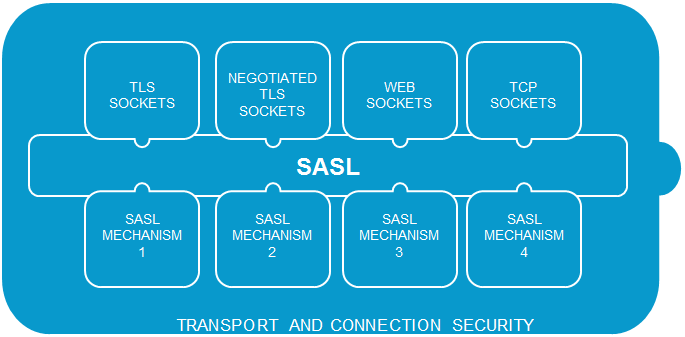
Transport and Connection Security
AMQP defines the following with regard to Transport and Connection Security layers:
TLS/SSL Socket
The node that accepts the connection uses a dedicated TLS port (Default 5671). The node that initiates the connection needs to successfully establish a TLS session before any AMQP traffic is exchanged.
Note:
In Universal Messaging, the node that accepts the connection is the UM realm which needs to use an NSPS Interface. See the section
NSPS Ports in the
Administration Guide for related information.
Negotiated TLS
The node that accepts the connections uses a single port for plain TCP & TLS sockets. The node that initiates the connection indicates the desire for TLS using a protocol flag, followed by AMQP traffic and upgrade of streams to TLS.
Note:
Universal Messaging does not currently support Negotiated TLS for AMQP 1.0.
WebSockets
The node that accepts the connections uses a dedicated TCP or TLS port. The node that initiates the connection requests a WS upgrade, followed by AMQP traffic. For more information check the
AMQP over Websocket binding, described on the OASIS web site
https://www.oasis-open.org/org.
Note:
Universal Messaging does not currently support the AMQP over WS/S draft. There are plans for support in a future product release.
TCP Sockets
The node that accepts the connection uses a dedicated TCP port (Default 5672).
NOTE: In Universal Messaging, the node that accepts the connection is the UM realm which needs to use an NSP Interface (see
Native Communication Protocols for information about NSP).
SASL
AMQP optionally allows support for SASL authentication. The node that accepts the connections can use a TCP or TLS port and negotiate a SASL mechanism using a protocol flag. The node that initiates the connection needs to negotiate a SASL mechanism.
Note:
In Universal Messaging, the node that accepts the connections is the UM realm using an NSP or NSPS interface respectively. Universal Messaging SASL support is restricted by the underlying JVM SASL restrictions with regard to mechanisms supported.
See the section
Administering TCP Interfaces, IP Multicast, and Shared Memory in the
Administration Guide for information about interfaces.
Note:
In Universal Messaging, using SASL authentication only makes sense if authentication is enabled on the UM realm (see
Using SASL for related information).