Design/Change-Time Policies Usage
Using Policies to Initiate Reviews and Approvals
Enforcing a review and approval process is a common use of a Design/Change-Time policy. To create this type of policy, you include one of CentraSite's approval actions in the policy. An approval action identifies the group of users (the approver group) whose approval is required in order to complete the policy successfully. When you configure an approval policy, you can specify whether approval is required from just one approver in the group or from all approvers in the group.
You apply approval polices to PreStateChange events. Thus, to use approval policies on assets, those assets must be under lifecycle management.
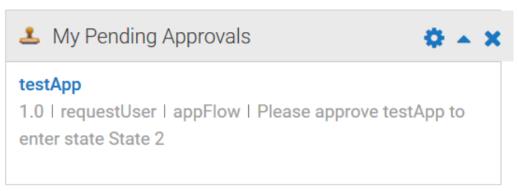
When CentraSite executes an approval policy, it initiates an approval workflow. Users who are designated approvers review the request on the My Pending Approvals widget in the CentraSite Business UI's welcome page. If the approvers approve the request, CentraSite executes the requested state change. If an approver rejects the request, the policy fails and the requested state change is not executed. Pending approvals appear in the My Pending Approvals widget in the CentraSite Business UI's welcome page as shown in the figure:
Using Policies to Validate Assets
Validation is another common task that you can perform using Design and Change-Time policies. You use validation policies to ensure that assets conform to organizational norms and standards before they are accepted into the catalog or enter a critical lifecycle state. For example, you may create validation policies to:

Ensure that a service satisfies certain naming conventions, that it exists within a specified namespace or supports specified protocols.

Ensure that an asset has been classified by a specified taxonomy and includes required attribute settings.

Ensure that a service complies with Web Service Interoperability (WS-I) standards (Basic Profile 1).

Prevent an asset from being deleted unless it has reached a specified state within its lifecycle.
CentraSite provides built-in actions that you can use to perform many validation tasks. You can also create custom actions to perform validation tasks that are specific to your environment.
Using Policies to Modify Assets
You can use Design/Change-Time policies to make changes to assets when certain events occur. Setting instance-level permissions on an asset is an example of an update you may incorporate using a policy. Other kinds of changes you may incorporate include classifying an asset, setting a specified attribute when an asset completes a series of tests, and changing an asset's lifecycle state.
CentraSite provides built-in actions that you can use to perform many kinds of updates to assets. You can also create custom actions to modify assets.
Using Policies to Issue Notifications or Update External Systems
Notifying individuals when certain events occur in the registry is another common use case for Design/Change-Time policies. CentraSite includes a built-in email action that you can use for this purpose.
You may, for example, use this action to send an email to key users in your IT organization when a service switches to the Production state of its lifecycle. You may also create custom actions that would send messages to and trigger processes on external systems when certain events occur in the CentraSite registry.
Using Policies to Execute a Consumer Registration
The consumer-registration feature in CentraSite enables users to register users and applications as consumers of an asset. This enhanced feature enables you to complete the registration process without explicitly creating a consumer-registration policy and without requiring the owner of the asset to review and accept the registration request.
If you want to impose an approval process on the consumer registration feature, you might create a design-time policy with one of the CentraSite's built-in approval actions for the OnConsumerRegistration event. This policy includes the Register Consumer action, which performs the actual registration process. It can optionally include other actions, such as Set Consumer Permission action, as needed.
Using Policies to Manage the Deployment of Virtual Services
If you use virtual services that are enabled with the LCM, you must create policies that enable an administrator to deploy a virtual service to webMethods API Gateway and to make a virtual service undeployable while it is being revised.