Generating Azure Storage SAS Tokens while configuring connections
From the CloudStreams v10.15 release, you can generate shared access signature (SAS) tokens while configuring a connection to Microsoft Azure Storage, from the connection configuration page in webMethods Integration Server Administrator.
webMethods CloudStreams allows you to generate the following types of SAS tokens:
 Account SAS Token
Account SAS Token - Access to more than one service in a storage account at the same time is provided. For more information, see the
Generating Account SAS Tokens section.
 Service SAS token
Service SAS token - Access to a resource in a storage service is provided. For more information, see the
Generating Service SAS tokens section.
Prerequisites

Install
CloudStreams Server v10.15 or a later version with the latest fix level.

Install the supported v10.15
CloudStreams Provider.
Generating Account SAS tokens
1. While configuring a connection to Microsoft Azure Storage, on the Configure Connection page in webMethodswebMethods Integration Server Administrator, select Microsoft Azure Storage Account SAS Connection from the Connection Type drop-down menu.
2. On the Connection Groups: Azure Account SAS section, click Generate SAS Token.
The Azure Account SAS Flow dialog box appears.
3. Fill in values for the required fields as per the following instructions:
 Account Name
Account Name: Specify the storage account name in Azure. This is a required field.
 Account Key
Account Key: Specify the account key associated with your account SAS. This is a required field.
 Signed Services
Signed Services: Select the signed services that are accessible with the account SAS. Allowed values include: Blob, Queue, Table, File.
Alternatively, you could provide access to more than one service by choosing combined values. This is a required field.
 Signed Resource Types
Signed Resource Types: Select the signed resource types that are accessible with the account SAS. Allowed values include:

Service: Access to service-level APIs is provided.

Container: Access to container-level APIs is provided.

Object: Access to object-level APIs for blobs, queue messages, table entities, and files is provided.
Alternatively, you could provide access to more than one resource type by choosing combined values. This is a required field.
 Signed Permission
Signed Permission: Select the signed permissions associated with the account SAS. This is a required field.
Note:
Ensure that the permissions match the specified signed resource type. If the permissions do not match, they will be ignored.

Read: Read a resource. This permission is valid for all signed resource types (Service, Container, and Object).

Write: Grant write access for users to the specified resource type. This permission is valid for all signed resources types (Service, Container, and Object).

Delete: Delete a resource. This permission is valid for Container and Object resource types, except for queue messages.

Permanent Delete: Permanently delete a resource. This permission is valid for Object resource type of Blob only.

List: List objects within a resource. This permission is valid for Service and Container resource types only.

Add: Add or append to an existing resource. This permission is valid for the Object resource types - queue messages, table entities, and append blobs.

Create: Create a new resource. This permission is valid for the Object resource types - blobs and files.
Note:
You can create new blobs or files, but may not overwrite existing blobs or files.

Update: Update an existing resource. This permission is valid for the Object resource types - queue messages and table entities.

Process: This permission is valid for the Object resource type - queue messages.

Tag: Allow users to perform blob tag operations. This permission is valid for the Object resource type - blobs.

Filter: Allow users to perform filtering by blob tag. This permission is valid for the following Object resource type only: blob.

