Connecting to Prometheus with Security enabled in TMC
To connect to the Prometheus endpoint with Security enabled in TMC, follow these steps:
1. Navigate to the TMC web application and add a connection to the TSA cluster. The name of the connection should be the value of the cluster_name label. /tmc/api/prometheus starts returning Prometheus metrics.
2. When you
enable user authentication in TMC, all the endpoints on TMC become password protected. In order for Prometheus to access the /tmc/api/prometheus endpoint, you need to enable basic authentication for the endpoint. Use the following steps to do so: a. Open the shiro.ini file located under your user account path. For Windows it could be at C:\Users\<username>\.tc\mgmt\shiro.ini, for Linux - ~/.tc/mgmt/shiro.ini.
b. If it is missing, in the shiro.ini file under section [main] add basicAuth = com.terracotta.management.security.shiro.web.filter.TCBasicWithFormFallbackAuthenticationFilter.
c. Under section [urls] add /api/prometheus = basicAuth. Refer to the
Apache Shiro Web Support for more details. Use the following image for reference: 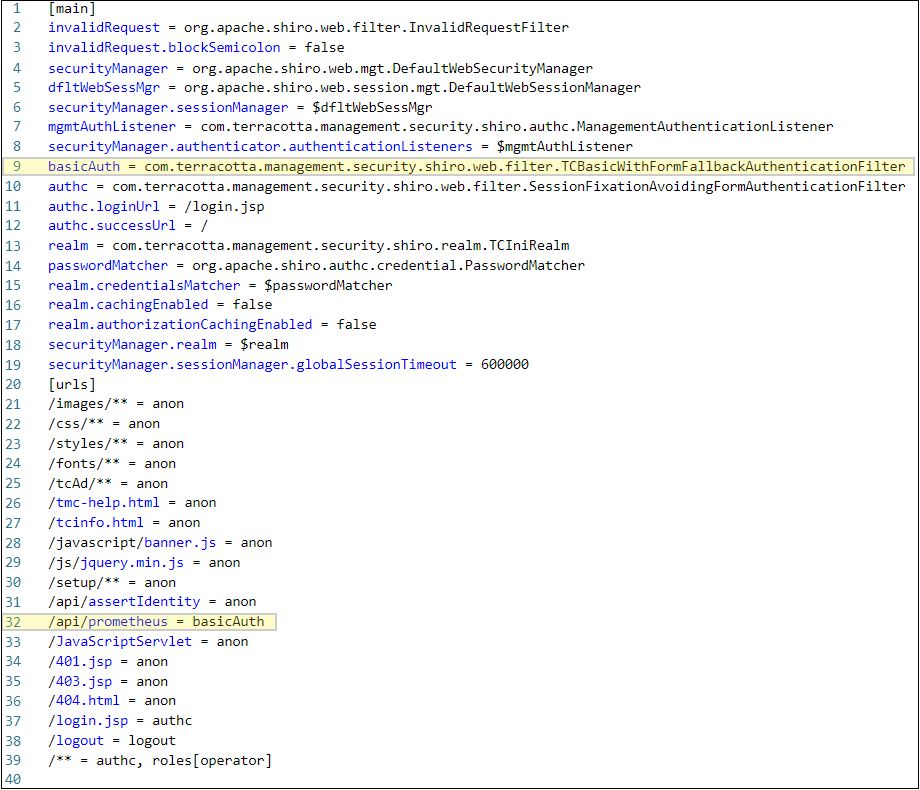
Note:
Make sure to add this segment before /** = authc, roles[operator] as the order of URL path expressions matters where the first match will win.
d. Restart TMC for the changes to take effect.
e. Before adding it in Prometheus, you can test the endpoint with a command line tool curl or a graphical tool like Postman. For example:
curl -u "<username>" <tmc-prometheus-endpoint>
3. If SSL is enabled on TMC, you need to export its certificate and provide it to the Prometheus configuration file. To do that either you can use the command line tool keytool or the graphical tool
KeyStore Explorer. For example: keytool -exportcert -alias <tmc-alias>
-keystore <tmc-keystore> -rfc -file <tmc-cert>
4. Add the details to the prometheus.yml configuration file. Refer to the
Prometheus Configuration page for more information. A sample configuration looks like this: - job_name: 'big_memory'
scheme: https
metrics_path: /tmc/api/prometheus
static_configs:
- targets: ['localhost:9443']
basic_auth:
username: <username>
password: <password>
tls_config:
ca_file: <path-to-tmc-certificate>
where <username> and <password> are the user's username and password, and <path-to-tmc-certificate> is the valid file path to the TMC certificate.


