Creating an SSL-Enabled Interface
To add an SSL-enabled interface using the Enterprise Manager, first create an nsps or nhps interface as described in
Creating Interfaces.
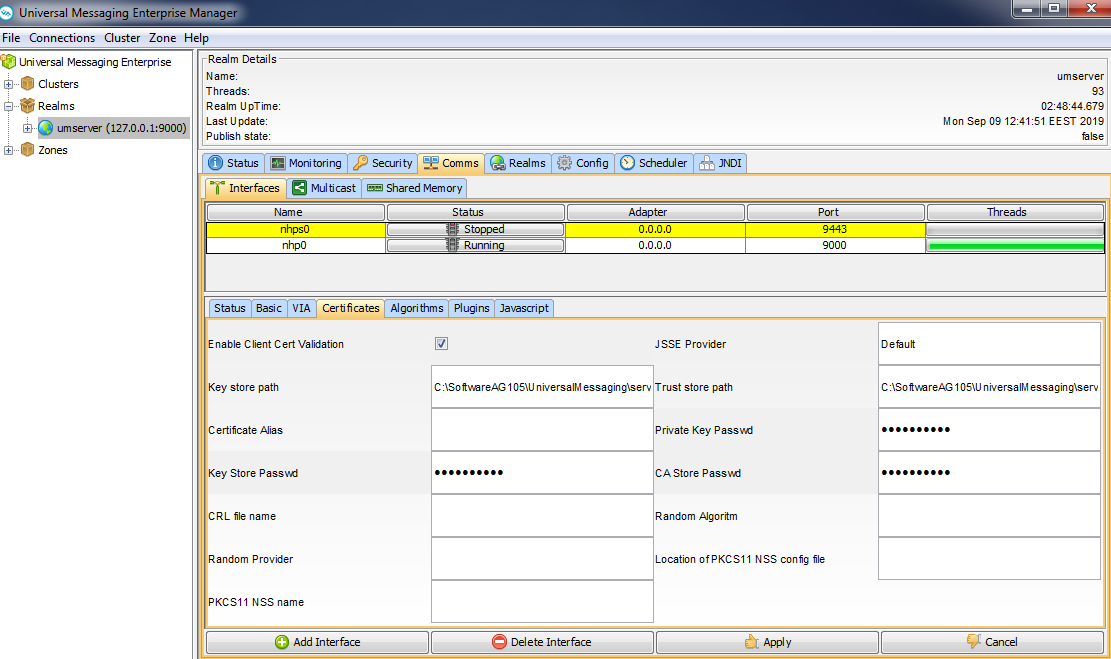
The following image shows an nhps (HTTPS) interface listening on port 9443.
Click the
Certificates tab. The values for the
Key store path and
Trust store path fields are specified by default. Universal Messaging provides a utility called Certificate Generator that can generate sample .jks files containing certificates bound to localhost, for the server, the client, and the truststore used by JSSE. The example uses the sample jks files to show how to create an SSL interface. For detailed information about generating certificates, see
How to Generate Certificates for Use.
The Key store path field must contain something similar to:
c:\SoftwareAG_directory\UniversalMessaging\server\umserver\bin\server.jks
which is the path to the sample Java keystore for the server, bound to localhost.
The Trust store path field must contain something similar to the following:
c:\SoftwareAG_directory\UniversalMessaging\server\umserver\bin\nirvanacacerts.jks
Then specify the value password for Key Store Passwd and CA Store Passwd. This is the password for both the server keystore and the CA (truststore) keystore.
Next, go to the Basic tab and select the Autostart Interface option to start the interface automatically when the Universal Messaging realm server starts.
Note:
If you intend to use an SSL interface for inter-realm communication, you should ensure that the
Allow for InterRealm option is selected and the
Allow Client Connections option is cleared. Alternatively, if you intend to use an SSL interface for communication between clients and the realm, you should ensure that the
Allow for InterRealm option is cleared and the
Allow Client Connections option is selected. For information about inter-realm communication, see
Setting Up Inter-Realm Communication.
Click Apply to save your changes and start the interface. If the network interface fails to start, inspect the Universal Messaging log file.
There is no limit to the number of network interfaces that can be added to a realm and each can have its own configuration, such as SSL chains, applied. This enables you to isolate customers from each other while still using only one Universal Messaging realm server.
The sample Java keystores work only when you use the loopback interface of your realm server host. If you want to provide SSL capabilities for remote connections, you must have your own keystores and valid certificate chains.
Connecting to an NHPS Interface
To connect to an nhps interface on a Universal Messaging server in the Enterprise Manager, you configure the following truststore and client keystore properties in the Software AG_directory \UniversalMessaging\java\instance_name\bin\Admin_Tools_Common.conf file of the server:
 set.default.CKEYSTORE=<path_to_client_keystore>
set.default.CKEYSTORE=<path_to_client_keystore> - Required only when client authentication is enabled.
 set.default.CKEYSTOREPASSWORD=<keystore_password>
set.default.CKEYSTOREPASSWORD=<keystore_password> - Required only when client authentication is enabled.
The certificates must be in .jks (java keystore) or PKCS12 format.
If you choose not to specify a client keystore certificate and а kesystore password, you must comment out these properties using a hash (#) in the nenterprisemgr.conf and Admin_Tools_Common.conf files.
Important:
If you have these properties configured both in the Software AG_directory \UniversalMessaging\java\instance_name\bin\nenterprisemgr.conf file and Admin_Tools_Common.conf file, the values in nenterprisemgr.conf override the values in Admin_Tools_Common.conf. Software AG recommends that you configure the properties in the Admin_Tools_Common.conf file.
In addition, optionally, you can configure an nhps url to which clients connect by default. You specify the url as a value of the -DRNAME property in the nenterprisemgr.conf file of the server, for example:
wrapper.java.additional.3=-DRNAME=nhps://umserver:8000
When you connect an NSPS client to an NSPS or NHPS interface, you must consider the following. The Java Client API implementation of the NSPS protocol does not support RFC 6125, which means that the client does not perform hostname validation against the list of "Subject Alternative Names" specified in the keystore of the server. This limitation exists because of a dependency on the JAVA JSSE and SSLSocket, which can only validate the hostname when using the HTTPS protocol.
Enabling Client Authentication
You use the Enable Client Cert Validation check box on the Interfaces > Certificates tab to enable or disable client authentication for an nhps or an nsps interface on a Universal Messaging server. If you enable client authentication, you must specify the client keystore certificate and kesystore password as properties in the nenterprisemgr.conf or the Admin_Tools_Common.conf file of the server instance.