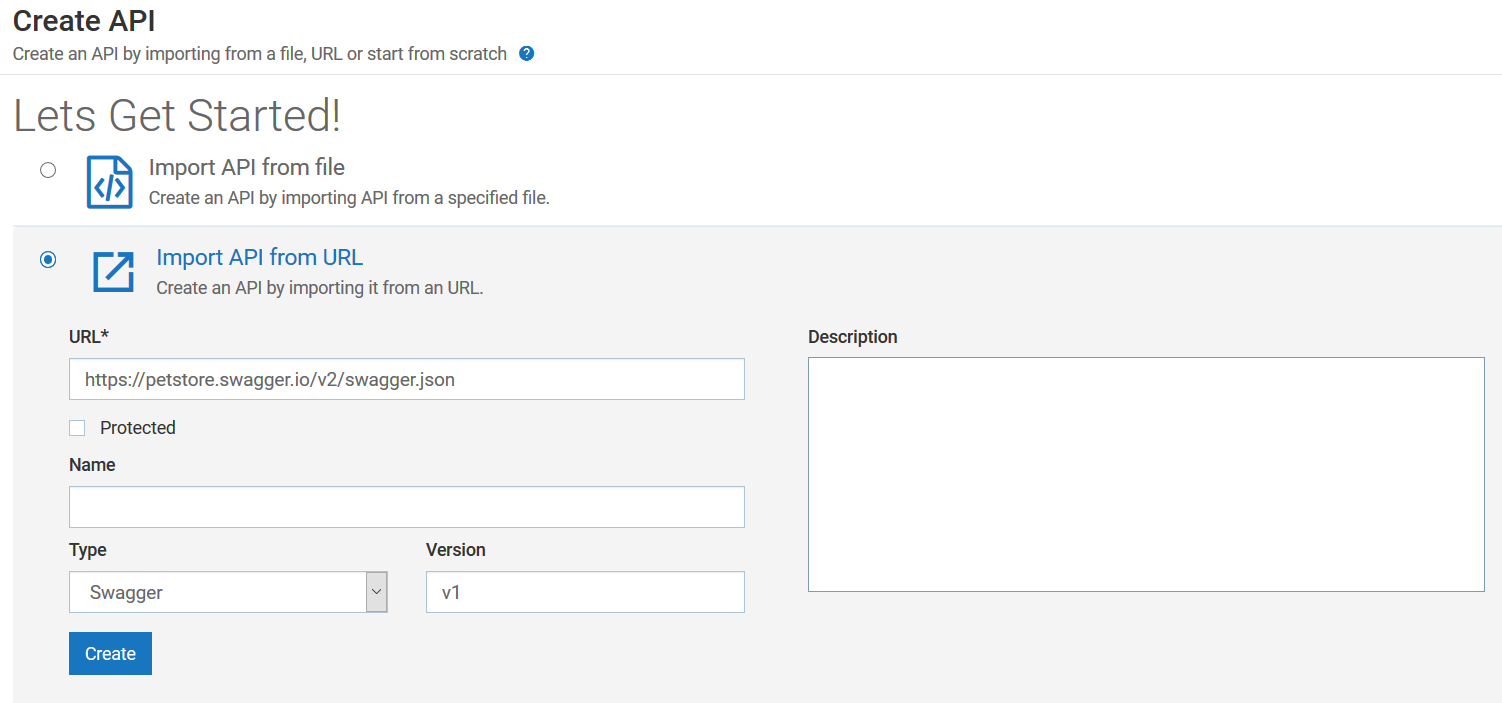
1. Create an API.
For details about creating an API, see
Creating a REST API.
