Blocking Incoming Requests to Green Zone
While configuring reverse invoke, you must ensure that you block any requests coming to either API Gateway or the Integration Server present in the green zone.

To block the requests to green zone
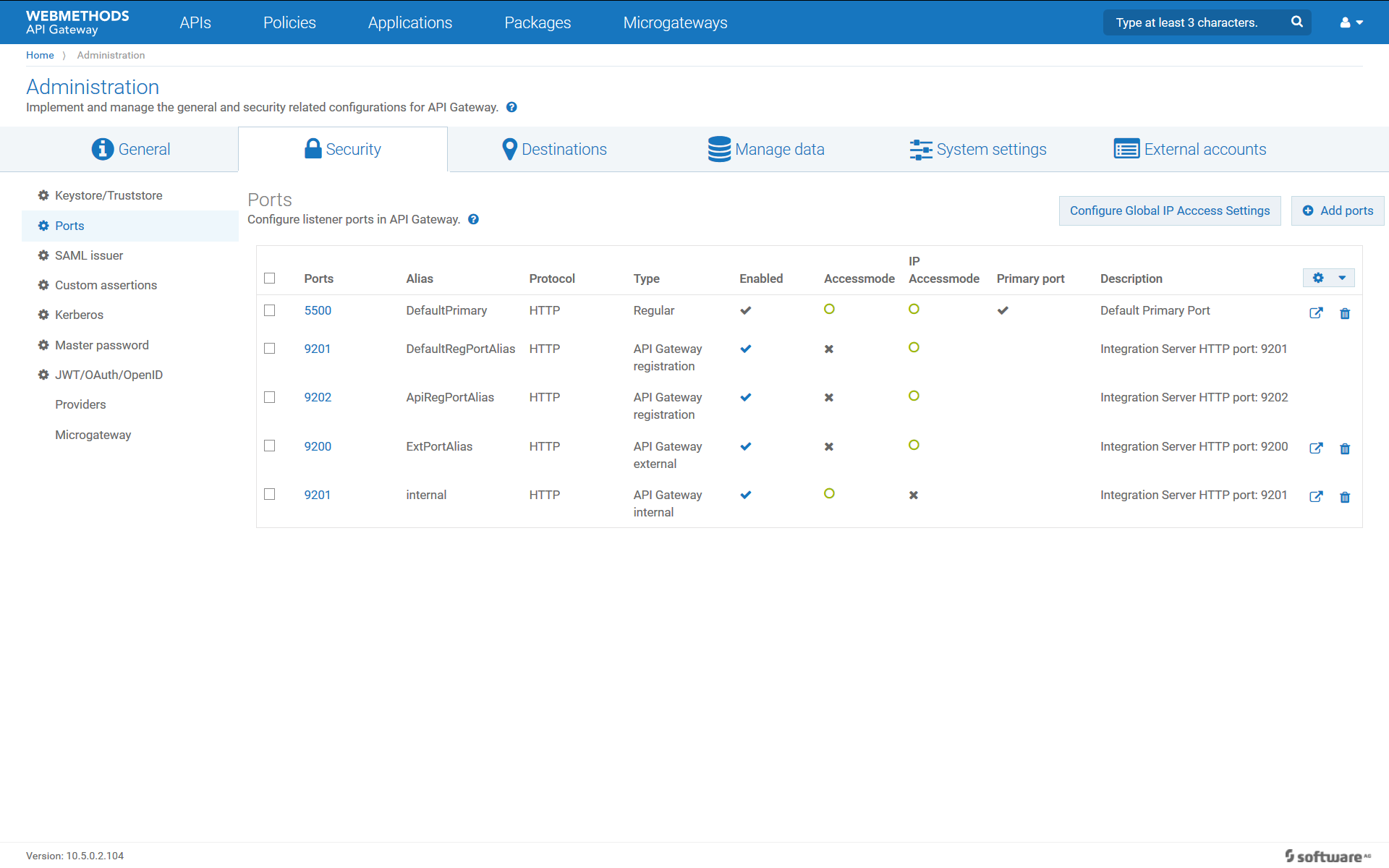
1. Configure the ports in API Gateway located in DMZ as follows.
With the above configuration, the API Gateway instance in DMZ receives requests on the external port ExtPortAlias. These requests are forwarded to the registration port DefaultRegPortAlias. DefaultRegPortAlias is connected to an API Gateway internal port that is defined on the DMZ API Gateway. This ensures that requests are not forwarded to the Integration Server or API Gateway in the green zone, but processed within the DMZ API Gateway. The default registration port is the first one defined for an external port. There is no specific naming required.
To forward API requests to the backend services, the API routing policies must point to the ApiRegPortAlias, the second registration port alias defined for the external port.
2. Configure the routing policies in the API Gateway instance located in DMZ, as follows.
The endpoint URI of the Straight Through Routing policy leverages the apigateway scheme and references the ApiRegPortAlias. The resource path of the endpoint URI points to the sample flow service employee running on the green zone Integration Server. As mentioned above, this flow service can not be invoked directly from the DMZ external port. All non-API requests are routed to the internal port of the DMZ API Gateway where the backend flow services are not defined.
3. Configure the internal port of the Integration Server as follows.