Defining the Authentication Scheme
Authentication against LDAP determines if a distinguished name exists for a user. This searches for a user entry based on a specific username. Search-based authentication works, for example, if user names are users' email addresses.
To define the authentication scheme:
1. If needed, log into Presto Hub and click  Admin Console in the main menu.
Admin Console in the main menu. 2. Expand Presto Repositories and click User Repository - LDAP.
3. Click Advanced Options.
4. Set these properties in the Authentication Properties section:
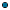 User Search Base
User Search Base = the base context for a user search in authentication. This produces a list of all users which is filtered with a combination of the User Search Filter and User Search Subtree properties to authenticate a user. For example:
ou=People
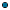 User Search Filter
User Search Filter = the relative filter to apply to search for users during authentication. The variable
{0} is replaced with the user's username from login.
This filter is based from the context defined in User Search Base. For example:
email={0}
Note: | This attribute must be the same attribute used in the User ID Attribute Name property. |
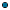 User Search Subtree
User Search Subtree = set this option if the search should be recursive through all levels of the Directory under the search base. If you clear this option, search only checks direct children of the search base.
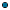 Use LDAP VLV Control for Sorting and Paging
Use LDAP VLV Control for Sorting and Paging = this option is set by default to allow
Presto to use
virtual list views (VLV) to paginate and sort LDAP search results.
Most LDAP directories support VLV, so in most cases you can leave this option set. If your LDAP directory logs errors for "unsupported search control", you can use this option to turn VLV off.
 User ID Attribute Name
User ID Attribute Name = the LDAP attribute that contains the username that users login with. For example:
email
This value becomes the user ID for all further security contexts, unless the User ID Pattern property is also set.
 User ID Pattern
User ID Pattern = a regular expression that is applied to user login names to extract the user ID for all further security contexts. This is only applied after authentication occurs.
 Admin Console in the main menu.
Admin Console in the main menu.