Security Requirements for Apama
Security model
The Apama security model for correlator and IAF components is that untrusted users must not be given access to any related files or to send or receive data on any of the correlator or IAF network ports. For dashboards, the same applies to the display server's management and data ports, and the data server's management port - although the data server's data port might need to be exposed to end-users if the thick Dashboard Viewer client is used. It is assumed that any user able to access these files or ports is trusted and has permission to make arbitrary changes and read arbitrary data. Such users are also permitted to inject arbitrary code into a correlator and execute it with the permissions of the correlator process.
Security requirements
You must use standard operating system and network tools/configuration to restrict access to the IAF and correlator components to only trusted users. For the dashboard servers, this applies except to the data server's data port.
You must use standard operating system tools to restrict access to all configuration and data files to only trusted users.
You must restrict access to changing the process environment when starting the server processes to only trusted users.
You must not set the correlator, IAF or dashboard server logging to a level higher than INFO to have all security-relevant events logged to the log files.
Setting the correlator, IAF or dashboard server logging to a level lower than INFO could include security-sensitive information in the log files.
If components must connect across an untrusted network, then either a standard overlay tool such as a VPN must be used, or the interconnection has to be done via Universal Messaging with appropriate controls and restrictions configured in Universal Messaging.
If you need to restrict the data sent from certain users to the correlator, then all interconnections must be done via Universal Messaging with appropriate controls and restrictions configured in Universal Messaging.
HTTP server
The HTTP server connectivity plug-in provides a REST API for submitting events to the correlator. This exposes another port on the correlator. If deployed in any context where access is not restricted to only trusted users, the HTTP server connectivity plug-in must be configured to use TLS and HTTP basic authentication. It should not be directly connected to the internet. If internet access is required, then the plug-in must be deployed in a DMZ behind a reverse proxy such as Apache or Nginx.
See
The HTTP Server Transport Connectivity Plug-in for detailed information on this plug-in.
Dashboards
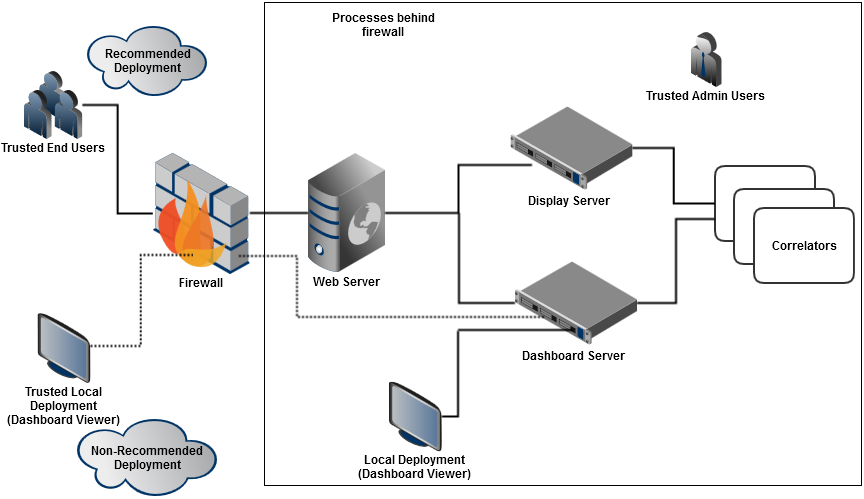
For access from untrusted hosts, you should deploy your dashboards to the web server using either a display server and/or Web Start deployment option. The dashboard server or display server processes should be running behind a firewall, just like the correlators. When accessing the dashboard server by using a standalone Dashboard Viewer outside the firewall, make sure to run the dashboard server with the --ssl option, which will ensure secure sockets for client communication using the data port. You must also ensure that the management ports of both servers are not exposed to end users.
The following diagram depicts the recommended dashboard deployment options:
Authentication for the display server is done via JAAS and your authentication mechanism of choice.
Important: You must customize your own JAAS modules. The out-of-the-box authentication/authorization modules for dashboards cannot be used. This means that there is no authentication by default, and the basic authorization mechanism is shipped. For details on how to configure your own JAAS modules, see
Administering Dashboard Security.
For a dashboard audit trail, you must load the Dashboard Support bundle into the correlator processing audit events and handle the DashboardClientConnected and DashboardClientDisconnected events, logging them in an appropriate manner.