Set Immutability Policy: Allow users to set/delete immutability policy and legal hold on a blob. This permission is valid for the Object resource type: blob.
 Signed Start
Signed Start: Specify the start time at which the SAS becomes valid. If this field is left empty, the start time will be effective when the request is received by the service. This is an optional field.
Note:
The value for this field should be expressed in one of the accepted ISO 8601 UTC formats.
 Signed Expiry
Signed Expiry: Specify the expiry time after which the SAS becomes invalid. This is a required field.
Note:
The value for this field should be expressed in one of the accepted ISO 8601 UTC formats.
 Signed IP
Signed IP: Specify the public IP address or a range of IP addresses from which to accept requests. This is an optional field. For example, sip=170.1.5.65 or sip=166.1.5.70-169.1.5.80.
Note:
Ensure that the range of IP addresses is inclusive.
Note:
The value specified for the Signed IP field is verified by the SaaS provider to check if a request has originated from a valid IP address/IP range. To ensure that your request is not blocked by the SaaS provider, you will need to add the public IP address or a range of IP addresses in the Azure portal. To do so, follow the steps given below:
1. Login to your Microsoft Azure account. Go to the storage account where you want to add a valid public IP address or a range of IP addresses.
2. Locate the Networking settings under Security + networking.
3. Under Firewall and Virtual Networks section, select Enabled from selected virtual networks and IP addresses.
4. In the Firewall option, add a valid IP address or a range of IP addresses and then select Save to apply your changes.
Next, provide the same IP address or the range of IP addresses in the Signed IP field as specified in Microsoft Azure portal.
 Signed Protocol
Signed Protocol: Select the HTTP protocol that is allowed for a request made with the account SAS. This is an optional field.
Possible values: Both HTTPS and HTTP (https, http) or HTTPS only (https).
Default value: https, http Note: HTTP only is not permitted and cannot be specified.
 Signed Encryption Scope
Signed Encryption Scope: Specify the encryption scope you want to use to encrypt the contents of a request. This is an optional field.
Supported versions: 2020-12-06 and later.
4. Click Get Token.
The generated Account SAS token will be sent to the authentication server and the fields in the Connection Groups: Azure Account SAS section will be populated after a successful response from the SaaS provider.
Generating Service SAS tokens
1. While configuring a connection to Microsoft Azure Storage, on the Configure Connection page in webMethodswebMethods Integration Server Administrator, select Microsoft Azure Storage Service SAS Connection from the Connection Type drop-down menu.
2. On the Connection Groups: Azure Service SAS section, click Generate SAS Token.
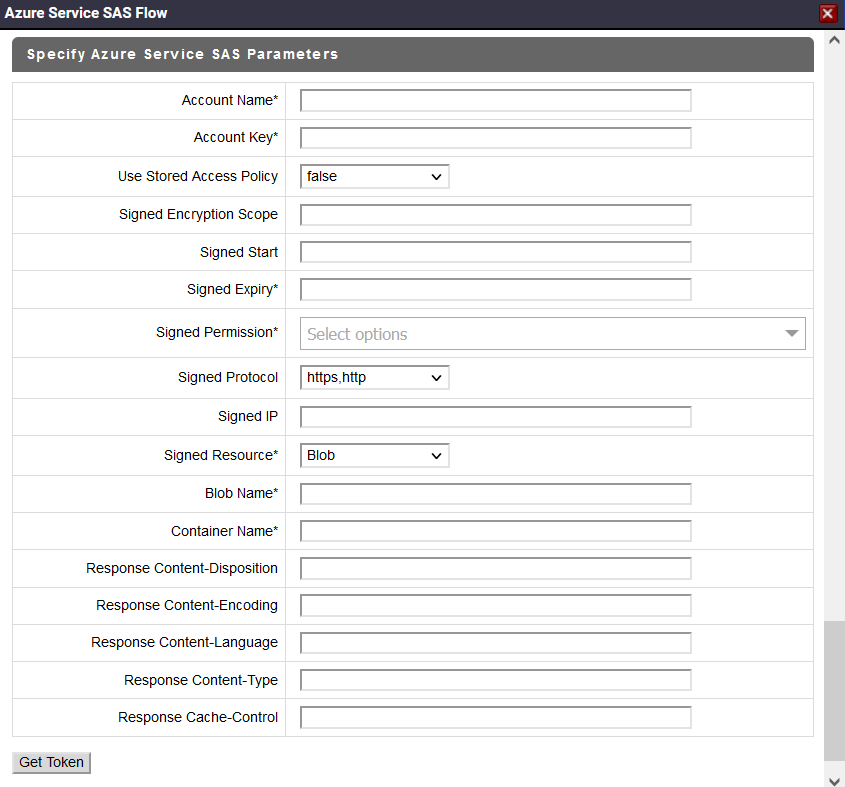
The Azure Service SAS Flow dialog box appears.
3. Fill in values for the required fields as per the instructions given below:
 Account Name
Account Name: Specify the storage account name in Azure. This is a required field.
 Account Key
Account Key: Specify the account key associated with your account SAS. This is a required field.
 Use Storage Access Policy
Use Storage Access Policy: Specify if you want to secure the SAS using the storage access policy. If this field is set to true, the following field appears on the screen:
 Signed Identifier
Signed Identifier: Provide a unique value that associates with an access policy specified for a container, queue, or table. This is an optional field.
Note:
The value for this field should be up to 64 characters.
 Signed Encryption Scope
Signed Encryption Scope: Specify the encryption scope you want to use to encrypt the contents of a request. This is an optional field.
 Signed Start
Signed Start: Specify the start time at which the SAS becomes valid. If this field is left empty, the start time will be effective when the request is received by the service. This is an optional field.
Note:
The value for this field should be expressed in one of the accepted ISO 8601 UTC formats.
 Signed Expiry
Signed Expiry: Specify the expiry time after which the SAS becomes invalid. This is a required field.
Note:
The value for this field should be expressed in one of the accepted ISO 8601 UTC formats.
 Signed Permission
Signed Permission: Select the signed permissions that are associated with the service SAS. This is a required field.
Note:
Ensure that this field is omitted if it has been specified in an associated stored access policy.
 Signed Protocol
Signed Protocol: Select the HTTP protocol that is allowed for a request made with the service SAS. This is an optional field.
Possible values: Both HTTPS and HTTP (https, http) or HTTPS only (https).
Default value: https, http Note: HTTP only is not permitted and cannot be specified.
 Signed IP
Signed IP: Specify the public IP address or a range of IP addresses from which to accept requests. This is an optional field. For example, sip=170.1.5.65 or sip=166.1.5.70-169.1.5.80.
Note:
Ensure that the range of IP addresses is inclusive.
Note:
The value specified for the Signed IP field is verified by the SaaS provider to check if a request has originated from a valid IP address/IP range. To ensure that your request is not blocked by the SaaS provider, you will need to add the public IP address or a range of IP addresses in the Azure portal. To do so, follow the steps given below:
1. Login to your Microsoft Azure account. Go to the storage account where you want to add a valid public IP address or a range of IP addresses.
2. Locate the Networking settings under Security + networking.
3. Under Firewall and Virtual Networks section, select Enabled from selected virtual networks and IP addresses.
4. In the Firewall option, add a valid IP address or a range of IP addresses and then select Save to apply your changes.
Next, provide the same IP address or the range of IP addresses in the Signed IP field as specified in Microsoft Azure portal.
 Signed Resource
Signed Resource: Select the signed resource you want to access with the SAS. Allowed values include:

Blob: Access to contents and metadata of a blob in an account is provided.

Container: Access to contents and metadata of blobs inside a container in an account is provided.

File: Access to contents and metadata of a file is provided.

Queue: Access to contents and metadata of a queue is provided.

Table: Access to contents and metadata of a table is provided.
The following fields appear when you select Blob as the signed resource:
 Blob Name
Blob Name: Enter the name you want to specify for a blob.
 Container Name
Container Name: Enter the name you want to specify for a container.
 Response Content-Disposition
Response Content-Disposition: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Type
Response Content-Type: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Encoding
Response Content-Encoding: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Language
Response Content-Language: Enter the response header you want to specify when the SAS is used in a request.
 Response Cache-Control
Response Cache-Control: Enter the response header you want to specify when the SAS is used in a request.
The following fields appear when you select Container as the signed resource:
 Container Name
Container Name: Enter the name you want to specify for a container.
 Response Content-Disposition
Response Content-Disposition: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Type
Response Content-Type: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Encoding
Response Content-Encoding: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Language
Response Content-Language: Enter the response header you want to specify when the SAS is used in a request.
 Response Cache-Control
Response Cache-Control: Enter the response header you want to specify when the SAS is used in a request.
The following fields appear if you select File as the signed resource:
 File Name
File Name: Enter the name you want to specify for a file.
 Response Content-Disposition
Response Content-Disposition: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Type
Response Content-Type: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Encoding
Response Content-Encoding: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Language
Response Content-Language: Enter the response header you want to specify when the SAS is used in a request.
 Response Cache-Control
Response Cache-Control: Enter the response header you want to specify when the SAS is used in a request.
The following fields appear if you select Queue as the signed resource:
 Queue Name
Queue Name: Enter the name you want to specify for a queue.
The following fields appear if you select Share as the signed resource:
 Share Name
Share Name: Enter the name you want to specify for a share.
 Response Content-Disposition
Response Content-Disposition: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Type
Response Content-Type: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Encoding
Response Content-Encoding: Enter the response header you want to specify when the SAS is used in a request.
 Response Content-Language
Response Content-Language: Enter the response header you want to specify when the SAS is used in a request.
 Response Cache-Control
Response Cache-Control: Enter the response header you want to specify when the SAS is used in a request.
The following fields appear if you select Table as the signed resource:
 Table Name
Table Name: Enter the name you want to specify for a table.
 StartPk
StartPk: Enter the minimum partition key that is accessible with this SAS.
 StartRk
StartRk: Enter the minimum row key that is accessible with this SAS.
 EndPk
EndPk: Enter the maximum partition key that is accessible with this SAS.
 EndRk
EndRk: Enter the maximum row key that is accessible with this SAS.
4. Click Get Token.
The generated Service SAS token will be sent to the authentication server and the fields in the Connection Groups: Azure Service SAS section will be populated after a successful response from the SaaS provider.