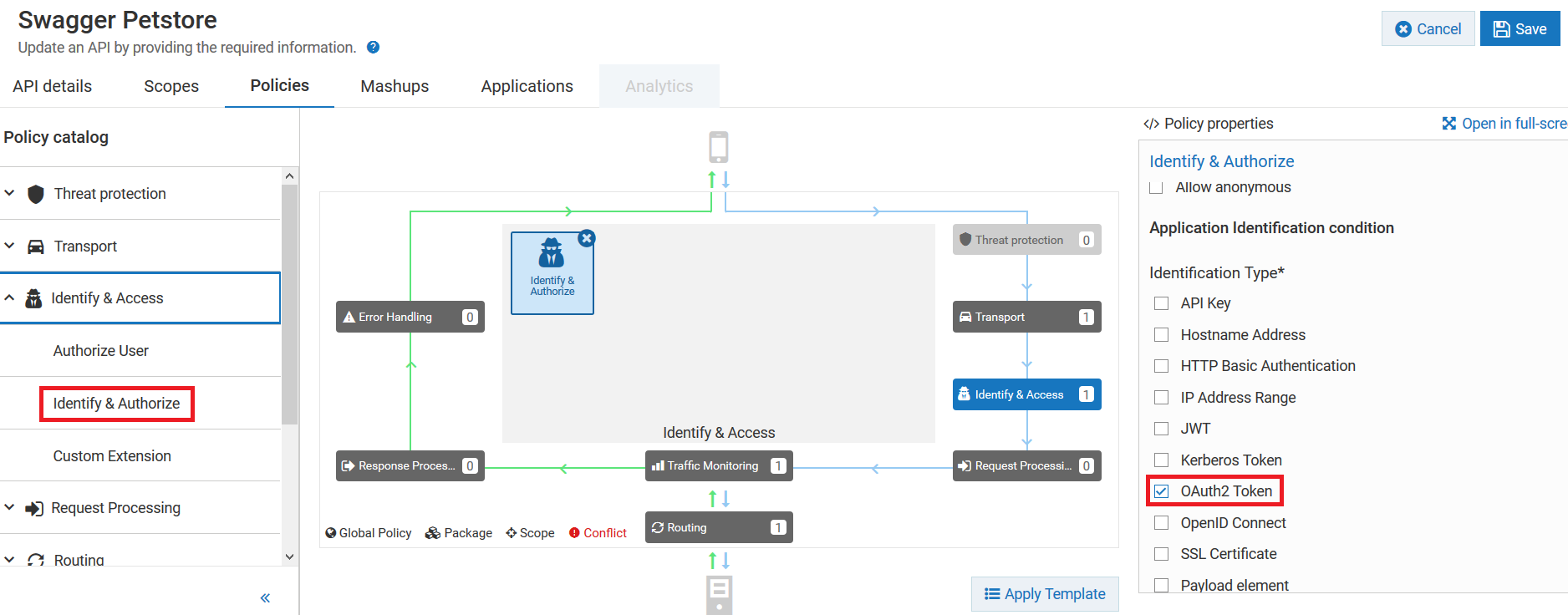
2. Enable the OAuth2 token identification type in the Identify & Authorize policy.
For details about
Identify & Authorize policy, see
Identify & Authorize.
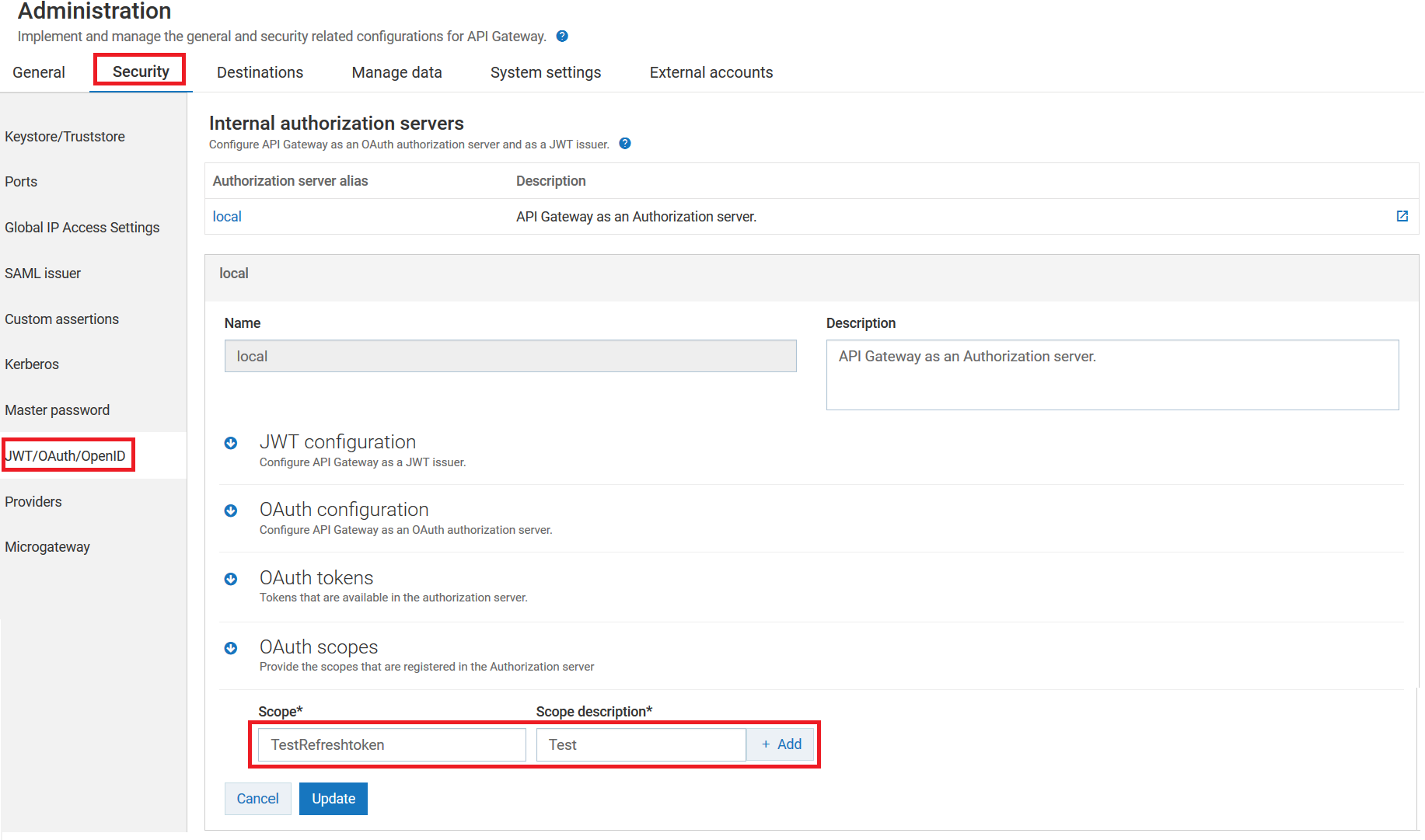
3. Create OAuth scope in the local authorization server.
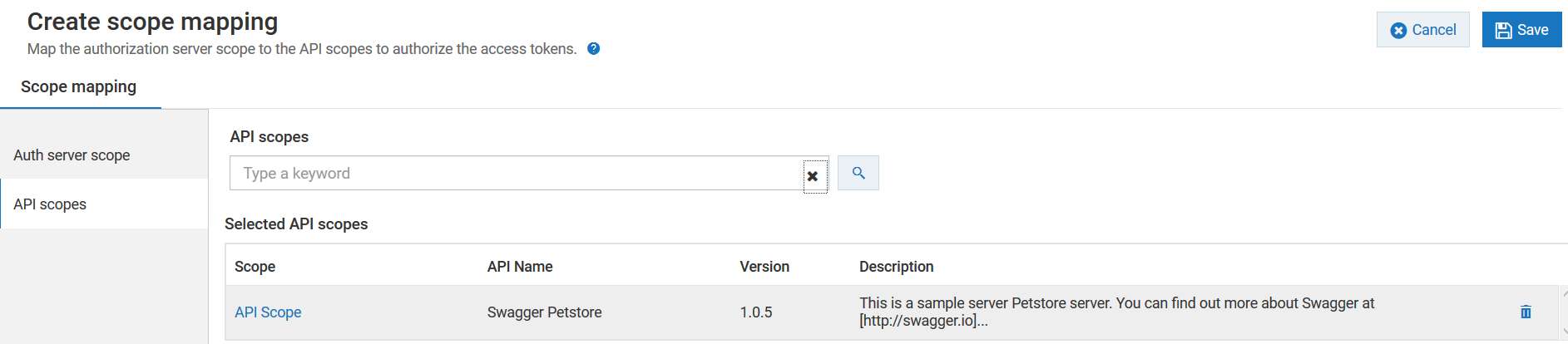
4. Map the OAuth scope to the API scope.
For details about mapping OAuth scope, see
Mapping OAuth or OpenID Scopes.
5. Create an application with OAuth2 authentication strategy.
a. Create a new application.
For details about creating an application, see
Creating an Application.
b. Associate the application with the API that you have created.
