Territory ACLs
You use territory ACLs to control which Brokers can join a territory. When a territory has an ACL attached, the basic authentication identity or the SSL identity of any Broker attempting to join must be listed on the territory ACL. If not, the Broker will be denied permission.
Brokers within a territory that belong to the same Broker Server share the same basic authentication identity or SSL identity as that of their Broker Server. This is because a Broker Server's identity is copied to all of its Brokers in the territory.
A territory ACL is shared among all the Brokers in the same territory. When you change the territory ACL on a particular Broker, that ACL is automatically propagated to the rest of the territory.
If you plan on opening the membership of the territory to additional Brokers, specifying their identities on a territory ACL is necessary if the enlisting Brokers have identities different than those specified by the ACL. If that is the case:

Make sure that the
Broker Server(s) of the enlisting
Brokers have either basic authentication identities or SSL identities.

Make sure that either basic authentication or SSL is enabled for those
Broker Servers.

Add the basic authentication identities or SSL identities of the
Brokers you want to add to the territory ACL.
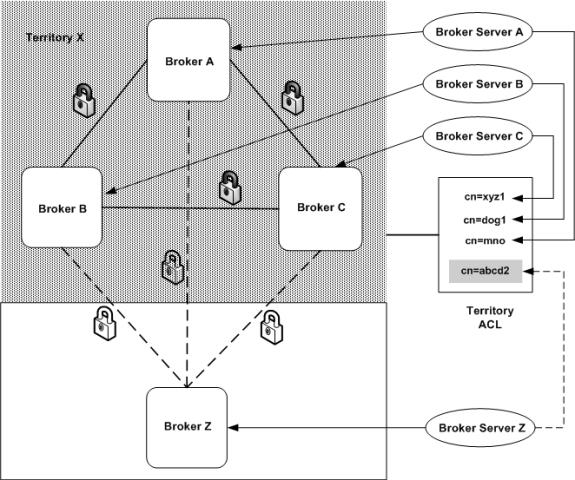
The following figure illustrates the process of adding a Broker to a territory protected by an ACL:
How a Territory Access Control List Works
In the figure, territory X consists of three Brokers, A, B, and C, that are controlled by their respective Broker Servers A, B, and C. The basic authentication identities or SSL identities for each of the Broker Server's controlling Brokers A, B, and C are listed in the ACL for territory X. For Broker Z (belonging to Broker Server Z) to join territory X, its identity (shaded DN in the ACL), which is the same as that of Broker Server Z, must be added to the territory ACL.
For information about configuring territory ACLs, see
About Controlling Which
Brokers Can Join a Territory.