How do I enforce PKCE at application level?
This section explains how to enforce PKCE at an application level in the local authorization server. When you enforce PKCE at an application level, it is enforced only for that application.

To enforce PKCE at an application level
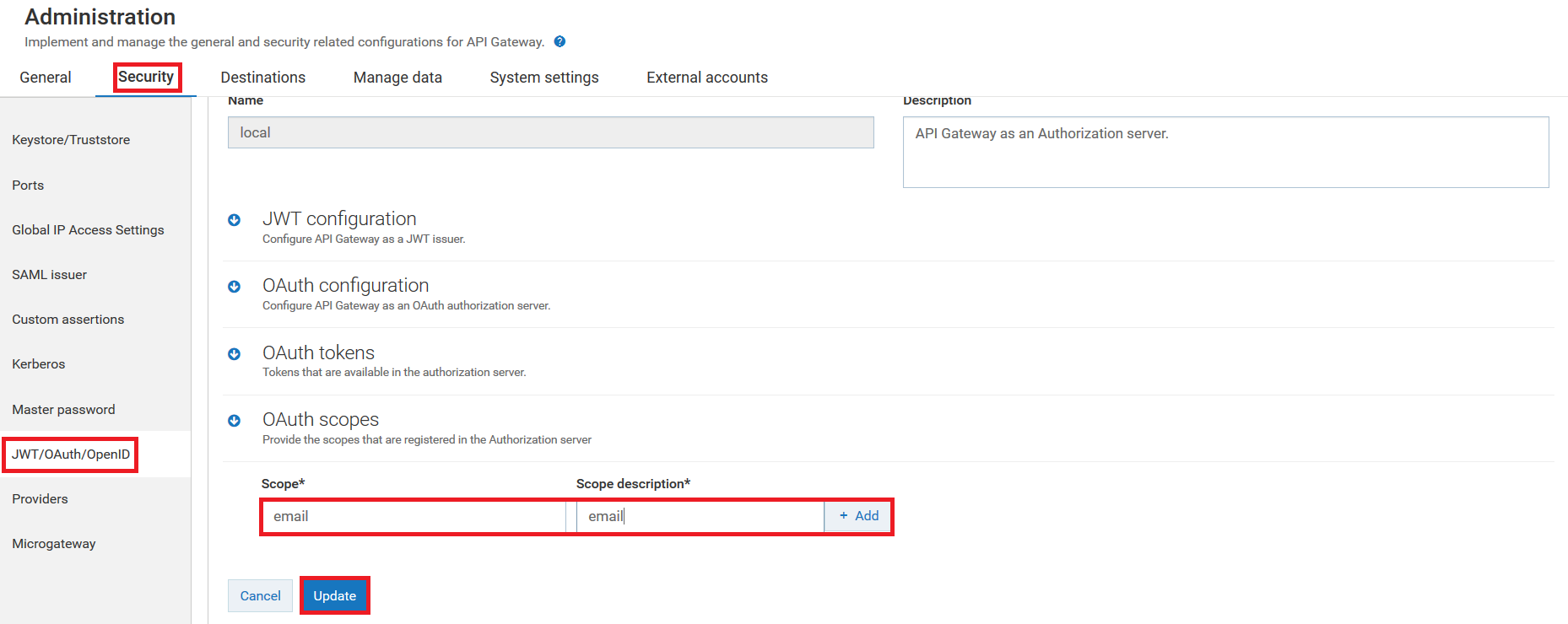
1. Create OAuth scope in the local authorization server.
2. Create a new application or update an existing application with OAuth2 authentication strategy.
For details about creating an application, see
Creating an Application.
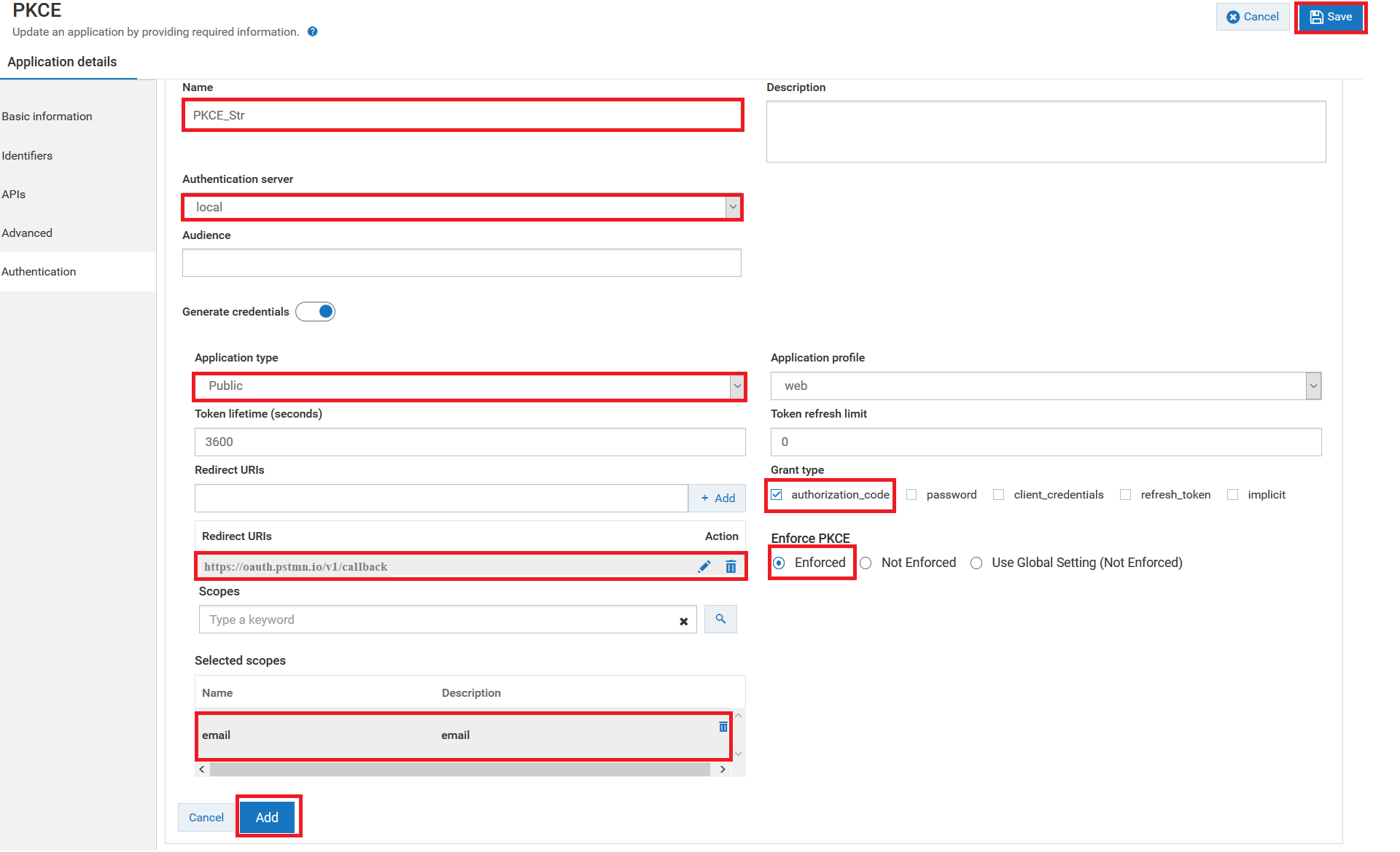
3. Open the application and click the Authentication to create a strategy with OAuth2 authentication.
Make sure you have selected the following mandatory fields for this use case:

Select the
Authentication schemes as
OAUTH2.

Specify the
Authentication server as
local.

Select the
Application Type as
Public.

Specify the grant type to be used to generate the credentials. For this specific use case, you must select authorization_code, which is dynamically populated from the authorization server.

In the
Enforce PKCE section, select one of the following:
PKCE Settings | Description |
Enforced | If you select this option, the local authorization server enforces PKCE even if the PKCE is not enforced at the global level. |
Not Enforced | If you select this option, the local authorization server does not enforce PKCE even if the PKCE is enforced at the global level. |
Use Global Setting (Enforced) | If you select this option, the local authorization server enforces PKCE based on the PKCE setting at the global level. Note:
The value inside the parenthesis depicts whether you have enforced the PKCE at the global level or not. |
Note:
The application level PKCE enforcement takes precedence over the global level PKCE enforcement.

Specify the postman
https://oauth.pstmn.io/v1/callback URL as redirect URI.

Specify the OAuth scope that you have created for the local authorization server in Step 1.
4. Click Add to save the strategy.
5. Click Save to update and save the application.
Once you enforce PKCE, you get access token only on successful validation of code verifier.