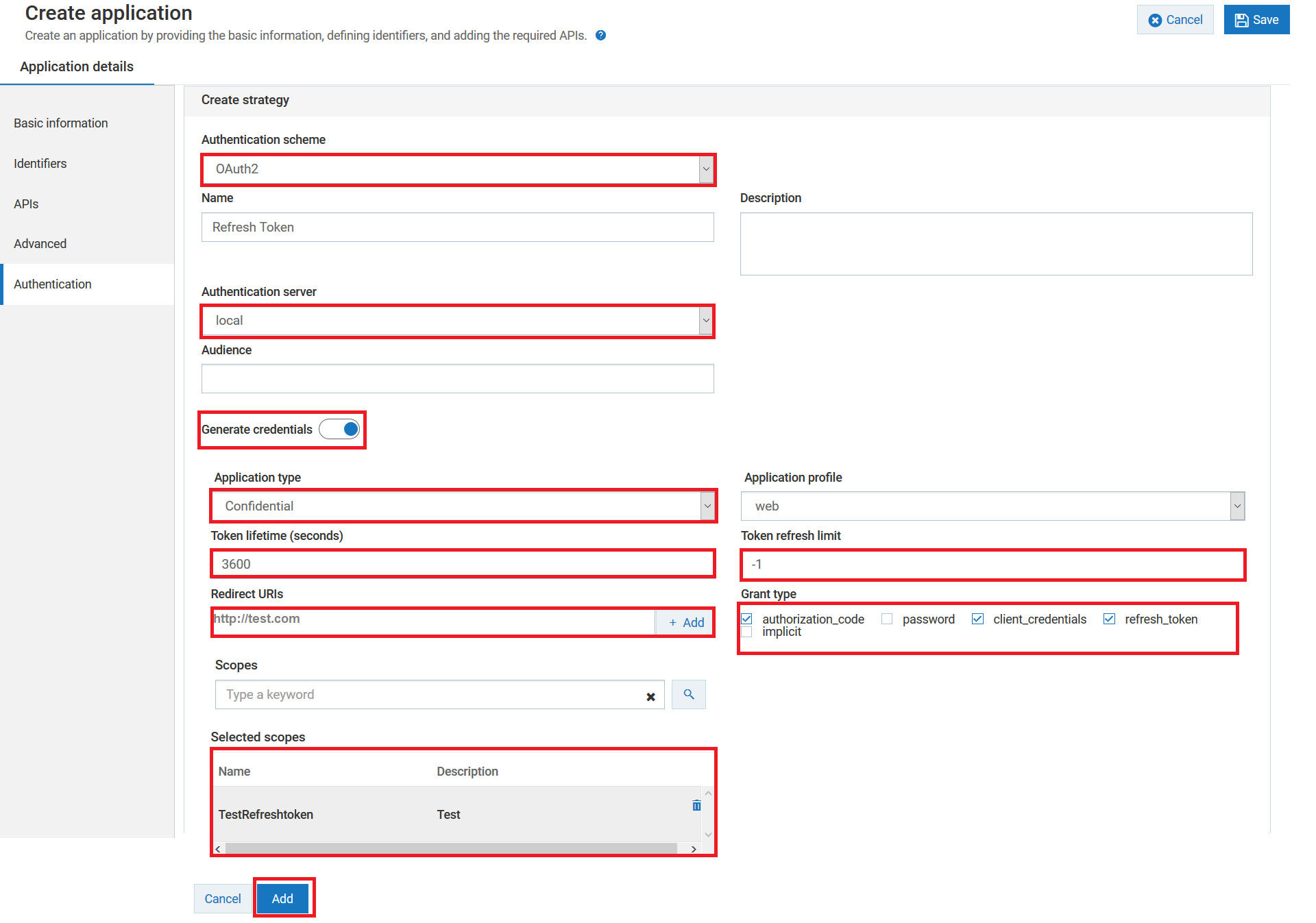
c. Click the Authentication tab to create strategy with OAuth2 authentication.
d. Select the Authentication schemes as OAUTH2.
e. Specify the Authentication server as local.
f. Enable the Generate credentials toggle button to generate the client dynamically in the authorization server and provide the following information:
a. Select the Application Type as Confidential. A confidential client is an application that can keep a client password confidential to the world. This client password is assigned to the client app by the authorization server. This password is used to identify the client to the authorization server, to avoid fraud. An example of a confidential client could be a web app, where no one but the administrator can get access to the server, and see the client password.
b. Select the application profile from the Application profile drop-down menu. For example, web.
c. Specify the duration in seconds for which the access token is active in the Token lifetime (seconds).
d. Specify the number of times you can use the refresh token in the Token refresh limit to get a new acceswws token.
Note:
To use refresh token unlimitedly, specify the limit as -1.
e. Specify the URIs that the authorization server can use to redirect the resource owner's browser during the grant process. You can add multiple URIs by clicking +Add.
f. Specify the grant type to be used to generate the credentials. For this specific use case, we have selected authorization_code, client_credentials, and refresh_token, which are dynamically populated from the authorization server.
Note:
Make sure you have selected refresh_token grant_type, if you want to get the refresh tokens.
g. Select the scopes that are to be mapped for the authentication strategy.
h. Click Add to save the strategy.
i. Click Save to save the application.