How Do I Secure API Gateway Server Communication with Backend Services?
Secure API Gateway server to enable secure communication with the backend services over HTTPS.
You must have API Gateway administrator privileges to perform this operation.
To configure API Gateway server for secure communication with Backend Services
1. Locate the keystore and truststore files in the file system.
The default keystore and truststore files are available in the Installation_Dir\common\conf folder.
2. Configure keystore and truststore in the API Gateway UI.
You require a keystore alias for configuring an HTTPS port in API Gateway. You require the truststore alias for validating backend service certificates.
a. Log on to API Gateway.
b. Navigate to Administration > Security > Keystore/Truststore.
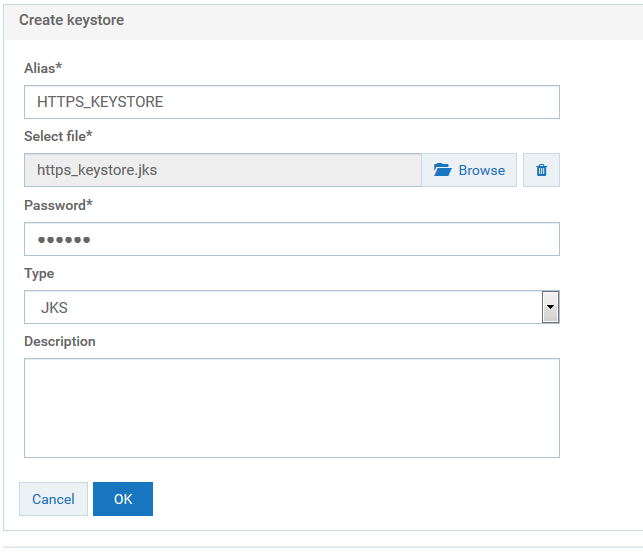
c. Click Add keystore.
d. Provide the following details:
 Alias
Alias. A text identifier for the keystore file. The alias name can contain only alphabets, numbers and underscores. It cannot include a space, hyphen, and special characters.
 Select file
Select file. Browse and select the file https_keystore.jks file located at
Installation_Dir\common\conf.
 Password
Password. Specify the password for the saved keystore file associated with this alias.
 Type
Type. Specify the certificate file format of the keystore file, which, by default, is JKS for keystores.
e. Click OK.
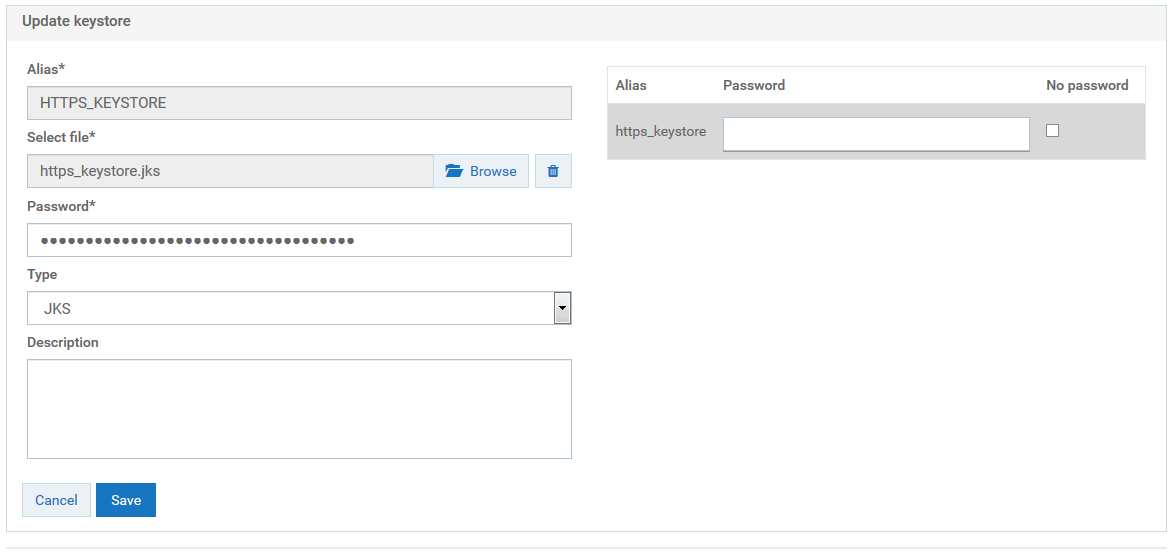
A warning appears, prompting you to create a password for the key alias.
f. Close the warning dialog box.
The Update keystore dialog box appears.
g. Provide the password for the https_keystore file, for example, manage.
h. Click Save.
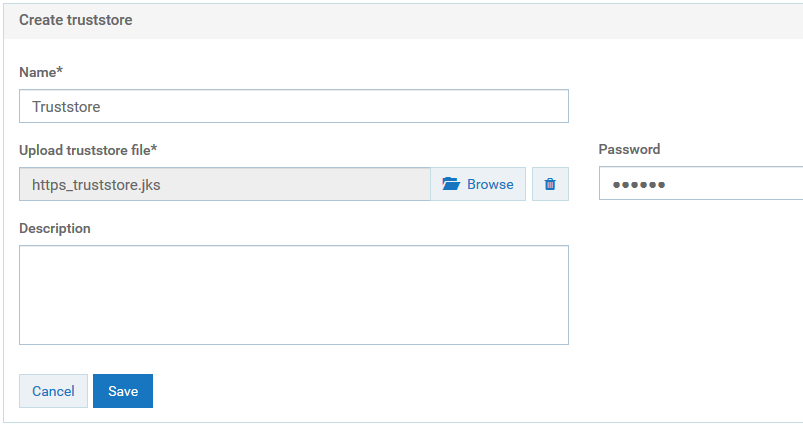
i. Click Add truststore.
j. Provide the following details.
 Name
Name. A name for the truststore file.
 Upload truststore file
Upload truststore file. Browse and select the https_truststore.jks file located at
Installation_Dir\common\conf.
 Password
Password. Specify the password that is used to protect the contents of the truststore, for example,
manage.
k. Click Save.
3. To communicate securely with the backend services you have to configure the keystore and truststore settings for outbound connections. This can be configured in one of the following ways:

Globally, you can configure the keystore and truststore settings for outbound connections in
Administration >
Security configuration section as follows:
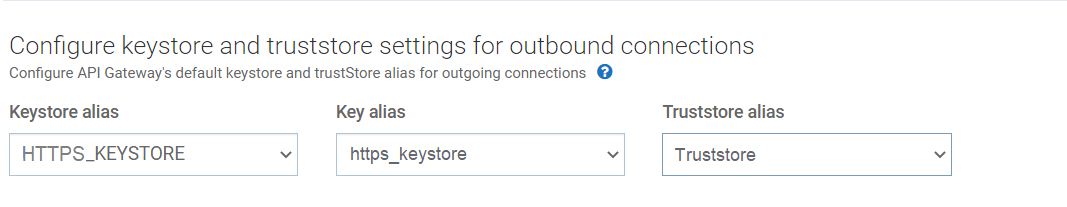
1. Navigate to Administration > Security > Keystore/Truststore.
2. In the Configure keystore and truststore settings for outbound connections section, provide the keystore and truststore aliases for securing outgoing SSL connections. The keystore and key alias are required for outgoing two-way SSL connections.

At an API-level, you can configure the keystore and truststore in the following ways:

Through an endpoint alias configured in the routing policy:
1. Create an endpoint alias where you specify the default URI, and the keystore and truststore for the backend service. For details about creating an endpoint alias, see
Creating an Endpoint Alias.
2. Specify the endpoint alias in the
Endpoint URI field in the routing policy properties section when you configure the policy. For details, see
Routing.

Through a routing policy by specifying the URI of the backend service endpoint, and the keystore and truststore. For details, see
Routing.
Note:
The global keystore and truststore configuration is the default configuration that applies for all APIs if there is no keystore or truststore configured through an endpoint alias or a routing policy at an API-level.
You now have a secure communication channel established between the API Gateway server and the backend services.